Putty and WinSCP Downloads Compromised: Malicious Ads Target Corporate Users
Cybercriminals have devised a sophisticated scheme to infect corporate networks with malware. They place advertisements in search engines like Google that link to downloads of popular Windows utilities. However, instead of legitimate programs, victims receive malicious files.
According to a report by the cybersecurity company Rapid7, attackers placed Google ads promoting fake download sites for Putty and WinSCP. Putty is a popular SSH client, and WinSCP is used for secure file transfers via SFTP and FTP protocols. These programs are widely used by system administrators, making them valuable targets for hackers.
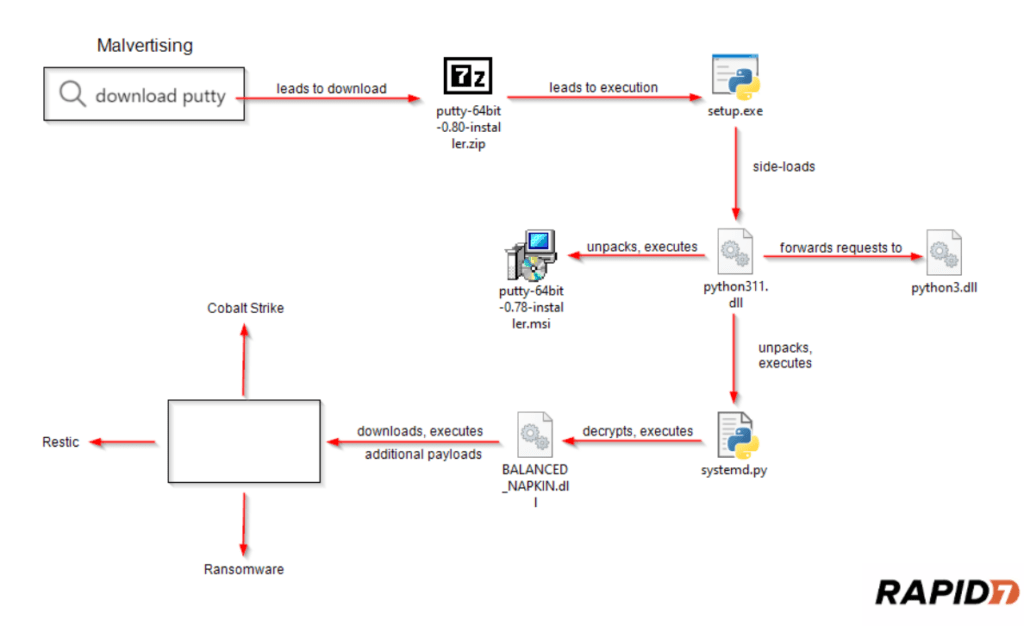
Simplified overview of the attack flow
The advertisements contained links to websites with domain names that closely resembled legitimate resources, such as puutty.org and vvinscp.net, along with other typographical variants. When users clicked on the ad links, they were prompted to download a ZIP archive purportedly containing the desired software.
However, instead of the actual utilities, the archive contained a malicious executable file named Setup.exe, disguised as a Python installer. Running this file triggered a complex mechanism to inject malicious code through a DLL Sideloading vulnerability. The attackers replaced the legitimate python311.dll library with their malicious version.
The downloaded malicious DLL unpacked and executed an encrypted Python script, installing the dangerous remote access tool Sliver. With this tool, hackers could deploy other malicious utilities, such as the Cobalt Strike backdoor.
Once they gained initial access to the corporate network, the attackers stole confidential data, attempted to gain full control over the domain controller, and ultimately deployed ransomware to encrypt the victim’s files.
Rapid7 experts noted similarities between this campaign and recently tracked attacks involving the BlackCat/ALPHV ransomware, which was neutralized last year. However, the specific ransomware family used in this case was not disclosed.
The use of fake search engine advertisements to distribute malware, known as malvertising, has become widespread in the past few years. Cybercriminals have placed ads for software like CPU-Z, Notepad++, Grammarly, μTorrent, Dashlane, and many other well-known programs.
Recently, hackers purchased an ad with the legitimate URL of the cryptocurrency exchange Whales Market, but the link led to a phishing site designed to steal cryptocurrency from visitors. Thus, this scheme poses a serious threat to both businesses and individual users.
Experts advise caution when following third-party download links, even if they are advertised on popular search engines. The preferred method remains downloading software only from the official websites of the developers.





