Microsoft 365 Under Phishing Attack: Trustwave Reports on Growing Greatness Platform Use
Researchers from Trustwave have reported a steady increase in the use of a Phishing-as-a-Service (PhaaS) platform called Greatness, which targets the collection of Microsoft 365 user credentials.
Greatness is marketed to other cybercriminals as a ready-to-use phishing kit complete with supported infrastructure, all for just $120 a month. This affordability lowers the entry barrier and facilitates large-scale attacks, even for inexperienced hackers.
The attack chains involve sending phishing emails with malicious HTML attachments. When opened, these attachments redirect recipients to a fake login page, capturing the entered credentials.
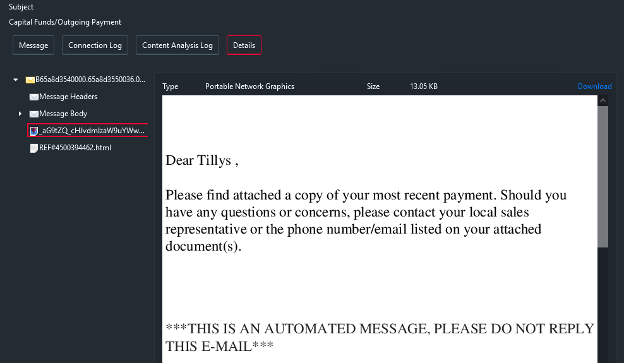
A phishing variant using HTML attachment
To enhance the likelihood of success, the emails mimic trusted sources, such as banks and employers, and create a false sense of urgency — classic tactics employed by malefactors.
The total number of victims of this campaign remains unknown, but Greatness is actively used and maintained, with its own Telegram community for sharing tips and attack methods.
Additionally, phishing attacks have been observed against South Korean companies, using lures that mimic technology companies to distribute VenomRAT (also known as AsyncRAT) through malicious Windows shortcut files (LNK).
“Malicious shortcut files disguised as legitimate documents are continuously being distributed,” warns the AhnLab Security Emergency Response Center (ASEC). Users may mistakenly regard a shortcut file as a regular document, as the “.LNK” extension is not typically displayed in the standard Windows file explorer.





