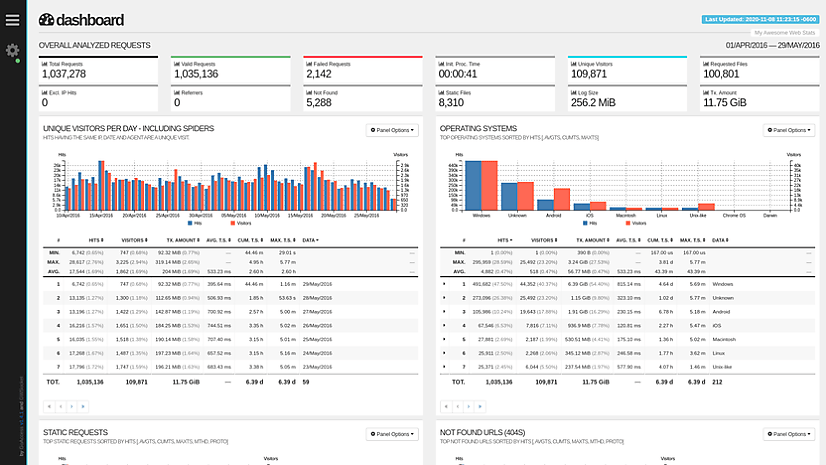
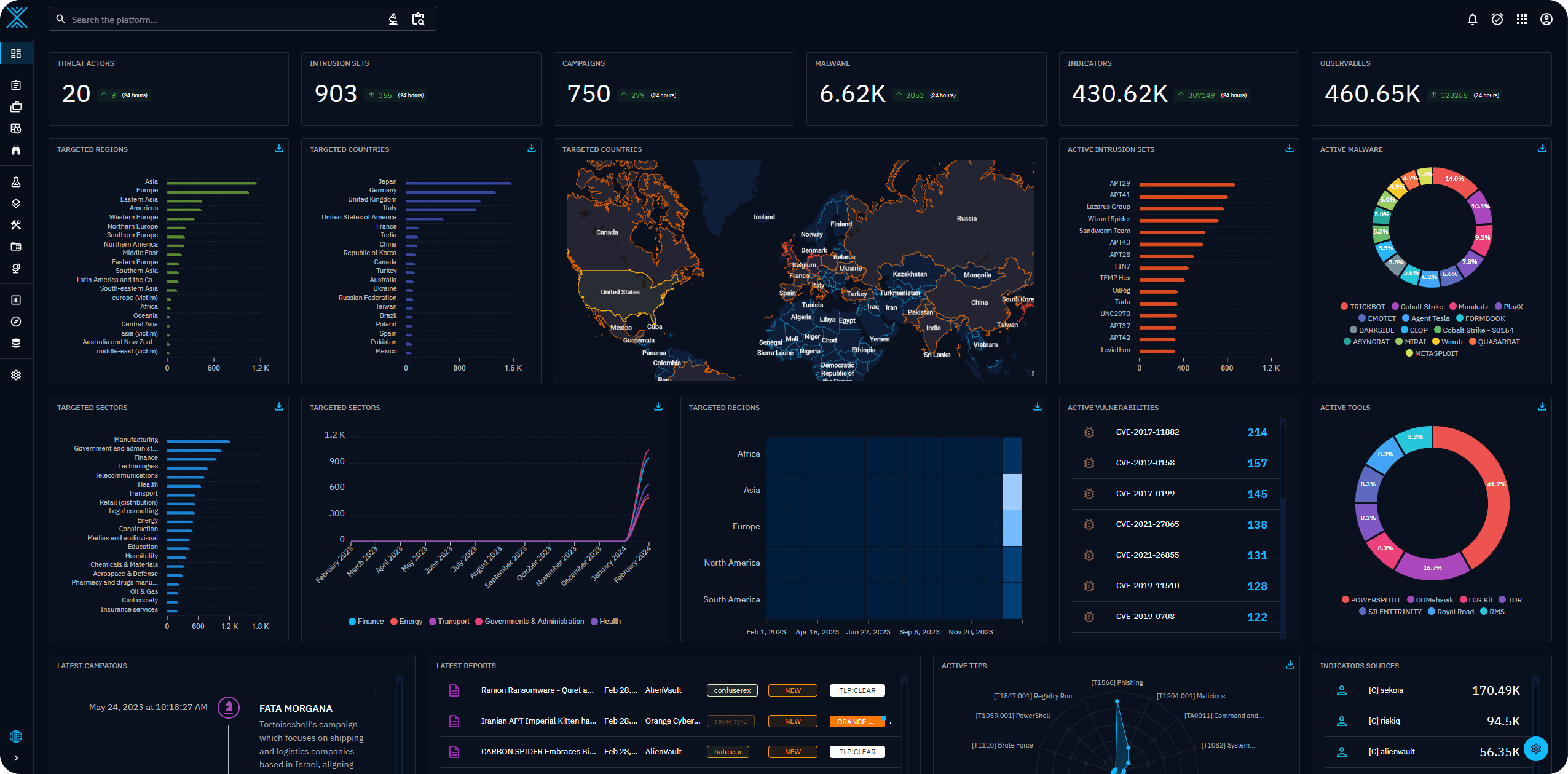
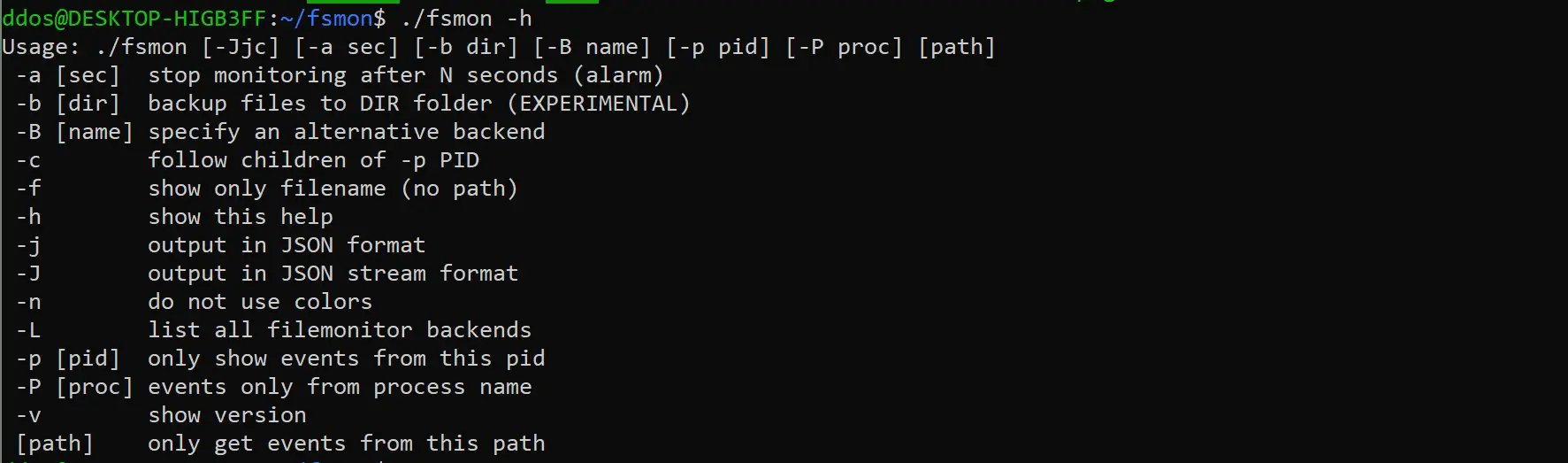
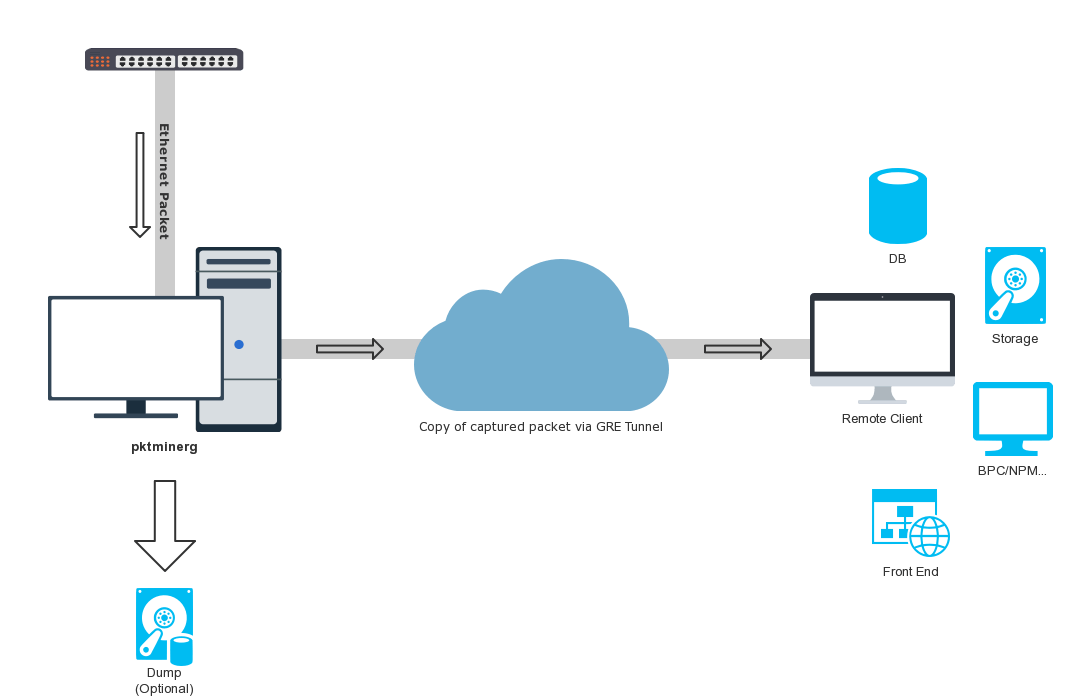
