Critical Rust Flaw (CVE-2024-24576) Enables Remote Code Execution on Windows
A vulnerability has been discovered within the standard library of the Rust programming language, allowing for the execution of malicious code on Windows systems.
CVE-2024-24576, rated with a CVSS score of 10, stems from a flaw in the mechanism for passing commands and arguments to the operating system. This flaw permits an authenticated attacker to remotely execute malicious code without user interaction, boasting a low complexity of execution.
The Rust Security Response Team was alerted that the Rust standard library fails to properly escape arguments when invoking batch files (with .bat and .cmd extensions) on Windows using the Command API.
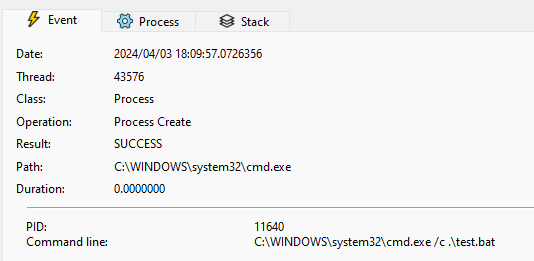
A cybercriminal, having control over the arguments of a launched process, can execute arbitrary commands in the shell by circumventing escaping. The vulnerability is critical when batch files are invoked on Windows with untrusted arguments. Other platforms or use cases are not at risk.
This issue affects all versions of Rust up to 1.77.2 on Windows, if the program code or one of its dependencies invokes and executes batch files with untrusted arguments.
Faced with the complexity of cmd.exe, the Rust security team was unable to find a solution that properly escapes arguments in all cases. As a result, the reliability of the escaping code was enhanced, and the Command API was modified. If the Command API cannot safely escape an argument when creating a process, an InvalidInput error is returned.
Engineer RyotaK from Flatt Security, who discovered the vulnerability and named it BatBadBut, notes that it also affects other programming languages. However, not all of them have received fixes:
- Erlang (documentation update);
- Go (documentation update);
- Haskell (fix available);
- Java (not fixed);
- Node.js (fix to be available soon);
- PHP (fix to be available soon);
- Python (documentation update);
- Ruby (documentation update).
RyotaK recommends moving batch files to a directory not included in the PATH environment variable to prevent their unintended execution. This measure helps avoid their execution without specifying the full path.





