Razer Synapse software has vulnerability, users can obtain system permissions within minutes
Razer Synapse software has a zero-day vulnerability. Anyone who owns a Razer mouse or keyboard can obtain the system permission within a few minutes.
If someone doesn’t know what Razer Synapse software is, Razer Synapse software is a peripheral adjustment software owned by Razer. It will be automatically downloaded after the player connects to the Razer mouse. Players can set functions such as mouse macros on it. Because Razer mouse or keyboard is also a very popular product, so many players are using them.
Recently, a security researcher @j0nh4t discovered that the automatic download of Razer Synapse software and the ability to select the installation path will become a vulnerability, allowing users to quickly obtain system administrator permissions on Windows system computers.
Need local admin and have physical access?
– Plug a Razer mouse (or the dongle)
– Windows Update will download and execute RazerInstaller as SYSTEM
– Abuse elevated Explorer to open Powershell with Shift+Right clickTried contacting @Razer, but no answers. So here's a freebie pic.twitter.com/xDkl87RCmz
— ҉j҉o҉n҉h҉a҉t҉ (@j0nh4t) August 21, 2021
According to the demonstration of BleepingComputer, the exploit method of this vulnerability is relatively simple. As long as the player connects the mouse to the computer, the system will automatically download the Razer Synapse software. As Razer Synapse’s installation program is executed through a program with Windows system permissions, Razer Synapse’s installation program itself will also obtain system permissions. When Razer Synapse completes the download, the installer will ask the user to select a specified installation path. At this time, if the user receives the Shift key and presses the right mouse button in the window for selecting the path, the user can see an option to “open the PowerShell window here”.
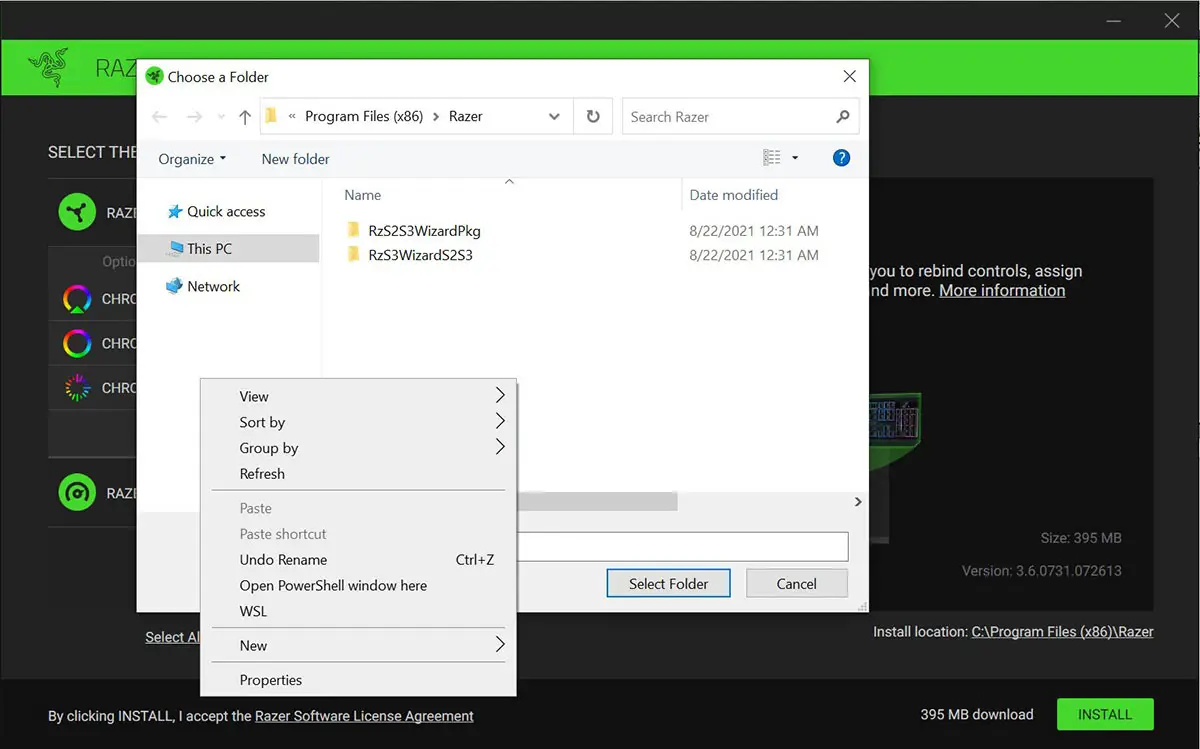
Since the Razer Synapse installer has system permissions at this time, the PowerShell opened at this time also has system permissions.

In fact, it’s not just Razer Synapse. Vulnerabilities such as launching automatic installation with system privileges have actually appeared in other programs that are also Windows plug-and-play. So this is also a relatively common problem.





