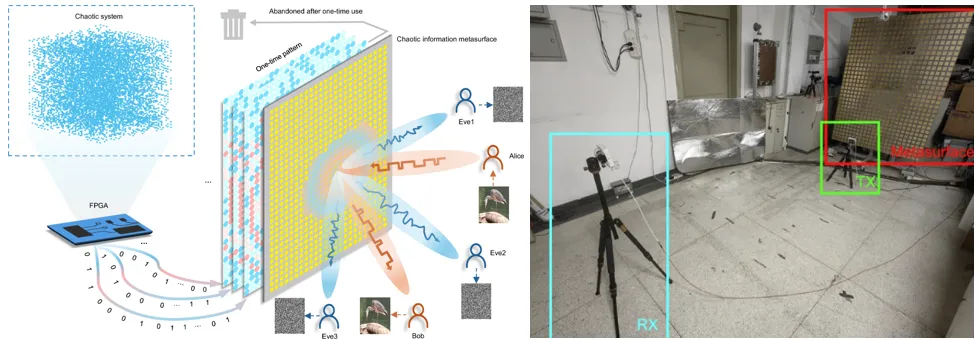
The Password Crisis: 98.5% of Corporate Passwords Are Insecure, Leaving Networks Vulnerable
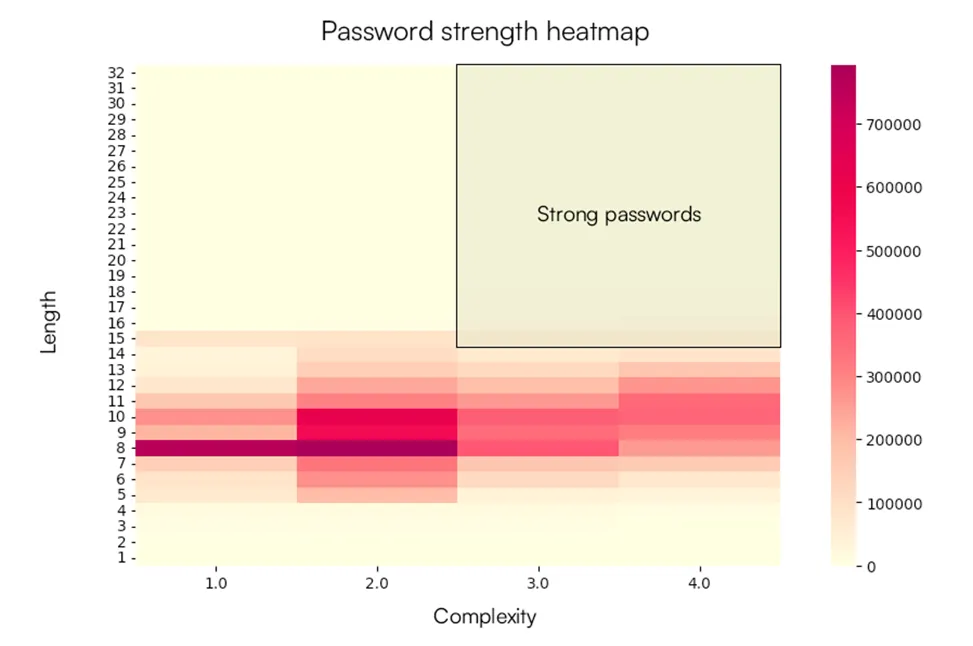
In a recent analysis based on the examination of 10 million real-world compromised passwords, researchers at Specops have laid bare the ongoing vulnerability of corporate networks stemming from human error. The passwords were drawn...