findmytakeover: find dangling domains in a multi cloud environment
findmytakeover
findmytakeover detects dangling DNS records in a multi-cloud environment. It does this by scanning all the DNS zones and the infrastructure present within the configured cloud service provider either in a single account or multiple accounts and finding the DNS record for which the infrastructure behind it does not exist anymore rather than using Wordlist. It can easily detect and report potential subdomain takeovers that exist.
This tool is not tested to run on non-commercial Cloud Service Provider regions like AWS GovCloud, Azure Government, or Google for Government but should be able to run without any issues.
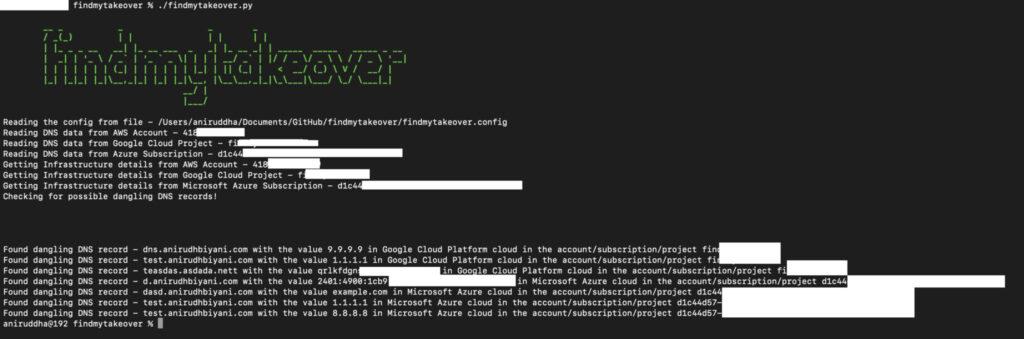
Screenshot
Why?
They are a threat because they allow attackers to host infrastructure behind your domain which can be used for any sort of purpose and get the entire traffic to an attacker-controlled domain with complete access to the domain’s content and resources.
This can become a breeding ground for malicious resources manipulated by an attacker that the domain owner has no control over. This means that the attacker can completely exercise dominance over the domain name to run an illegal service, launch phishing campaigns on unsuspecting victims, and malign your organization’s good name in the market.
Installation
Some dependencies are required to be installed based on the cloud provider that has been configured.
Depending on the cloud provider, you would need permission to read data. The following role would work for various cloud providers –
- Amazon Web Services – ViewOnlyRole and SecurityAudit
- Microsoft Azure – Reader
- Google Cloud – Viewer
git clone https://github.com/anirudhbiyani/findmytakeover.git
cd findmytakeover/
pip3 install -r requirements.txt
Use
The default value of the configuiration file would be the same directory where the tool is located and the configuration file would look like this.
Thee configuration file looks like this.
Limitations
This tool cannot guarantee 100% protection against subdomain takeovers. This will not protect you from dangling NS designations at the moment.
Copyright (C) 2024 anirudhbiyani





