Kinsing Cryptojackers Expand Botnet, Exploit Fresh Vulnerabilities
The Kinsing cryptojacking group continues to evolve, posing a persistent threat in the digital realm. AquaSec reports that since 2019, Kinsing has been orchestrating illicit cryptocurrency mining campaigns, swiftly integrating new vulnerabilities to expand its botnet.
Kinsing, also known as H2Miner, refers both to the malware and the group behind it. Since its first documentation in January 2020, Kinsing has continuously enhanced its toolkit with new exploits to incorporate infected systems into its cryptomining botnet.
Campaigns leveraging Golang-based malware have exploited vulnerabilities in systems such as Apache Log4j, Atlassian Confluence, Citrix, Linux, and Oracle WebLogic Server. Misconfigurations in Docker, PostgreSQL, and Redis have also been utilized for initial access.
In 2021, CyberArk’s analysis revealed similarities between Kinsing and another malware, NSPPS, concluding that both belong to the same family.
Kinsing’s attack infrastructure is categorized into three types: initial servers for scanning and exploiting vulnerabilities, servers for downloading payloads, and C2 servers for maintaining communication with compromised hosts.
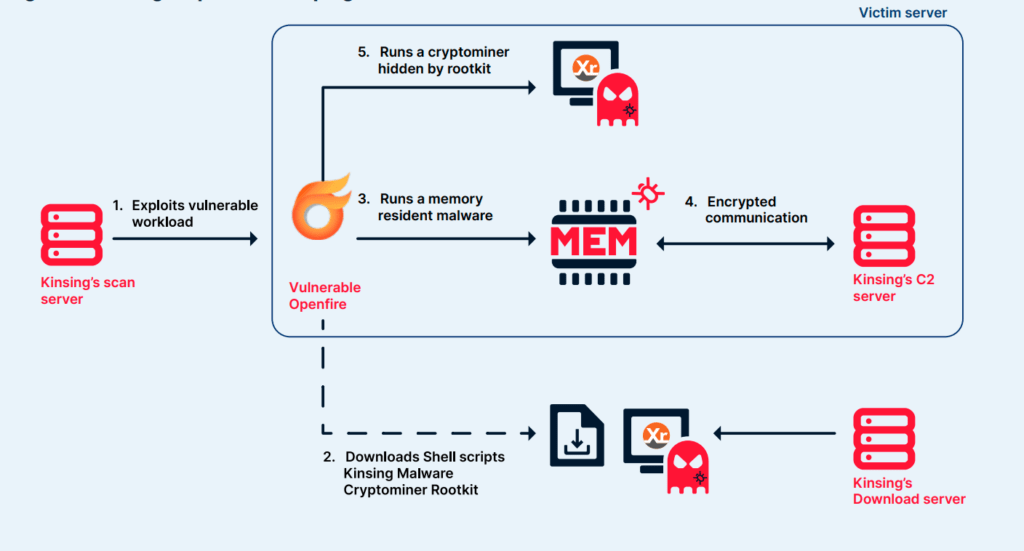
Kinsing’s Openfire Campaign
“Kinsing targets various operating systems with different tools. For instance, Kinsing often uses shell and Bash scripts to exploit Linux servers. We’ve also seen that Kinsing is targeting Openfire on Windows servers using a PowerShell script. When running on Unix, it’s usually looking to download a binary that runs on x86 or arm,” AquaSec reports.
The group also actively targets open-source applications, which constitute 91% of all attacked software. The primary targets are runtime applications (67%), databases (9%), and cloud infrastructure (8%).
Analysis of the identified malware samples revealed three categories of programs used by the group in their campaigns:
- Type I and II scripts that download subsequent attack components, eliminate competitors, bypass defenses, and disable firewalls and security tools.
- Auxiliary scripts designed for initial access, disabling specific security components of Alibaba Cloud and Tencent Cloud, opening reverse shells, and downloading miner payloads.
- Binary files serving as secondary payloads, including the Kinsing core and a Monero cryptocurrency miner.
The malware manages the mining process, shares the process identifier (PID) with the C2 server, performs connectivity checks, and sends execution results.
“Kinsing targets Linux and Windows systems, often by exploiting vulnerabilities in web applications or misconfigurations such as Docker API and Kubernetes to run cryptominers,” AquaSec notes. Proactive measures, such as hardening workloads before deployment, are crucial to preventing threats like Kinsing.
Data from the AquaSec report indicate that botnets continually find new ways to expand and enlist machines worldwide for malicious activities.
To protect against threats like Kinsing, proactive security measures are essential, including timely vulnerability remediation, proper system configuration, and solutions to prevent malware from exploiting unpatched attack vectors.





