Deciphering the Grandoreiro Botnet: ESET’s Insight into Cyber Victimology
In a collaborative effort between ESET and the Brazilian Federal Police, significant strides were made to dismantle the activities of the Grandoreiro botnet, which led to victims incurring losses of $3.9 million.
According to police reports, five temporary arrest warrants and thirteen search and seizure warrants were executed across the states of São Paulo, Santa Catarina, Pará, Goiás, and Mato Grosso in Brazil. The investigation was initiated following information from one of the gang’s victims, Spain’s Caixa Bank, which identified the developers and operators of the malicious software in Brazil.
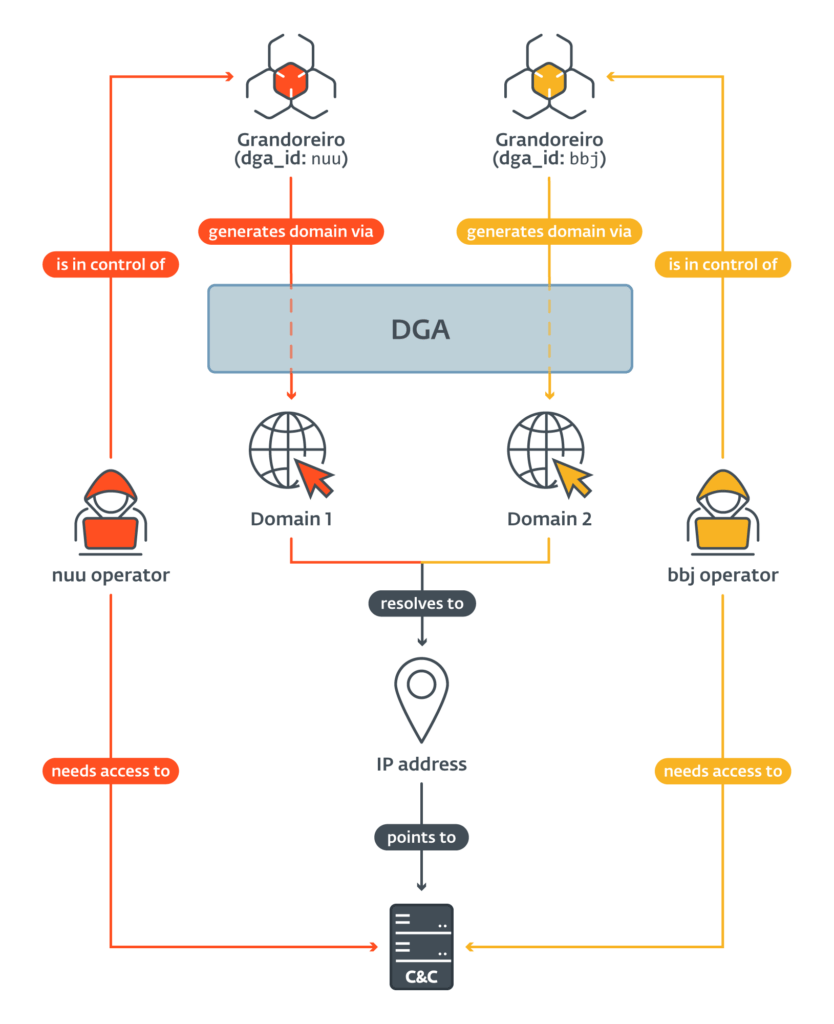
Schema of an IP overlap in two different Grandoreiro DGA configurations | Image: ESET
In the latest assault by Grandoreiro, hackers dispatched phishing emails disguised as court summons or invoices to gain access to victims’ devices. The Grandoreiro malware enables the blocking of the victim’s screen, keystroke logging, mouse and keyboard action simulation, screen broadcasting, and the display of fraudulent pop-up windows.
ESET provided technical analysis, statistical data, as well as information on domain names and IP addresses of command and control (C2) servers. Thanks to the identification of a flaw in the Grandoreiro network protocol, ESET researchers were able to acquire information about the attack’s victims.
ESET systems processed tens of thousands of Grandoreiro samples. The Domain Generation Algorithm (DGA), used since October 2020, generates one main and several backup domains daily. Grandoreiro operators utilized Azure and AWS cloud services to host their network infrastructure. ESET researchers provided data that facilitated the identification of accounts used to configure servers, ultimately leading to the arrest of individuals managing these servers.
Since its inception in 2017, Grandoreiro has specifically targeted the banking systems of Latin America, including Brazil, Mexico, and, from 2019, Spain. From 2023, a shift in focus towards Mexico and Argentina has been observed.
In February 2022, Grandoreiro operators introduced a version identifier into their programs. For instance, from February to June 2022, a new version emerged on average every four days. Studies have shown that Grandoreiro does not operate on a Malware-as-a-Service (MaaS) model but is rather managed by one or several closely cooperating groups.
ESET researchers discovered that the C2 servers of Grandoreiro reveal information about the victims. Data obtained from the servers indicate that most victims used Windows operating systems, with the highest number of attacks occurring in Brazil, Mexico, and Spain.
Thanks to long-term monitoring and analysis of Grandoreiro’s activities, ESET has made a significant contribution to the operation to curb its activities. The company continues to closely monitor the activity of other banking Trojans targeting Latin America, as well as the potential resurgence of Grandoreiro following law enforcement operations.





