A threat group linked to the Democratic People’s Republic of Korea (DPRK) is intensifying its attacks on companies operating in the Web3 and cryptocurrency sectors, deploying malware crafted in the Nim programming language. These operations underscore the group’s continual refinement of tactics and technical sophistication.
According to researchers at SentinelOne, the malware exhibits a rare capability on macOS: it employs process injection and communicates via the encrypted wss protocol—an obfuscated variant of WebSocket designed for secure remote interactions.
One of the more sophisticated features is its method of persistence. This is achieved by registering handlers for the SIGINT and SIGTERM system signals, enabling the malware to re-establish itself if the process is terminated or if the system is rebooted.
Dubbed “NimDoor,” the malware campaign has previously been partially documented by research teams from Huntabil.IT, Huntress, and Validin. However, the current wave introduces new and more advanced malicious modules.
The infection begins with social engineering. Attackers reach out to potential victims via messaging platforms such as Telegram, proposing a Zoom video call. The meeting is scheduled through Calendly, and the target receives an email that appears to contain a legitimate Zoom invite, accompanied by instructions to install a supposed SDK update for “compatibility.”
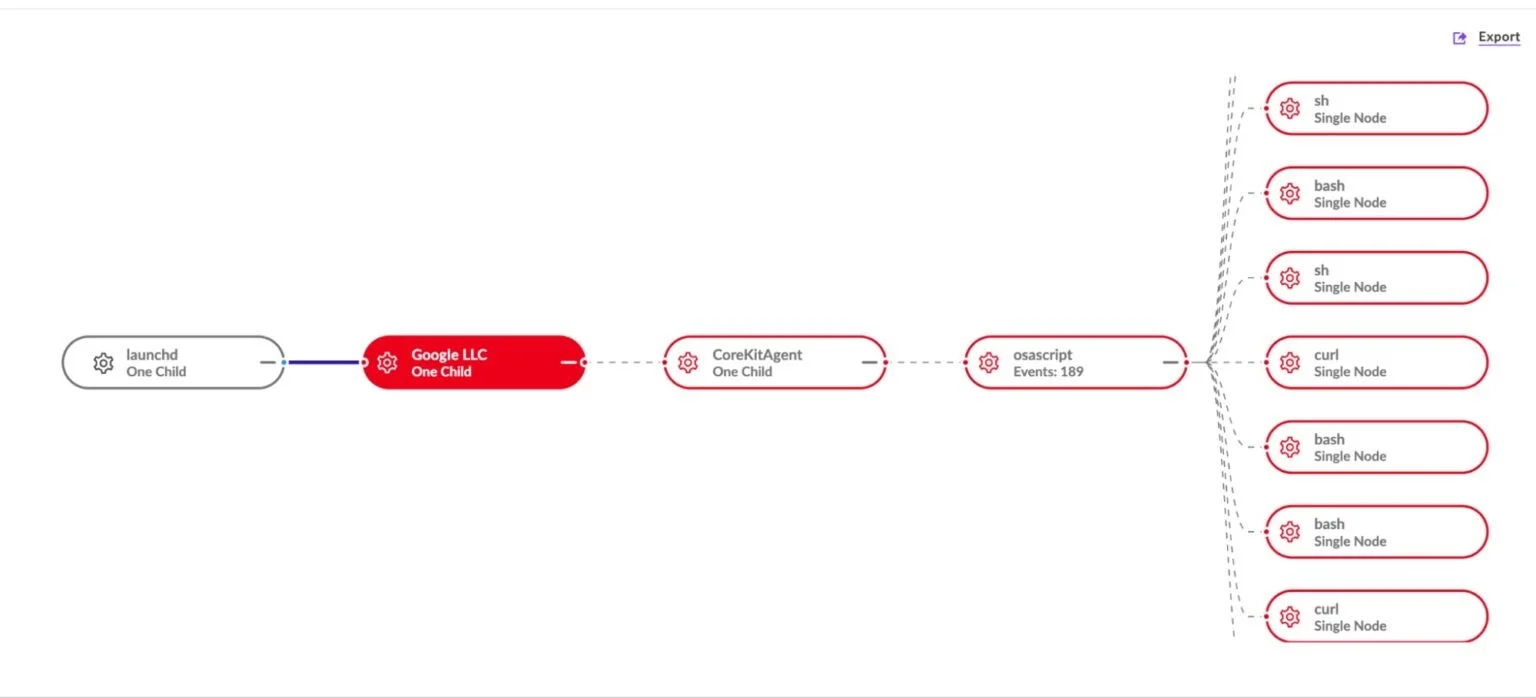
In reality, the victim executes an AppleScript that retrieves the second-stage payload from a remote server. Simultaneously, the victim is redirected to the official Zoom website, lending an air of authenticity to the ruse. The malware then extracts ZIP archives containing executable files designed to establish persistence and deploy bash scripts to harvest sensitive data.
At the heart of the infection is a C++ loader called InjectWithDyldArm64 (also known as InjectWithDyld). This loader decrypts two embedded binaries—Target and trojan1_arm64. It initiates the Target binary in a suspended state, injects the second binary’s executable code, and then resumes execution.
Subsequently, the malware establishes communication with a remote command-and-control (C2) server, enabling the adversary to collect system metadata, execute arbitrary shell commands, and manipulate working directories. All output is transmitted back to the C2 infrastructure.
The trojan1_arm64 module is capable of fetching additional payloads, including credential-stealing components tailored to popular browsers such as Arc, Brave, Google Chrome, Microsoft Edge, and Mozilla Firefox. Telegram session data is also exfiltrated.
A notable element of this campaign is the use of Nim-compiled executables that serve as a platform for the CoreKitAgent. This component monitors for any attempts to terminate the malware’s processes and rapidly restores them, greatly enhancing resilience against basic defensive measures.
The malware also runs an AppleScript that, every 30 seconds, transmits a heartbeat signal to one of two hardcoded servers along with a list of currently running processes. Through this channel, it can also receive and execute additional commands.
This campaign reveals a growing interest among North Korean actors in macOS environments and their increasing reliance on AppleScript for post-exploitation and data exfiltration. While previous attacks utilized Go and Rust, the adoption of Nim reflects a strategic pivot toward obscuring malicious code more effectively.
Nim’s selection is driven by its ability to obfuscate logic and blur the boundaries between user and system code. Its compilation model allows malicious functionality to be deeply embedded within binaries, rendering detection and analysis considerably more difficult.






