A newly discovered technique in Windows allows malicious scripts to be executed without triggering any user warnings. This method, known as FileFix, has been refined to exploit a vulnerability in how browsers handle saved HTML pages.
The attack was demonstrated by cybersecurity researcher mr.d0x, who had previously showcased the initial version of FileFix. In that iteration, attackers tricked users into pasting a disguised PowerShell command into the Windows Explorer address bar. Once entered, the command executed automatically, making the attack nearly imperceptible to the victim.
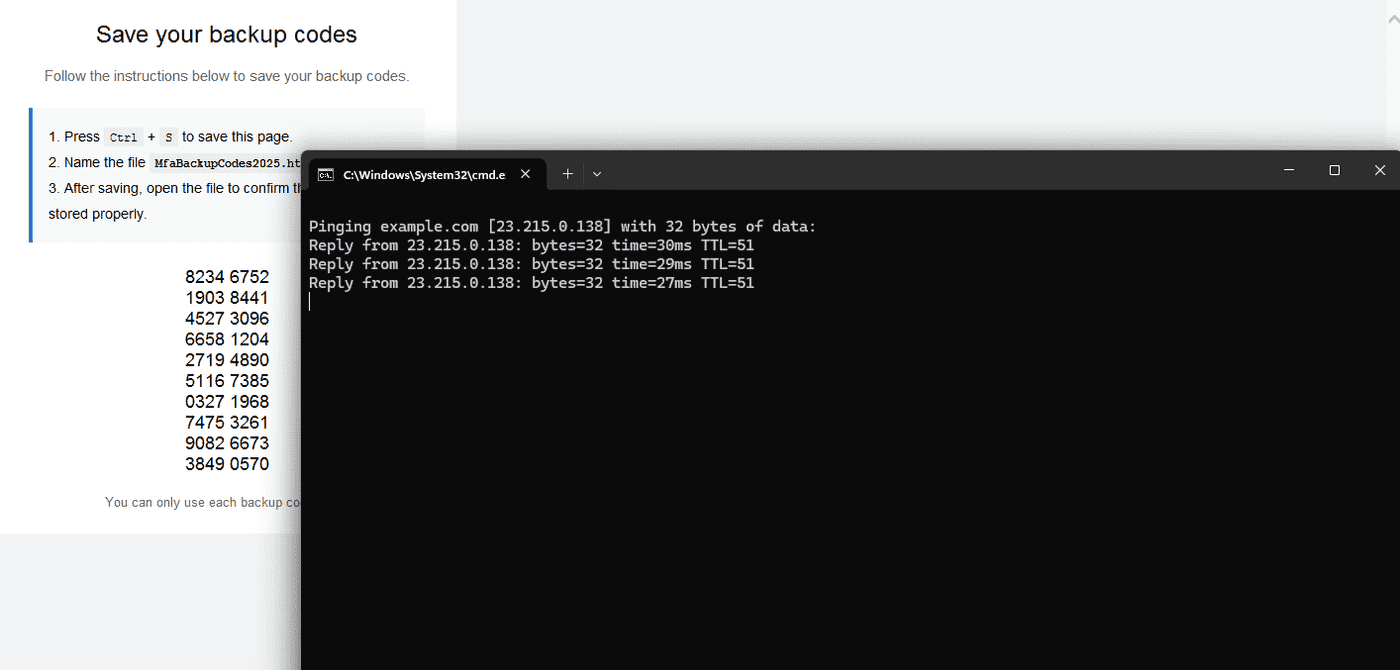
The latest variant of FileFix is even more sophisticated. It enables the execution of malicious scripts while bypassing the Mark of the Web (MoTW) security feature, which is designed to block potentially dangerous files downloaded from the internet. In this version, an attacker uses social engineering to persuade the victim to save an HTML page using the Ctrl+S shortcut, then rename the file extension to .HTA. These files are associated with the legacy, yet still supported, HTML Application (HTA) technology in Windows.
Files with a .HTA extension are essentially HTML-based applications that launch automatically via the system component mshta.exe. This legitimate executable allows HTML content and embedded scripts to run with the same privileges as the current user—making .HTA files a convenient vehicle for executing malicious code.
As mr.d0x demonstrated, when an HTML page is saved in the “Webpage, Complete” format (with the MIME type text/html), it does not receive the MoTW security marker. Typically, MoTW is appended to files downloaded from the internet to alert users and restrict script execution. Without this marker, attackers can evade standard Windows security defenses.
Once the user renames the file—for instance, to “MfaBackupCodes2025.hta”—and opens it, the embedded malicious code executes instantly, without any warnings or prompts. In effect, the victim unwittingly launches the malware.
The most challenging step for attackers remains the social engineering aspect—convincing the user to save the page and modify its extension. However, as mr.d0x notes, this hurdle can be overcome with a convincingly designed fake page. For example, it might impersonate an official website urging users to save two-factor authentication backup codes for account recovery. The page could include detailed instructions such as pressing Ctrl+S, choosing “Webpage, Complete,” and saving the file with a .HTA extension.
If the page appears credible and the user lacks sufficient security awareness to notice the file extension, the likelihood of a successful attack increases dramatically.
As a precaution, experts advise disabling or removing the mshta.exe executable found in C:\Windows\System32 and C:\Windows\SysWOW64. This component is rarely used in routine operations and can be safely deactivated in most environments.
Additionally, enabling the display of file extensions in Windows settings can help prevent format spoofing. It is also advisable to block HTML attachments in emails and exercise heightened caution when saving files from untrusted sources.






