GitHub Under Attack: 100,000+ Fake Repositories Spreading Malware
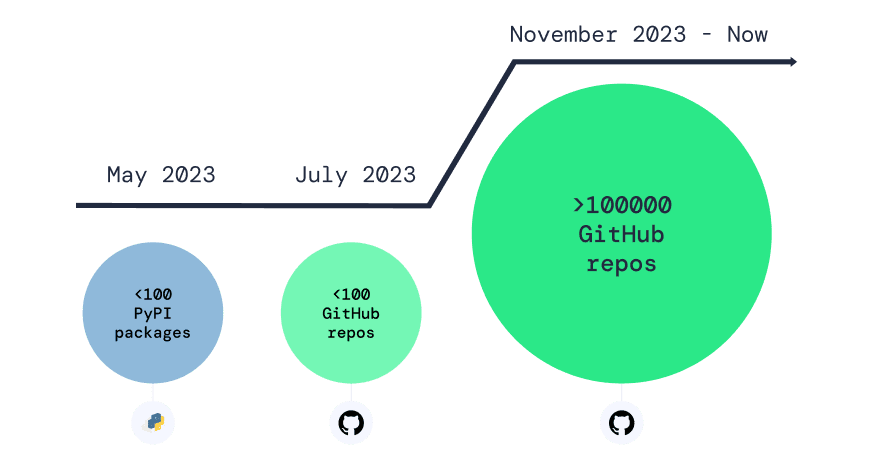
Researchers at Apiiro investigated a widespread campaign of attacks on the GitHub platform using malicious repositories. The experts identified over 100,000 counterfeit repositories, mimicking popular open-source projects to disseminate malware. The number of such repositories continues to grow steadily.
The specialists explained that hackers actively employ a tactic of substituting the names of real projects. They create a repository identical to a popular project on GitHub, with a name that closely resembles the original. Malefactors anticipate that a user will mistype the name during a search and inadvertently download infected code. This method is frequently utilized in conjunction with package managers, where the command line offers fewer opportunities for timely error recognition.
To execute the attack, malefactors clone the target repository, inject it with malicious code, and republish it under the original name. The promotion of such repositories then begins through various internet channels, including forums and social networks, where they are presented as legitimate. Automation of the process allows for the scaling of the distribution of infected projects.
The malicious code on the victim’s computer typically initiates the background download of third-party software. It is noted that malefactors most commonly use BlackCap Grabber—a program that steals credentials, cookies, and other vital information, sending it to the attackers’ servers.
GitHub is taking measures against so-called fork-bombs by automatically monitoring and blocking suspicious repositories with an excessive number of copies. Despite the automated removal of millions of suspicious forks, approximately 1% of infected copies still manage to remain on the platform.
Users are advised to be vigilant and verify the repositories they work with. This is especially important for companies to prevent malicious code from entering their systems and the software supply chain.





