Category: Information Security
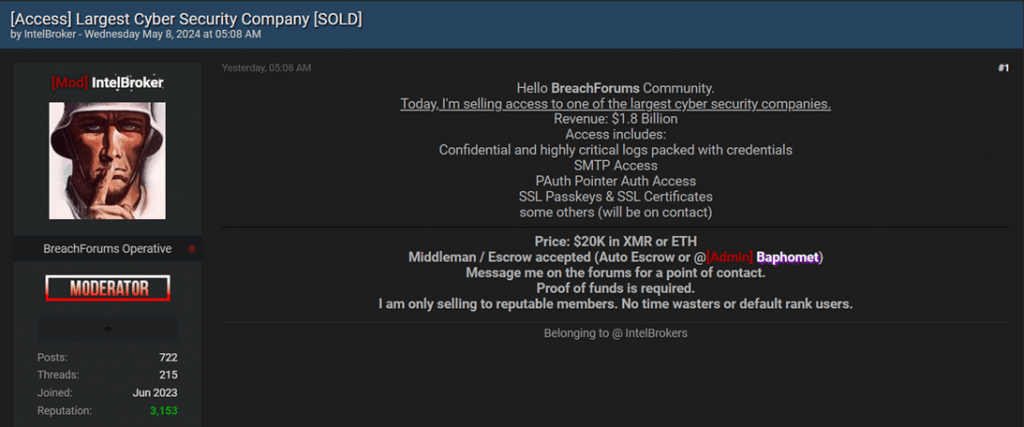
Recently, reports have emerged about a significant cyber incident. A hacker, known by the alias “IntelBroker,” claims to have breached the systems of one of the world’s leading cybersecurity companies, which boasts an annual...
Recently, cybersecurity experts have detected a new version of HijackLoader malware, now featuring enhanced methods to thwart analysis. This upgrade enables the malware to remain undetected within compromised networks for extended periods. Researchers at...
As a result of a data breach from a third-party payroll system, the names, banking details, and in some cases, addresses of approximately 272,000 active duty and veteran members of the British Armed Forces...
Kaspersky Lab has presented a review of changes in the cyber threat landscape for the first quarter of 2024, noting an increase in software vulnerabilities that underscores the importance of timely responses to new...
Researchers from Leviathan Security have identified a severe security threat that impacts nearly all virtual private network (VPN) applications. Dubbed “TunnelVision,” and assigned the identifier CVE-2024-3661 (CVSS score of 7.6 out of 10), this...
Censys has disclosed details of a new cyber espionage campaign, ArcaneDoor, which is believed to be linked to China. The attacks reportedly began in July 2023, with the first incident detected in January 2024....
The intelligence services revived the seized LockBit website to announce new information disclosed by law enforcement agencies. Following the extensive “Chronos” operation, authorities dismantled the LockBit infrastructure and transformed one of its leak sites...
Over 50% of the 90,310 servers utilizing the Tinyproxy proxy tool are vulnerable due to a critical flaw, designated CVE-2023-49606, which has been rated 9.8 out of a possible 10 on the CVSS scale....
Researchers from Kandjii have identified a new piece of malicious software named Cuckoo, targeted at Apple macOS systems. This malware not only establishes a persistent presence in infected systems but also performs a range...
The cyberespionage group APT42 employs social engineering to infiltrate corporate networks and cloud environments in the West and the Middle East. Mandiant, which first documented the group’s activities in September 2022, reports that APT42...
Yaroslav Vasinskyi was sentenced to 13 years and seven months in prison in the United States for his involvement in major cyberattacks using the REvil ransomware virus. In addition to his prison term, the...
Android users have encountered DNS leak issues when switching VPN servers, despite having “Always On VPN” and “Block Connections Without VPN” features enabled. This problem, identified in the latest version of Android 14, was...
In Finland, cybercriminals have intensified their efforts, deploying malicious Android applications aimed at hacking bank accounts, as warned by the local Finnish Transport and Communications Agency (Traficom). These fraudsters are sending SMS messages in...
Cybercriminals are increasingly harnessing Microsoft Graph API to manage malicious software and evade detection systems. According to researchers from Symantec, such actions are designed to facilitate communication with C2 infrastructure hosted on Microsoft’s cloud...
Recently, Aruba Networks, a subsidiary of Hewlett Packard Enterprise (HPE), disclosed information about ten vulnerabilities in its ArubaOS operating system, four of which are classified as critical. These vulnerabilities could potentially allow arbitrary code...
The cybersecurity firm Oversecured has uncovered vulnerabilities in Android applications from Xiaomi, affecting users globally. The investigation revealed 20 vulnerabilities associated with unauthorized access to system data, file theft, and leakage of phone and...