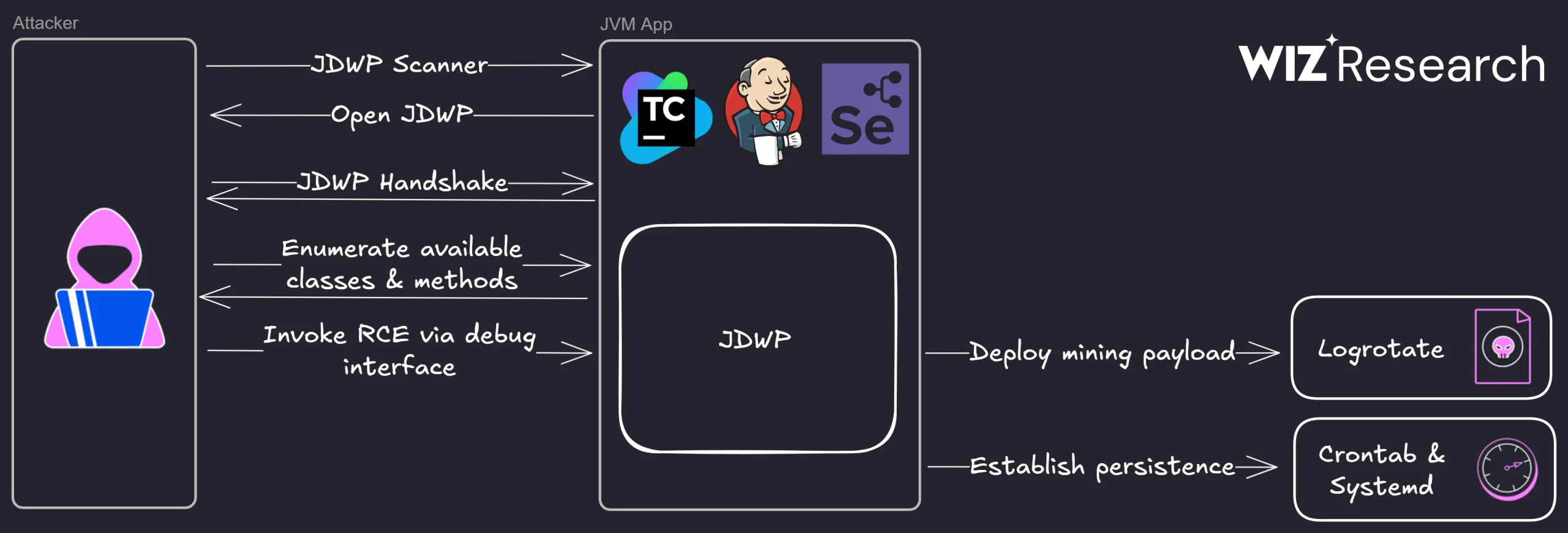
Spain’s .es Domain Surges 19x in Cybercrime Use: Now Third Most Popular for Phishing & RATs
In recent months, cybersecurity experts have observed a dramatic surge in the malicious exploitation of domains within the .es top-level domain (TLD). Over the past six months alone, the number of such incidents has...