Congressman David Schweikert (Republican, Arizona, District AZ-01) has introduced the Cybercrime Marque and Reprisal Authorization Act of...
Sangoma has issued an urgent alert regarding an actively exploited zero-day vulnerability in FreePBX installations where the...
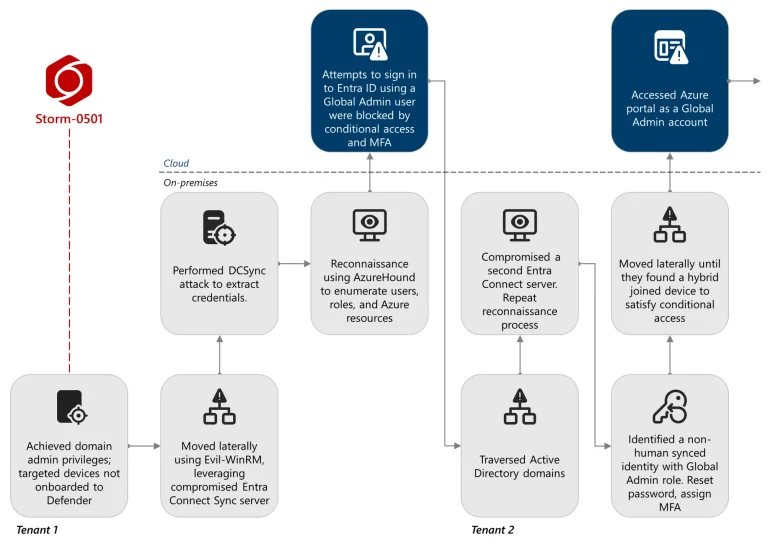
According to a report by Microsoft Threat Intelligence, the group Storm-0501 has shifted its focus from traditional...
The U.S. National Security Agency, the U.K.’s National Cyber Security Centre, and partners from more than ten...
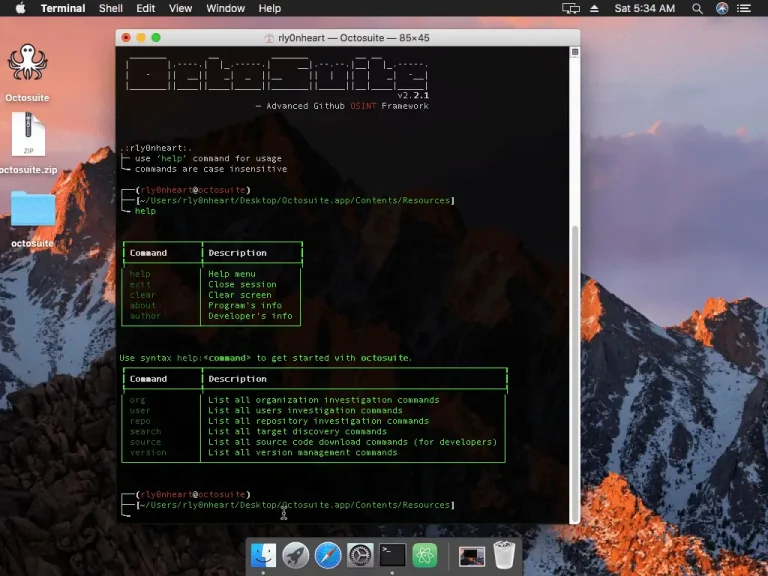
Octosuite Octosuite is an open-source lightweight yet advanced osint framework that targets GitHub users and organizations. With...
GitHub has announced the launch of the public preview of the Grok Code Fast 1 model in...
NetScaler has issued an urgent advisory warning administrators of three newly discovered vulnerabilities in NetScaler ADC and...
A newly discovered critical vulnerability in Docker Desktop has placed Windows users at significant risk. Tracked as...
MathWorks, the developer of the widely used software MATLAB and SIMULINK, has disclosed a major ransomware attack...
Drift has disclosed details of a security incident involving its Salesforce integration. Between August 8 and August...
