DEEP#GOSU Exposed: New Cyber Espionage Campaign
The cybersecurity firm Securonix has uncovered a new campaign in which hackers employ sophisticated techniques to infiltrate Windows computers and exfiltrate confidential data. Named DEEP#GOSU, the campaign is believed to be linked to the North Korean group Kimsuky.
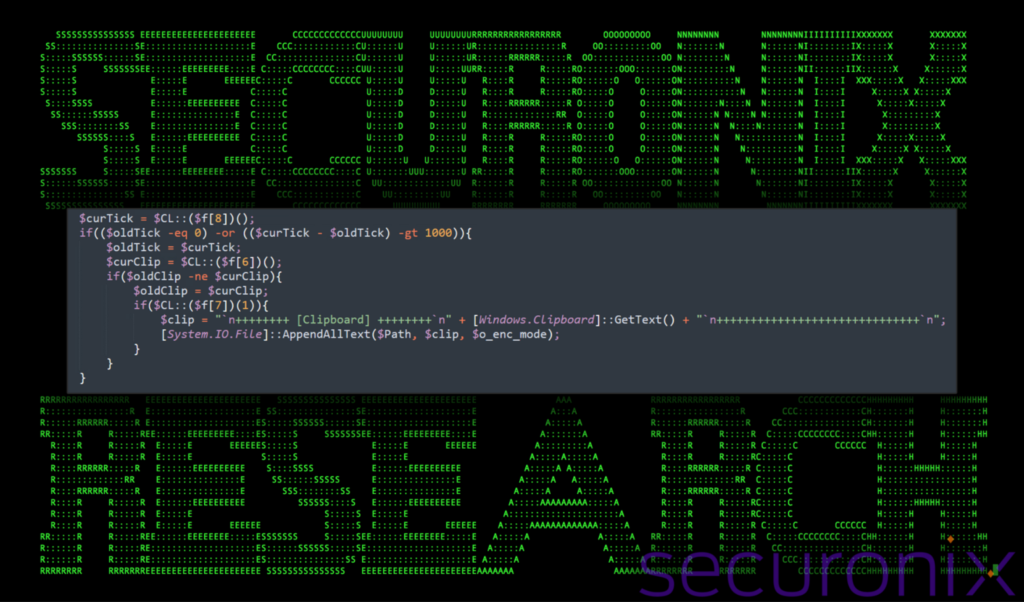
According to the Securonix report, the multi-layered malware possesses capabilities for:
- Stealth operation within Windows systems;
- Keystroke logging;
- Clipboard monitoring;
- Payload execution;
- Data exfiltration;
- Ensuring persistence through the use of remote access software, scheduled tasks, and self-executing PowerShell scripts.
A notable characteristic of this malware is its ability to disguise itself as legitimate traffic by utilizing Dropbox or Google Docs for command and control (C2) operations. This camouflage renders it invisible to network monitoring and facilitates the updating of its functionalities or the downloading of additional modules.
The core of the campaign is the distribution of malicious emails containing a ZIP archive, which appears to enclose a PDF document as a lure. However, upon opening the document, the user unwittingly initiates a PowerShell script that subsequently connects with Dropbox to download and execute further malicious scripts.
These scripts are designed to harvest data from the victim’s computer, including keystroke logging and clipboard monitoring, thereby enabling the attackers to intercept passwords and other sensitive information.
Moreover, to maintain access to and control over infected systems, the attackers employ a variety of techniques, including the creation of scheduled tasks and scripts that automatically execute, thus ensuring their prolonged presence within the system without detection.
Interestingly, the Kimsuky group has previously utilized similar methods, underscoring the necessity for organizations and individuals to remain vigilant in safeguarding their data.





