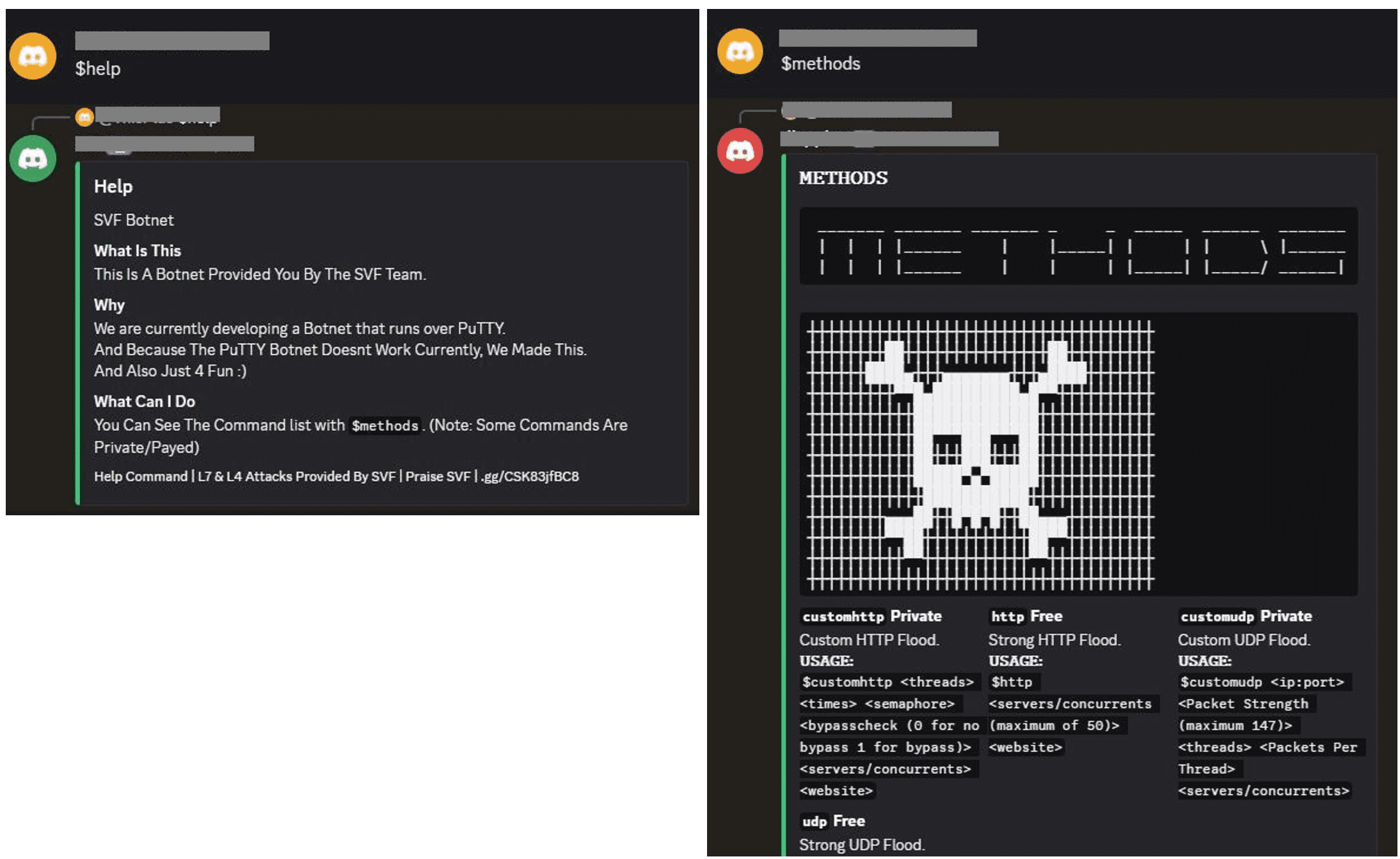
Brave Browser Blocks Microsoft Recall by Default, Citing Major User Privacy Concerns
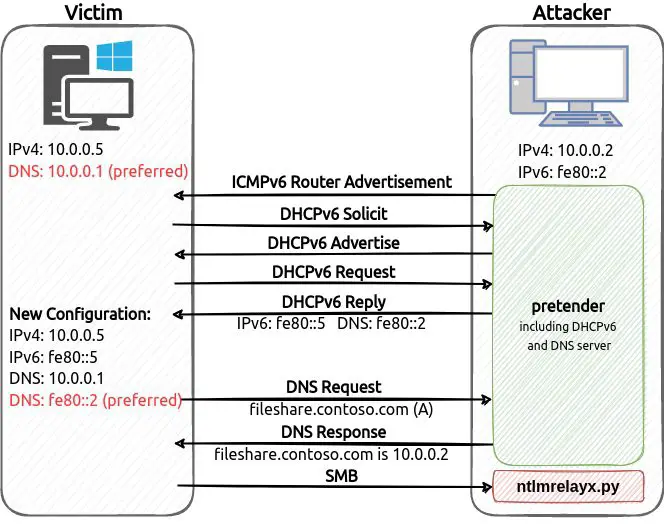
Brave Software has decided to block the Windows Recall feature by default in its browser, citing the protection of user privacy as the driving force behind the move. This policy now applies to all...