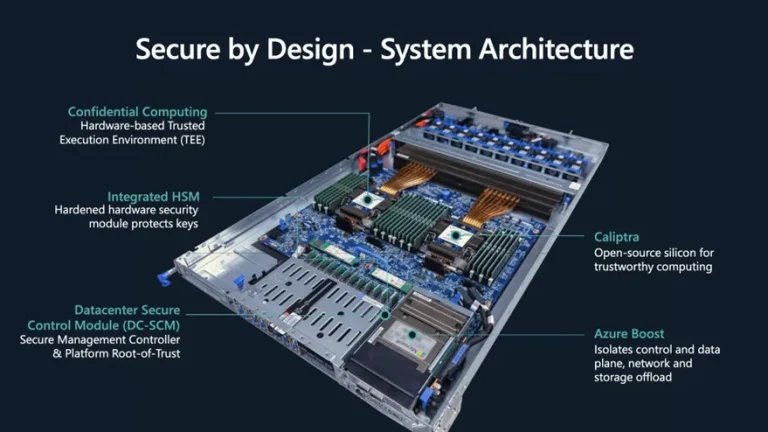
For many years, Microsoft has built its cloud security strategy around hardware, and after a string of...
In August of this year, specialists from Israel’s National Digital Agency uncovered a large-scale campaign known as...
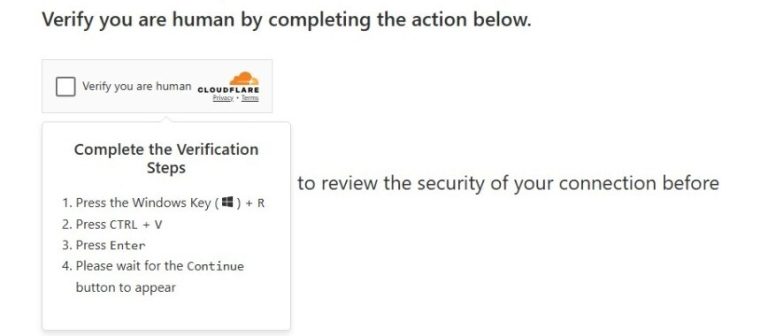
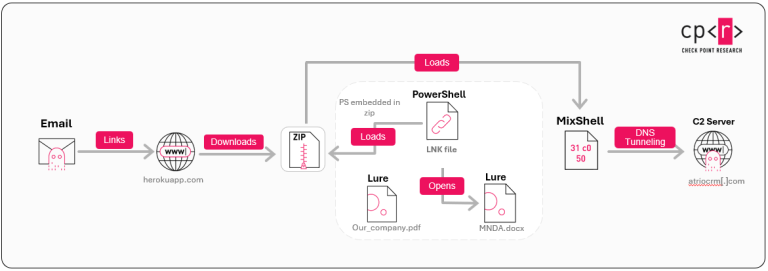
Researchers at Check Point Research have uncovered a new targeted campaign, dubbed ZipLine, which leverages the malicious...
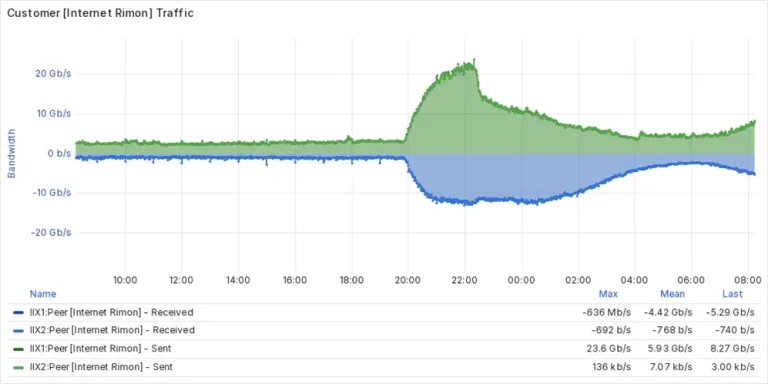
A cyberattack against the Israeli “kosher internet” provider Internet Rimon, which serves religious and ultra-Orthodox communities, disrupted...
Nevada’s network of state institutions was left paralyzed following an incident that occurred in the early hours...
Researchers have unveiled ONEFLIP, a groundbreaking attack technique that introduces a novel method of covertly modifying neural...