The cybersecurity firm Proofpoint has uncovered a new phishing campaign orchestrated by the Iranian faction MuddyWater. This operation disseminates legitimate remote monitoring and management software, Atera, among Israeli organizations within the global manufacturing, technology, and information security sectors.
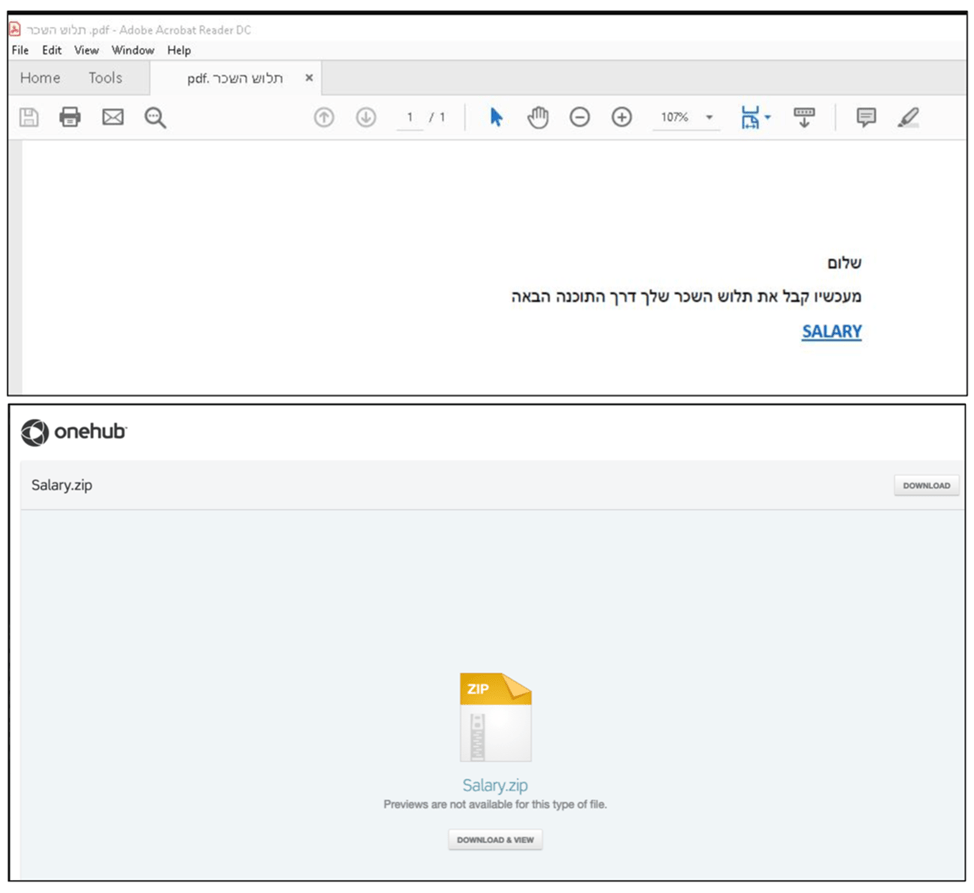
This assault, which transpired between March 7th and 11th, is characterized by the strategic placement of files on file-sharing platforms (Egnyte, Onehub, Sync, and TeraBox) and the deployment of phishing messages themed around invoice payments or salary information, dispatched from a compromised account linked to the Israeli domain “co.il”.

Clicking on a link within an attached PDF document leads to the downloading of a ZIP archive, which contains an MSI installer that ultimately installs the Atera Agent on the compromised system. The MuddyWater group has been utilizing the Atera Agent since July 2022.
The activity identified marks a significant shift in MuddyWater’s tactics. While not the first instance of the group’s use of attachments with malicious links, Proofpoint researchers have observed for the first time an attempt by MuddyWater to deliver a malicious link via an attached PDF file, rather than a direct link in the email.
Proofpoint attributes this campaign to MuddyWater based on the group’s known techniques, tactics, and procedures (TTPs), the campaign’s targeting profile, and malware analysis. In 2022, the United States Cyber Command associated the group with Iran’s Ministry of Intelligence and Security.






