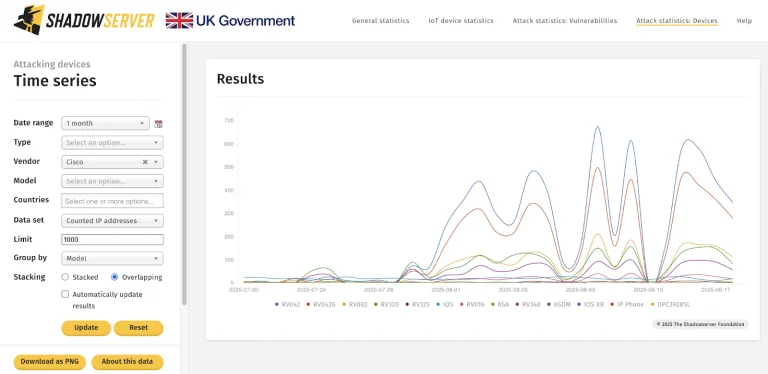
The wave of attacks targeting vulnerabilities in Microsoft SharePoint continues to escalate, reaching levels of sophistication and scale not witnessed since the mass infections orchestrated by LockBit. According to Microsoft, the breaches are attributed to Storm-2603, a threat group with ties to China. Their latest tactic involves deploying the Warlock ransomware onto victim servers following initial access via unpatched flaws—specifically CVE-2025-49706 and CVE-2025-49704. One allows for forged requests, while the other enables remote code execution. In tandem, these vulnerabilities grant adversaries full control over unprotected systems.
The principal entry point is a counterfeit script, spinstall0.aspx, surreptitiously uploaded to vulnerable on-premise servers. This initiates a phased infiltration: beginning with a whoami command to determine privileges, followed by a sequence of cmd.exe executions and batch file deployments. Notably, Microsoft Defender is systematically disabled—service settings are altered via services.exe, and AMSI, the Antimalware Scan Interface responsible for script inspection, is deliberately deactivated.
Once foothold is established, Storm-2603 schedules malicious tasks and alters IIS components to embed .NET libraries, ensuring persistent access even after the initial vulnerabilities are patched. In subsequent phases, the attackers deploy Mimikatz to extract credentials and employ tools like PsExec and Impacket to move laterally across the network.
The climax of the campaign involves modifying Active Directory Group Policies (GPO), through which Warlock ransomware is implanted. Reports also reference LockBit, suggesting the group’s adaptability in leveraging various ransomware strains. Analysts have additionally observed traces of ToolShell, BadPotato, RemoteExec, and AsmLoader— the latter responsible for executing shellcode both within the IIS process and independent tasks.
