Securonix Uncovers RE#TURGENCE: A Campaign Targeting MSSQL Servers in US, EU, and LATAM
Recently, a surge in attacks on poorly protected MS-SQL servers has been observed across the United States, the European Union, and Latin America. Security researchers from Securonix believe this campaign is focused on gaining initial access and is driven by financial motives.
Experts note that any successful attack within this campaign invariably ends either with the sale of access to the compromised host or the delivery of ransomware. The campaign is linked to the activities of Turkish hackers and has been codenamed RE#TURGENCE by Securonix researchers.
Access to MS-SQL servers is achieved through password hacking, followed by the use of the xp_cmdshell configuration option to execute shell commands on the compromised host. This is reminiscent of a previous campaign named DB#JAMMER, which was discovered in September 2023.
Subsequently, a PowerShell script is extracted from a remote server, responsible for downloading a disguised Cobalt Strike payload.
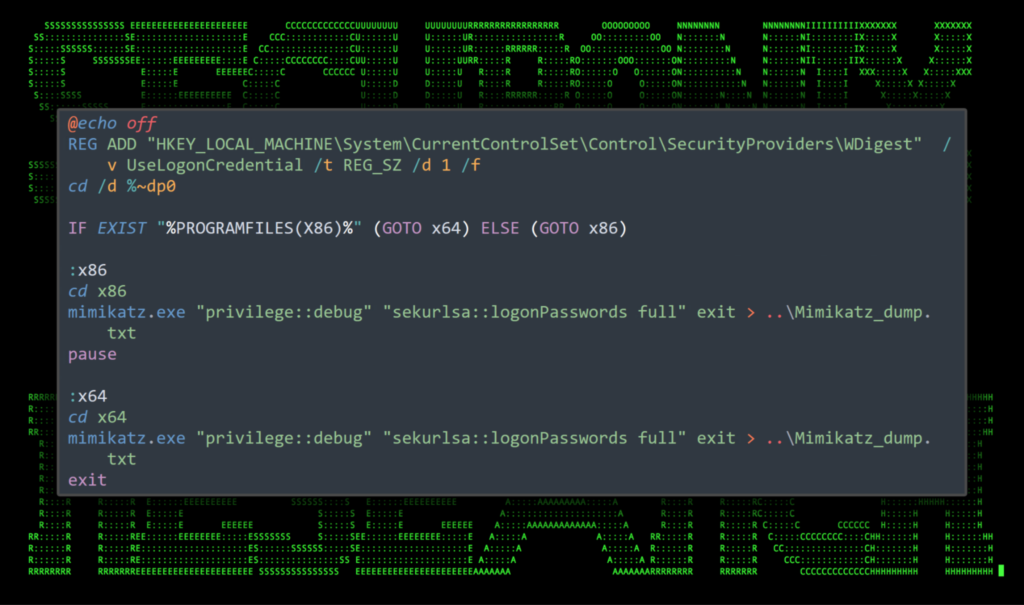
Thereafter, a toolkit is used to download the AnyDesk remote desktop application from a network resource for machine access and downloading additional tools, such as Mimikatz for credential harvesting and Advanced Port Scanner for reconnaissance.
Lateral movement is carried out by hackers using a legitimate system administration utility named PsExec, which can execute programs on remote Windows hosts.
Eventually, the entire chain of attacks leads to the deployment of the ransomware software Mimic, a variation of which was also used in the previous DB#JAMMER campaign.
Securonix specialists emphasize that the indicators and malicious methods used in both campaigns vary significantly, suggesting a high likelihood of their independence from each other.
This is particularly true regarding methods of initial penetration: the DB#JAMMER campaign was somewhat more complex and utilized tunneling, while RE#TURGENCE is more targeted and inclined to use legitimate tools and remote monitoring and management, such as AnyDesk, to blend in with normal activity.
Securonix also discovered an operational security error made by the attackers. This error allowed specialists to track the clipboard activity of the hackers and establish their Turkish origin.
Researchers warn, “Always avoid direct connection of critical servers to the Internet. In the case of the RE#TURGENCE attackers, they were able to hack the server directly from outside the main network.”





