The pentester's Swiss knife
KexecDDPlus This proof-of-concept is the result of a research project that aimed at extending the work of @floesen_ on the KsecDD Windows driver. It relies on Server Silos to access the KsecDD driver directly, without having...
Cloudlist Cloudlist is a multi-cloud tool for getting Assets (Hostnames, IP Addresses) from Cloud Providers. This is intended to be used by the blue team to augment Attack Surface Management efforts by maintaining a...
Power Pwn Power Pwn is an offensive and defensive security toolset for Microsoft Power Platform. Disclaimer: These materials are presented from an attacker’s perspective to raise awareness of the risks of underestimating the security...
Linux Process Injection This repository contains proof-of-concept implementations of various Linux process injection primitives. This code is meant to provide simple examples of injection techniques in action, allowing defenders to understand how they work...
Fibratus Fibratus is a tool for exploration and tracing of the Windows kernel. It lets you trap system-wide events such as process life-cycle, file system I/O, registry modifications or network requests among many other observability signals. In a...
Spoofy Spoofy is a program that checks if a list of domains can be spoofed based on SPF and DMARC records. You may be asking, “Why do we need another tool that can check if...
Ldapper A GoLang tool to enumerate and abuse LDAP. Made simple. Ldapper was created with for use in offensive security engagements for user enumeration, group enumeration, and more. Ldapper uses familiar “net” commands such as...
apk.sh apk.sh is a Bash script that makes reverse engineering Android apps easier, automating some repetitive tasks like pulling, decoding, rebuilding, and patching an APK. Features apk.sh basically uses apktool to disassemble, decode and rebuild resources...
NimPlant – A light first-stage C2 implant written in Nim and Python Feature Overview Lightweight and configurable implant wrote in the Nim programming language Pretty web GUI that will make you look cool...
URLFinder URLFinder is a high-speed, passive URL discovery tool designed to simplify and accelerate web asset discovery, ideal for penetration testers, security researchers, and developers looking to gather URLs without active scanning. Feature Curated...
fingerprintx fingerprintx is a utility similar to httpx that also supports fingerprinting services like as RDP, SSH, MySQL, PostgreSQL, Kafka, etc. fingerprintx can be used alongside port scanners like Naabu to fingerprint a set of ports identified...
Grepmarx – source code static analysis platform for security auditors Grepmarx is a web application providing a single platform to quickly understand, analyze and identify vulnerabilities in possibly large and unknown code bases. Features...
Nuke It From Orbit With the precision of a brain surgeon wielding a chainsaw, nifo can obliterate most AV/EDR products from endpoints or servers running the world’s most popular operating system, even if they’re...
lynis Lynis is a security auditing tool for systems based on UNIX like Linux, macOS, BSD, and others. It performs an in-depth security scan and runs on the system itself. The primary goal is to test...
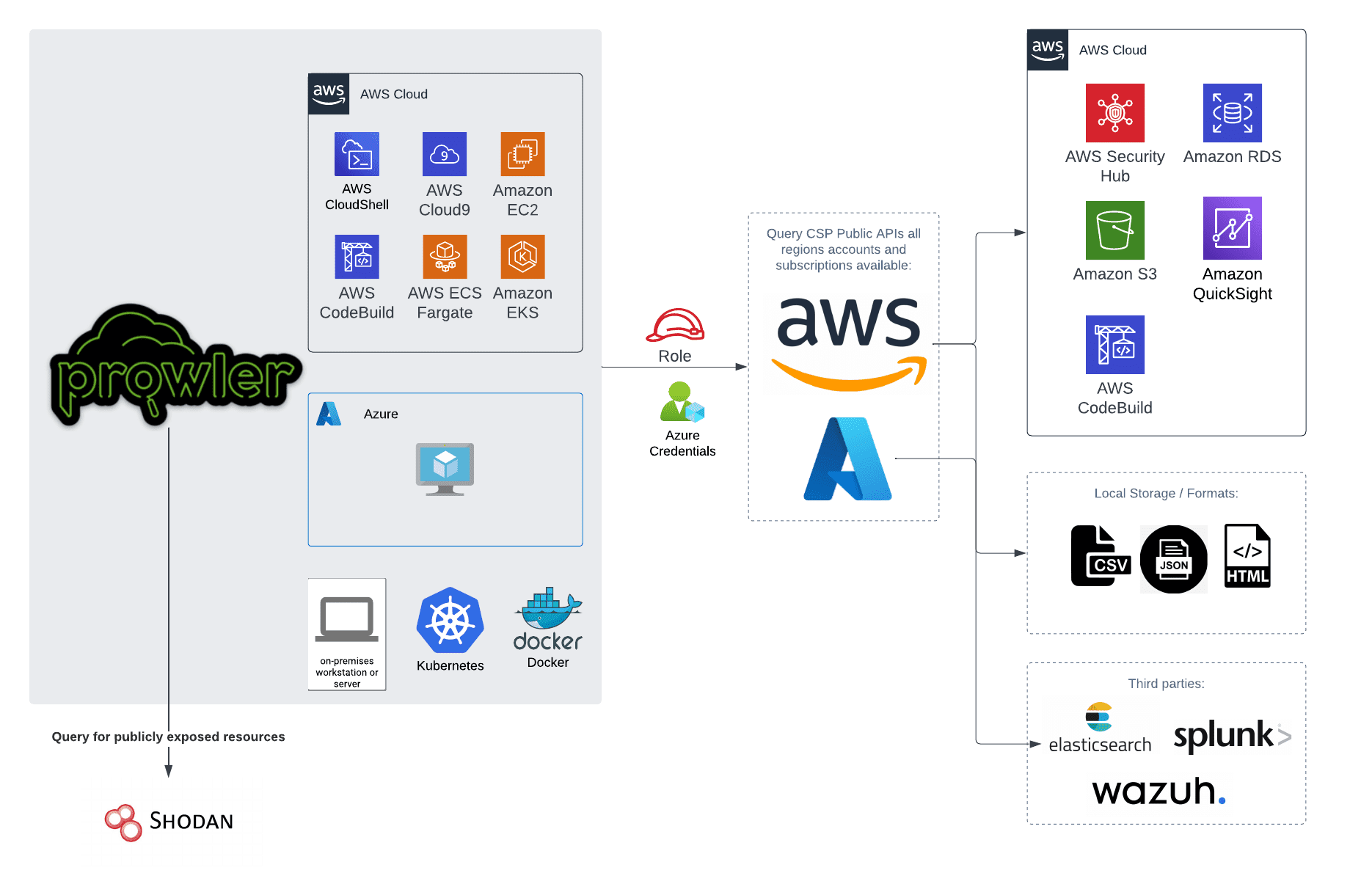
Prowler: AWS Security Tool Prowler is a command-line tool for AWS Security Best Practices Assessment, Auditing, Hardening, and Forensics Readiness Tool. It follows guidelines of the CIS Amazon Web Services Foundations Benchmark (49 checks)...
mailcat The only cat who can find existing email addresses by nickname. Supported providers Total 37 providers, > 170 domains and > 100 aliases. Name Domains Method Gmail gmail.com SMTP Yandex yandex.ru + 5...