Outdated Netgear Router & Bitdefender Box V1 Exploited for Full Remote Control
At the inaugural DistrictCon Junkyard competition, analysts from Trail of Bits vividly demonstrated the grave risks posed by outdated networking devices left without updates. During the event, they remotely compromised two discontinued products—the Netgear WGR614v9 router and the Bitdefender Box V1—earning recognition for one of the most unconventional attack scenarios. Although initial access to these systems was limited to the local network, both exploits ultimately achieved full control, reflecting realistic threats in domestic and office environments. Detailed accounts of the vulnerabilities, analysis stages, and demonstrations have been published in Trail of Bits’ official GitHub repository.
The Netgear analysis began with a hardware teardown: researchers located debugging interfaces and memory chips, then downloaded the device’s firmware from the manufacturer’s website. Using tools like binwalk and unblob, they recursively unpacked the firmware image, performed a port scan, and gained access to the UART console—allowing them to inspect the running kernel, active processes, and services. Particular attention was given to the UPnP daemon (upnpd), responsible for Universal Plug-and-Play support.
Through the UPnP implementation, three successful attacks were executed by chaining vulnerabilities: an authentication bypass in the SOAP handler, buffer overflows in the BSS and stack segments, and command injection. One of the most inventive techniques, dubbed bashsledding, involved injecting ROP gadgets that called system(), with the payload written to non-volatile memory (NVRAM) via a domain locking mechanism. To circumvent reliance on precise code offsets, the payloads used extended sequences of whitespace, interpreted by the Bash shell until the intended command was discovered.
Another attack variant, called bigfish_littlepond, exploited a BSS segment overflow to alter a string pointer passed to the shell. Researchers discovered that upnpd spawned a helper process named bpa_monitor. By substituting the invoked command name and injecting a payload via a separate SOAP request, they achieved arbitrary code execution.
The Bitdefender Box V1, despite operating on a different architecture and security model, proved similarly vulnerable. Designed to secure home networks and analyze traffic, the device contained a flaw in its update mechanism: firmware could be downgraded without authentication. This was compounded by a checksum verification vulnerability, enabling arbitrary command execution.
The analysis began with a hardware dump of the Winbond W25Q128FV SPI memory chip. Since official update servers were no longer accessible, researchers turned to archived APKs of the mobile companion app and, using VirusTotal, identified version 1.3.12.869, which included firmware 1.3.11.490 signed with a valid key.
A comparative analysis revealed that the md5 parameter in HTTP requests to /check_image_and_trigger_recovery lacked proper character sanitization. This allowed injection of a command that added the researchers’ SSH key to authorized_keys, granting persistent remote access.
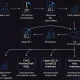
The attack chain involved the following steps: calling the /update_auth_token endpoint (to reset configuration and lift update restrictions), uploading a firmware archive via /upload_backup_firmware, verifying its structure through /decode_image, and finally injecting a command at the /check_image_and_trigger_recovery stage.
Although the device featured RSA-based signature verification, it lacked a version check mechanism—allowing any signed, albeit outdated, firmware image to pass scrutiny and execute unsafe code.
Both incidents—Netgear and Bitdefender—highlight deep-rooted vulnerabilities in the Internet of Things ecosystem. UPnP SOAP interfaces are often left unsanitized, and their services commonly run with excessive privileges. The combination of insecure UPnP implementations and rollback-prone update mechanisms renders many devices highly susceptible to compromise.
Junkyard’s organizers emphasize that the aim of such competitions extends beyond showcasing technical prowess—it is to spotlight the critical issue of abandoned hardware. Unlike elite contests like Pwn2Own, Junkyard focuses on accessibility: it welcomes inexpensive, unsupported devices. Participants are encouraged to evaluate firmware availability, locate debugging interfaces, analyze FCC certifications, and scour legacy images or apps for useful data.
The takeaway is clear: the end of official support does not equate to the end of threats. Any obsolete router or filtering appliance, once touted as a safeguard, can swiftly become a weak link. Hence, when selecting new hardware, one must consider not only its features but also the duration of security support the manufacturer is prepared to guarantee.