Security Alert: Chinese-Linked Hackers Infiltrate 30% of Cisco Routers
According to a report by SecurityScorecard’s STRIKE team, hackers from the Volt Typhoon group, linked to the Chinese government, have gained persistent access to Cisco RV320/325 routers, discontinued since 2019.
The malefactors exploited two vulnerabilities in the web management interface of Cisco Small Business RV320 and RV325 Dual Gigabit WAN VPN routers, both cataloged in CISA’s Known Exploited Vulnerabilities (KEV):
- CVE-2019-1653 (CVSS score: 7.5): Allows an unauthenticated remote adversary to obtain confidential information due to improper access control to URLs. Cybercriminals exploit this flaw by connecting to the vulnerable device via HTTP/HTTPS and requesting specific URLs. Successful exploitation enables the attacker to download the router’s configuration or detailed diagnostic information.
- CVE-2019-1652 (CVSS score: 7.2): Permits a remote wrongdoer, authenticated and with administrative rights on the vulnerable device, to execute arbitrary commands. This vulnerability stems from improper validation of user-entered data. The cybercriminal can exploit this by sending malicious HTTP POST requests to the vulnerable device’s web management interface. A successful exploit allows the criminal to execute arbitrary commands in the Linux base shell as the root user.
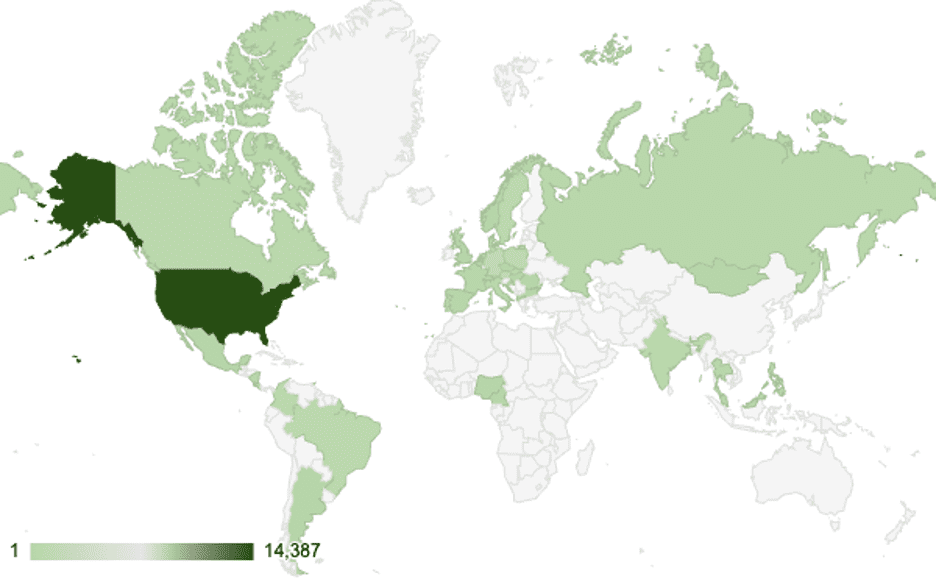
Geographical distribution of possibly infected Cisco RV320 devices by count of connections to C2 router nodes
The vulnerabilities affect RV320 and RV325 devices with firmware version 1.4.2.15–1.4.2.20. A full fix was released in firmware version 1.4.2.22, but not all administrators have paid due attention to updating outdated devices.
STRIKE estimates that hackers compromised about 30% of the devices within 37 days. The team observed frequent connections between compromised devices and Volt Typhoon’s infrastructure from December 1, 2023, to January 7, 2024, indicating a highly active presence.
Researchers also discovered web shells on the hacked routers, installed by hackers for further system control. Signs indicate that the Volt Typhoon is preparing new infrastructure for attacks on U.S., UK, and Australian government assets.
The researchers also point to Volt Typhoon’s active preparations for new attacks, including targets in the U.S. and among allies. They identified a connection of 325 out of 1,116 potential targets with IP addresses previously identified as proxies used by the Volt Typhoon.
Experts believe the success of this campaign is linked to the attackers targeting outdated equipment, often neglected. Such attacks could become a popular trend in the cybercriminal community.





