gshark: Scan for sensitive information in Github easily and effectively
GShark
The project is based on golang with AdminLTE to build a management system to manage the Github search results. Github API has been utilized to scrawl the related results according to keywords and some rules. It proves to be a proper way to detect the information related to your company.

Feature
- Support multi-platform, including Gitlab, Github, Searchcode
- Flexible menu and API permission setting
- Flexible rules and filter rules
- Utilize gobuster to brute force subdomain
- Easily used management system
Download
git clone https://github.com/madneal/gshark.git
cd server
go mod tidy
mv config-temp.yaml config.yaml
go build
./gshark web
If you want to set up the scan service, please run:
./gshark scan
Deployment
For the deployment, it’s suggested to install nginx. Place the dist folder under html, modify the nginx.conf to reverse proxy the backend service. I have also made a video for the deployment in bilibili and youtube. For the deployment in windows, refer here.
The deployment work is very easy. Find the corresponding binary zip file from releases. Unzip and run. Remember to copy the files inside the disk to html folder of nginx.
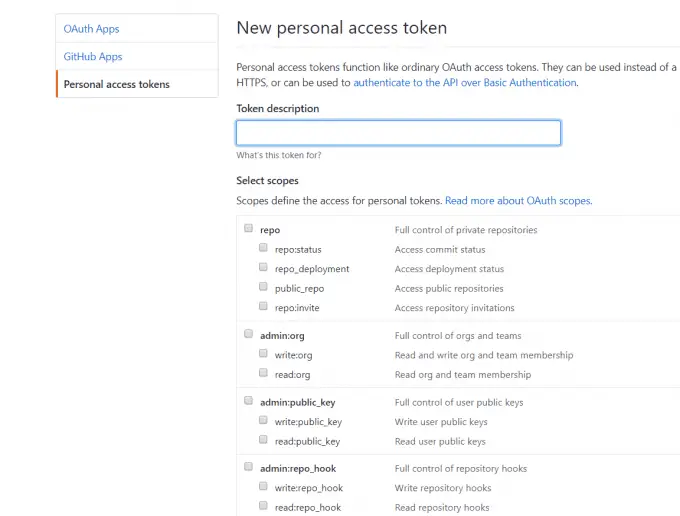
Add Token
To execute the main scan, you need to add a Github token for crawl information in github. You can generate a token in tokens. Most access scopes are enough.
Use
Copyright [2018] [Dong Bing]
Source: https://github.com/madneal/





