Microsoft: SharePoint Zero-Day Exploit Leaked, Bypassed Patch, and Actively Attacked By China-Linked APTs
Microsoft has acknowledged that its July security updates failed to fully address vulnerabilities in on-premises versions of SharePoint, leaving systems susceptible to remote code execution. As a result, targeted attacks have continued, with experts suspecting that exploit details were leaked prior to the official patch release.
The mystery lies in how threat actors—including Chinese hackers, cyber-espionage groups, and ransomware operators—discovered a way to exploit the vulnerability and circumvent the patch issued just a day later.
“There was a leak somewhere,” said Dustin Childs, head of threat awareness at Trend Micro’s Zero Day Initiative (ZDI), in an interview with The Register. “We are now seeing a zero-day exploit being used in the wild—what’s worse is that it bypasses the patch released the following day.”
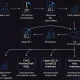
The chain of events began in May at the Pwn2Own competition in Berlin, hosted biannually by ZDI. On May 16, Vietnamese researcher Dinh Ho Anh Khoa demonstrated an exploit for Microsoft SharePoint, combining an authentication bypass with an unsafe deserialization bug. He was awarded $100,000. Following the presentation, Khoa and Microsoft representatives met privately to share detailed technical information. If the bug is deemed unique, Microsoft is typically granted 90 days to issue a fix.
Childs asserts that Microsoft received a full report on the same day as the demonstration. Nevertheless, widespread exploitation began on July 7, a day before the public disclosure of two vulnerabilities: CVE-2025-49704 (unauthenticated remote code execution) and CVE-2025-49706 (data spoofing). Security updates were released concurrently, though they arrived after the attacks had already commenced.
While the disclosure timeline aligned with coordinated vulnerability disclosure guidelines—60 days post-report—Childs emphasizes that the leak altered everything: “What went wrong was the leak.”
One possible explanation is the compromise of Microsoft’s Active Protections Program (MAPP), which provides vetted partners with early access to pre-patch vulnerability information under NDA, typically 14 days prior to release (designated r-14). In this case, that date was June 24. Attacks began on July 7, and the patches released on July 8 were quickly found to be ineffective.
Childs suggests that anyone with access to the CVE information through MAPP might have noticed the incomplete fix. ZDI confirmed that the authentication bypass had been addressed too narrowly.
On July 18, Eye Security published an analysis of large-scale attacks leveraging the SharePoint vulnerability chain. The following day, Microsoft issued an urgent advisory, admitting that the original patches had failed. On July 21, supplemental updates were released, including fixes for SharePoint 2016. By then, however, over 400 organizations had already been compromised. The attacks were attributed to at least two Chinese hacker groups—Linen Typhoon and Violet Typhoon—as well as the ransomware-linked group Storm-2603.
Microsoft declined to answer The Register’s specific questions but stated it would “evaluate the incident and implement process improvements.”
Satnam Narang, a special operations engineer at Tenable, speculated that the leak might not have been the only avenue attackers used. Researcher Soroush Dalili was reportedly able to reconstruct the exploit using Google’s Gemini LLM, suggesting that adversaries could have done the same with models like Gemini, Claude Opus, or OpenAI’s GPT-4o.
Still, Narang concedes, “It’s difficult to say what exact chain of events enabled the exploitation of these vulnerabilities in real-world attacks.”
Notably, Microsoft has yet to publish MAPP guidance for two newly identified related vulnerabilities—CVE-2025-53770 and CVE-2025-53771. According to Childs, this may indicate a temporary lapse in trust toward the program: “If I believed the leak originated from MAPP, I wouldn’t share anything through it either.”