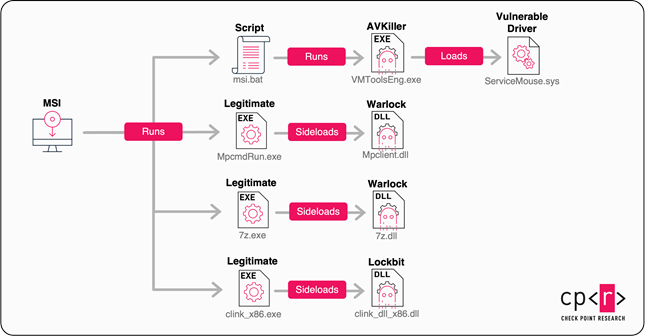
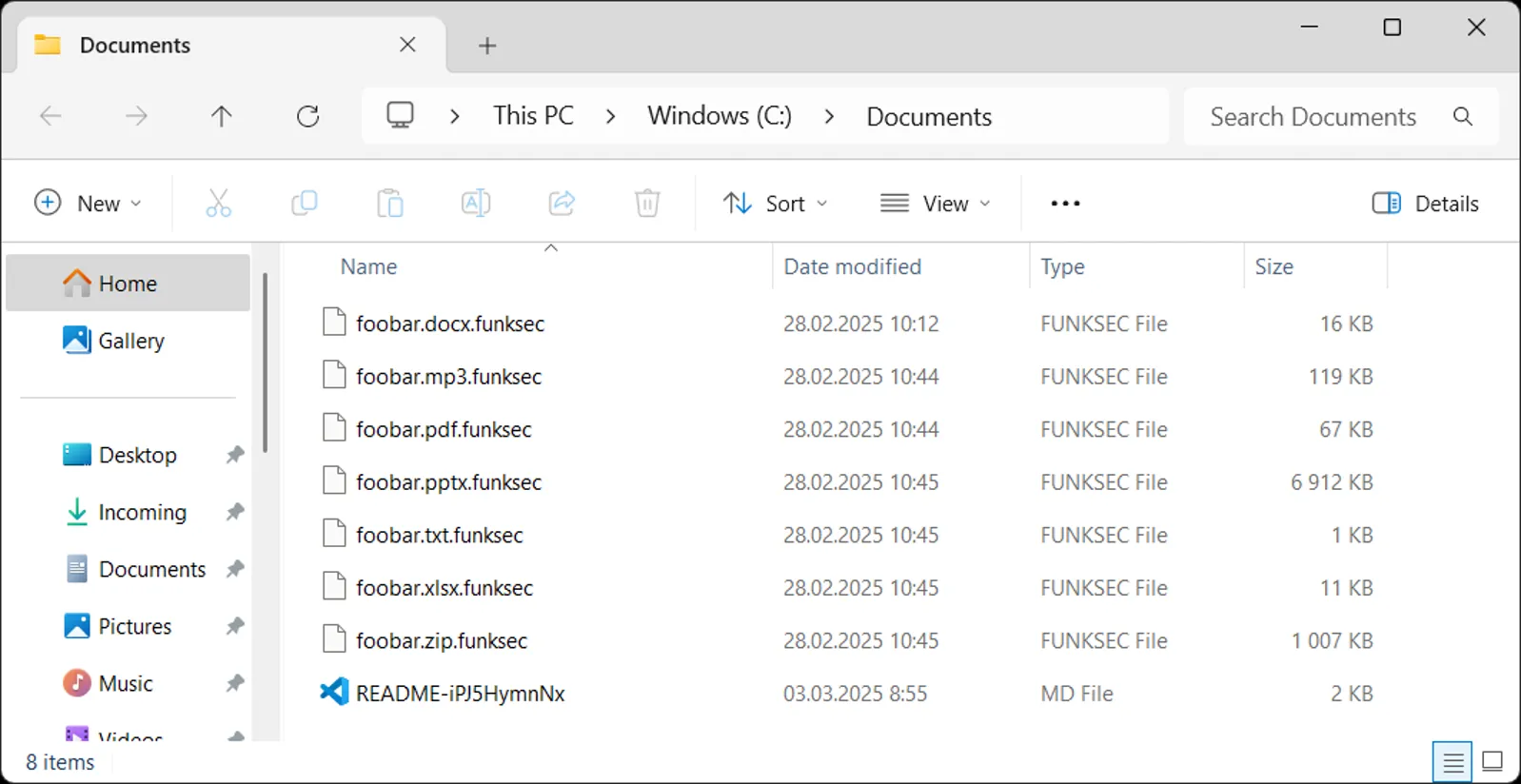
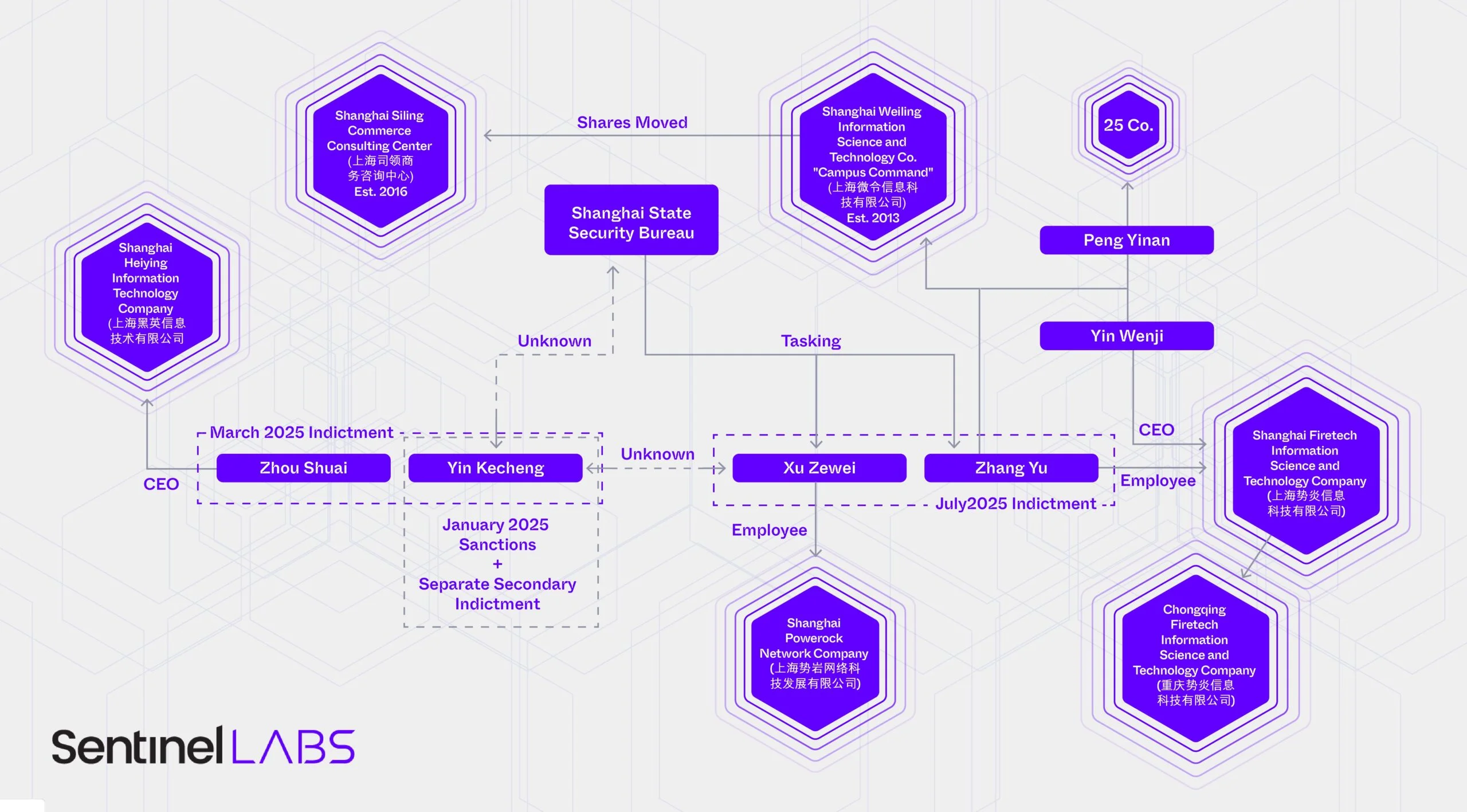
Storm-2603 Unleashes Warlock & LockBit Ransomware with Custom AK47 C2 Framework
Attacks linked to the Storm-2603 group continue to raise serious concerns within the cybersecurity community. This relatively obscure yet well-documented group, reportedly associated with China, has been implicated in the exploitation of recently discovered...