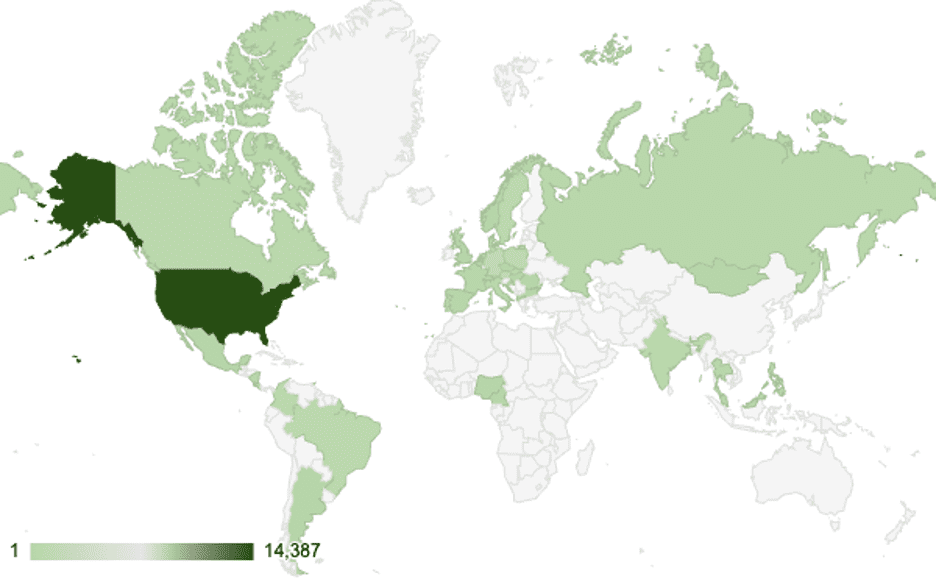
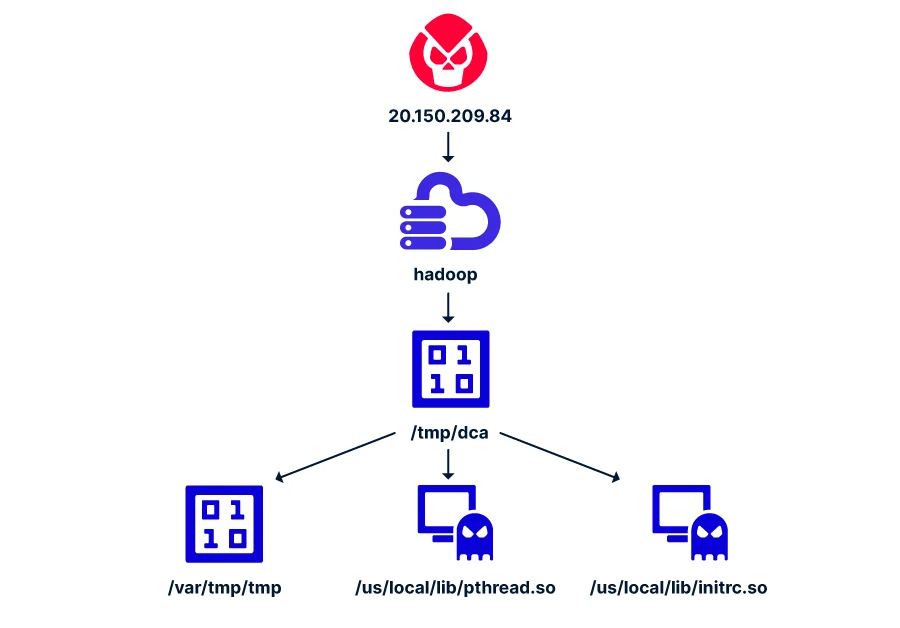
Global Security Alert: Over 1,700 VPN Devices Hacked with GIFFEDVISITOR Web Shell
Earlier this month, we discussed the zero-day vulnerabilities in Ivanti products. A recent analysis by Mandiant revealed that attackers employed five distinct malware families in their assaults, including Zipline, Thinspool Dropper, Wirefire, Lightwire, and...