pcap-did-what: Analyze pcaps with Zeek and a Grafana Dashboard
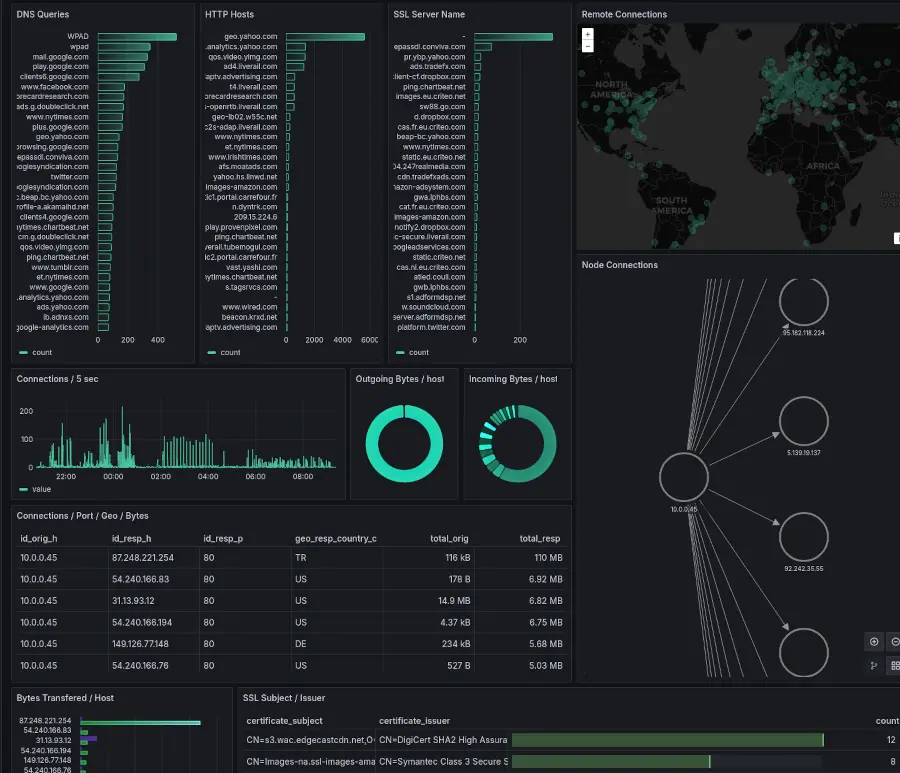
Zeek & Grafana Integration for Network Monitoring This repository provides a quick way to get started using Zeek with a practical use case. The focus is to analyse a network pcap and enable easy...