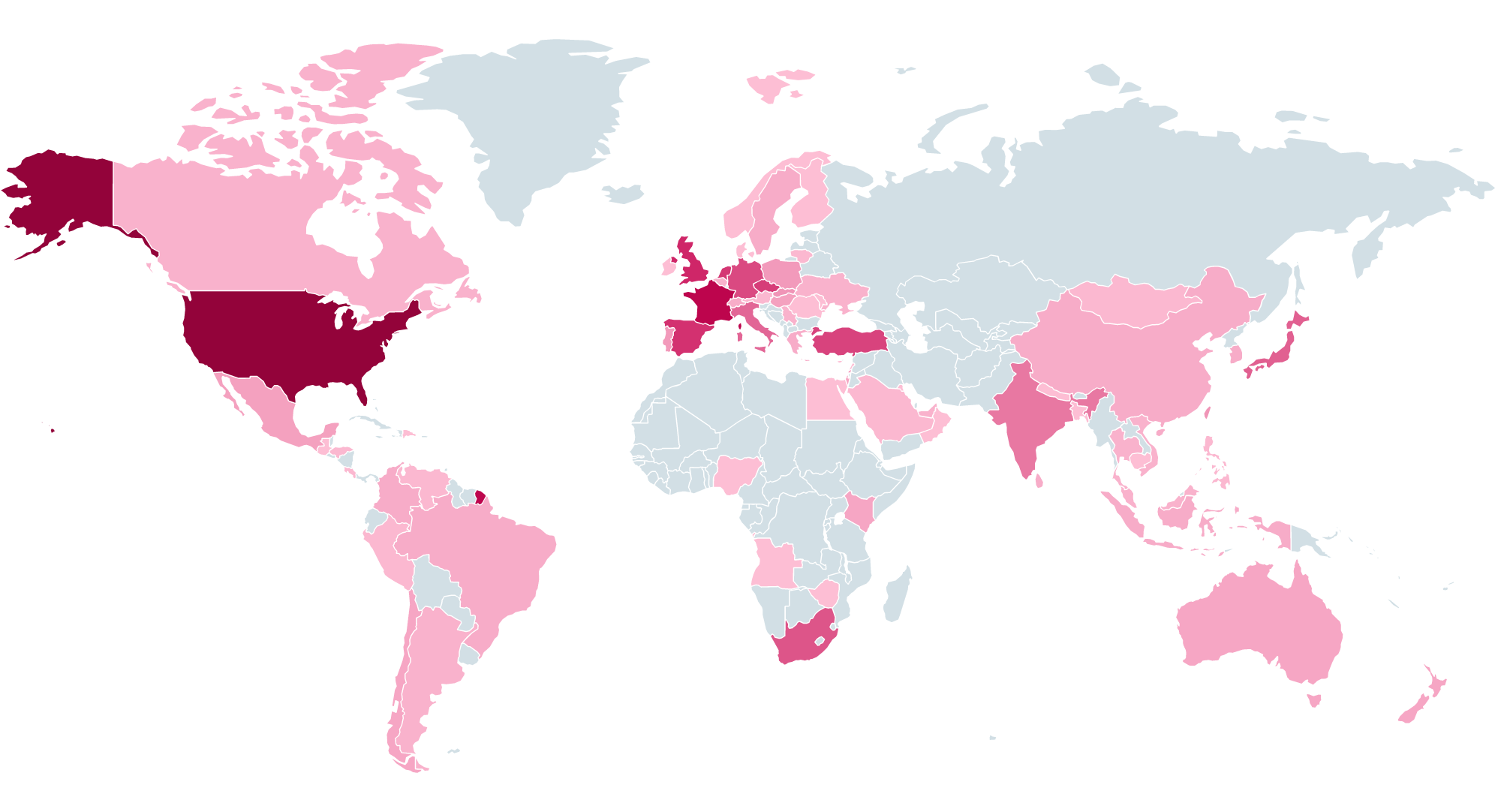
ESET has revealed that the United States accounts for 13.3% of ToolShell-related attacks worldwide. Other affected nations include the United Kingdom, Germany, France, Portugal, and Italy, with targets spanning government bodies and major enterprises. Simultaneously, Check Point reports over 4,600 attempted intrusions across more than 300 organizations globally, affecting sectors such as telecommunications, finance, and public administration. The campaign has also aggressively exploited known vulnerabilities in Ivanti EPMM.
Exacerbating the situation is the attackers’ pursuit of ASP.NET MachineKeys—cryptographic secrets that allow them to regain access even after security patches are applied. Malicious components resembling spinstall0.aspx have been found exfiltrating these keys along with the hostname and current user credentials. According to WithSecure, these tactics mirror a campaign from December 2024, during which similar techniques were deployed by an unidentified actor.
While Microsoft and ESET point to Chinese involvement, no independent confirmation has yet been provided. The Chinese Ministry of Foreign Affairs has categorically denied the accusations, asserting the country’s commitment to combating cybercrime and rejecting allegations lacking substantive evidence.
Amid the ongoing threat, Microsoft urges immediate action: install the latest SharePoint patches, re-enable AMSI, restart IIS, regenerate ASP.NET keys, and verify that antivirus defenses are fully operational. If AMSI cannot be restored, a manual reboot following updates and key regeneration is strongly recommended.
The situation remains fluid. As attack vectors become public, a surge of secondary attacks from less sophisticated threat actors—armed with leaked tools—is anticipated. The battle against SharePoint vulnerabilities is rapidly evolving into a global war of attrition, where a single misstep could compromise an entire network.