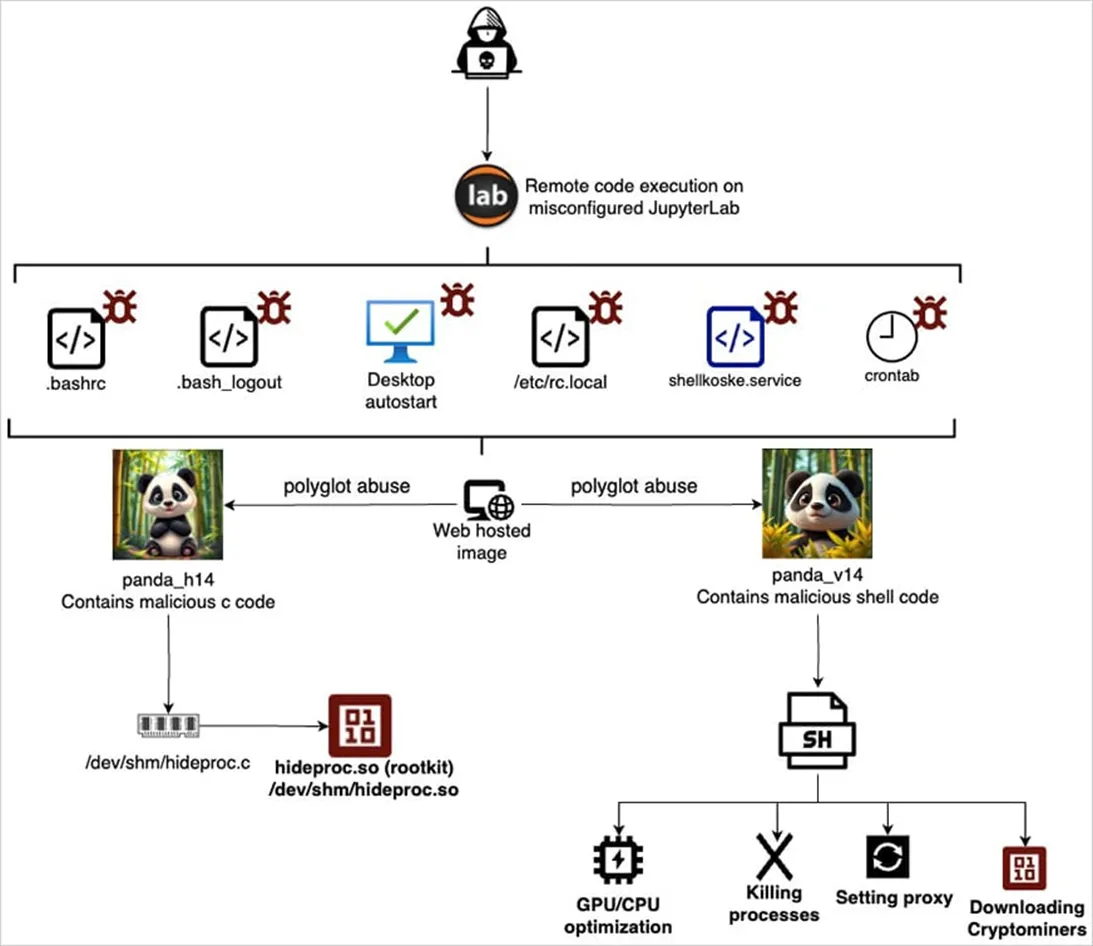
An unusual attack targeting Linux servers has unveiled a new echelon of malware obfuscation—and possibly, its artificial origin. Researchers at AquaSec have documented a threat dubbed Koske, which hides within seemingly innocuous images of pandas and employs adaptive logic that, according to experts, may have been generated using large language models or automated development systems.
What sets Koske apart is its ability to execute directly in memory without ever writing to disk, leveraging polyglot files—formats that allow a single object to function both as an image and an executable script. Specifically, the malicious code resides at the end of JPEG files containing panda photos. Visually indistinguishable from ordinary images, these files, when parsed by a command-line interpreter, trigger embedded scripts.
The intrusion begins with the exploitation of misconfigured JupyterLab instances exposed to the internet. Once access is obtained, the attacker downloads two such images from popular hosting services like OVH images, FreeImage, and PostImage. Each image conceals a separate component: the first is a C fragment that compiles directly in memory and operates as a rootkit; the second is a shell script responsible for stealth operations and persistence.
The shell component uses native Linux utilities to execute and anchor itself within the system. It configures system services and cron jobs at 30-minute intervals to ensure continuous reinfection. To evade network filters and proxy constraints, it rewrites /etc/resolv.conf, locks the file using chattr +i, flushes iptables rules, resets proxy environment variables, and initiates a custom proxy discovery module utilizing curl, wget, and raw TCP requests.
The rootkit acts as a dynamic extension loaded via LD_PRELOAD, intercepting readdir() system calls to conceal processes and files containing strings like “koske” or “hideproc”. It also references a supplemental list of process IDs stored in /dev/shm/.hiddenpid, a technique that renders it invisible to most user-level monitoring tools.
Once persistent, the malware downloads cryptocurrency miners from GitHub. Before deployment, Koske assesses the host’s hardware capabilities—examining CPU and GPU type and power—then selects from a pool of 18 cryptocurrencies, including Monero, Ravencoin, Zano, Nexa, and Tari, all known for their anonymity.
Each currency is paired with fallback mining pools. If the primary pool is unreachable, Koske automatically switches, underscoring its high degree of autonomy and resilience.
Researchers observed Serbian IP addresses used in the attacks, Serbian phrases within the scripts, and Slovak artifacts in GitHub repositories. However, no direct affiliation with a known threat actor has been confirmed. Experts highlight that Koske’s level of adaptability and stealth strongly suggests AI involvement—either in code generation or development automation. This marks a potential new phase in malware evolution: one defined by heightened autonomy, self-optimization capabilities, and minimal need for human intervention.





