RUBYCARP: Romanian Hackers Target Businesses
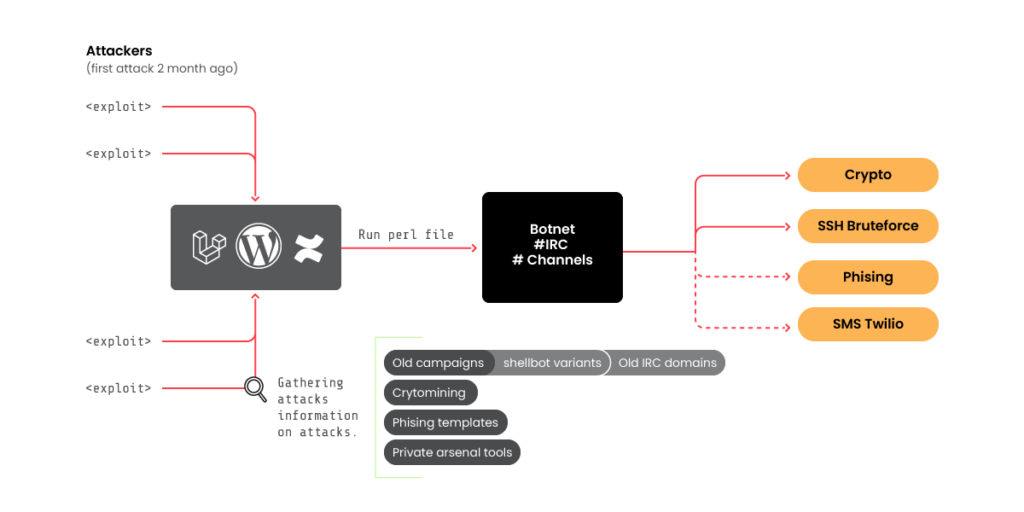
A cybercriminal group from Romania, known under the codename “RUBYCARP,” is exploiting known vulnerabilities and brute force methods to breach corporate networks and servers for financial gain, according to a recent report by Sysdig. Currently, RUBYCARP controls a botnet comprising over 600 infected servers operating through private IRC channels.
Researchers have identified 39 variations of RUBYCARP’s Perl-based botnet payloads, yet only eight were detected on VirusTotal at the time of the report’s publication. The experts also noted that this cybercriminal group has been active for over a decade.
Furthermore, the report mentions some connections between RUBYCARP and the APT group Outlaw, though these links are tenuous, primarily based on the common tactics employed by their botnets.
RUBYCARP’s latest malicious campaign involved targeted attacks against Laravel applications through the remote code execution vulnerability CVE-2021-3129, as well as brute-forcing SSH servers and attacking WordPress sites using databases of account credentials.
Once the malware is installed on an infected server, it connects to an IRC-based C2 server and becomes part of the botnet. Researchers identified three separate botnet clusters—”Juice,” “Cartier,” and “Aridan”—each likely used for different purposes.
The infected devices can be utilized to launch Distributed Denial of Service (DDoS) attacks, phishing, financial fraud, and cryptocurrency mining. RUBYCARP deploys NanoMiner, XMrig, and their own development, C2Bash, for mining cryptocurrencies such as Monero, Ethereum, and Ravencoin by leveraging the computational power of the victims.
The group also employs phishing to steal financial information, deploying ready-made phishing templates on infected servers. In their latest campaign, hackers used templates targeting European companies, including Swiss Bank, Nets Bank, and Bring Logistics.
Although RUBYCARP is not among the largest botnet operators, the group’s ability to operate almost undetected for over a decade speaks to its high level of stealth and operational security.
Beyond managing the botnet, Sysdig reports that the group is also involved in developing and selling hacking tools, indicating an extensive arsenal of malicious software at their disposal.





