This article will explain how to modify the default settings of sshd to ensure that sshd is secure and restricted to protect your server from hackers. You need to restart sshd every time you change the sshd configuration file.
Change ssh default port number
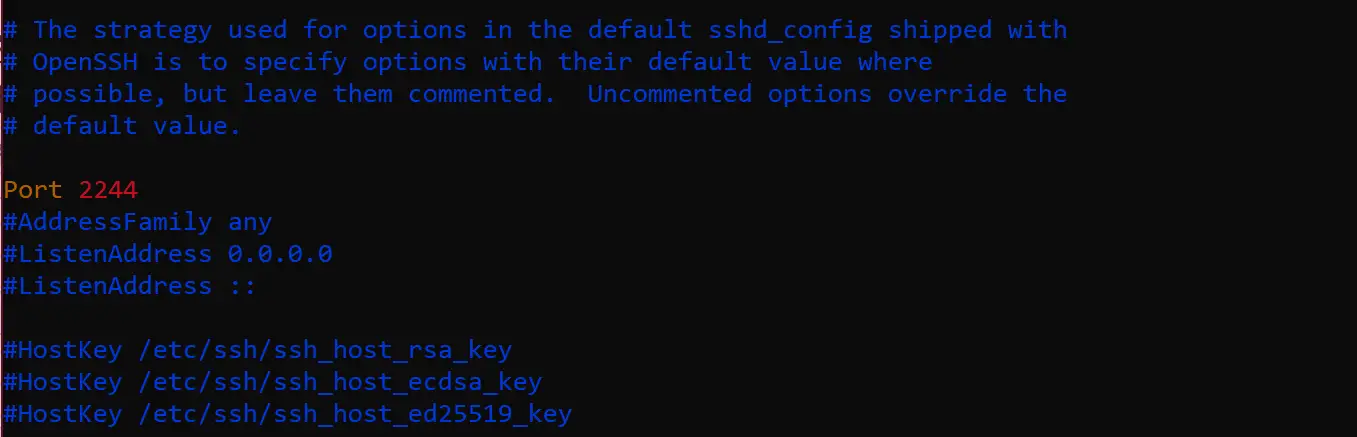
First, it is recommended to change sshd’s default port number 22 to a port number greater than 1024. Most port scanners only scan ports below 1024 by default. Open the sshd configuration file /etc/ssh/sshd_config and find the following code:
Allow only specified hosts to connect
In this step, we will restrict the connection to the server through ssh by the client’s IP address. Edit the file /etc/hosts.allow and add the following code:
sshd: X
X represents the IP address allowed to log in to sshd. If multiple IP addresses are allowed to log in, they are separated by spaces.
Now edit the /etc/hosts.deny file to deny logins to all other hosts:
sshd:ALL
Allow only specified users to log in
Not every user needs to use ssh to connect to the server. Allowing only specified users to connect to the server to enhances ssh security. For example, only allow ddos user to connect to the server through ssh, edit /etc/ssh/sshd_config and add the following code:
AllowUsers ddos
If you want to add multiple users, you can use spaces to separate them.
Disable root ssh login
It is usually wise to not allow the root user to connect to the server via ssh. You can edit the / etc / ssh / sshd_config file to change or add the following code:
PermitRootLogin no