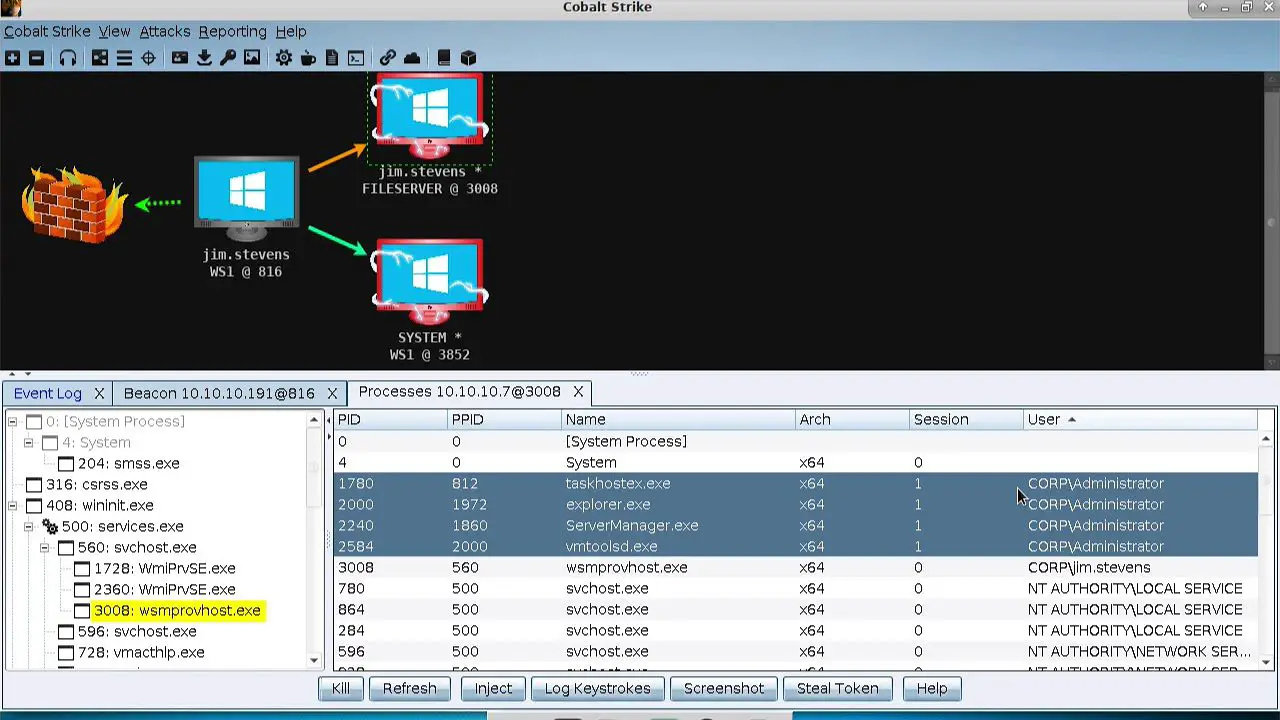
HackBrowserData: Decrypt passwords/cookies/history/bookmarks from the browser
HackBrowserData HackBrowserData is a command-line tool for decrypting and exporting browser data (passwords, history, cookies, bookmarks, credit cards, download history, localStorage and extensions) from the browser. It supports the most popular browsers on the market...