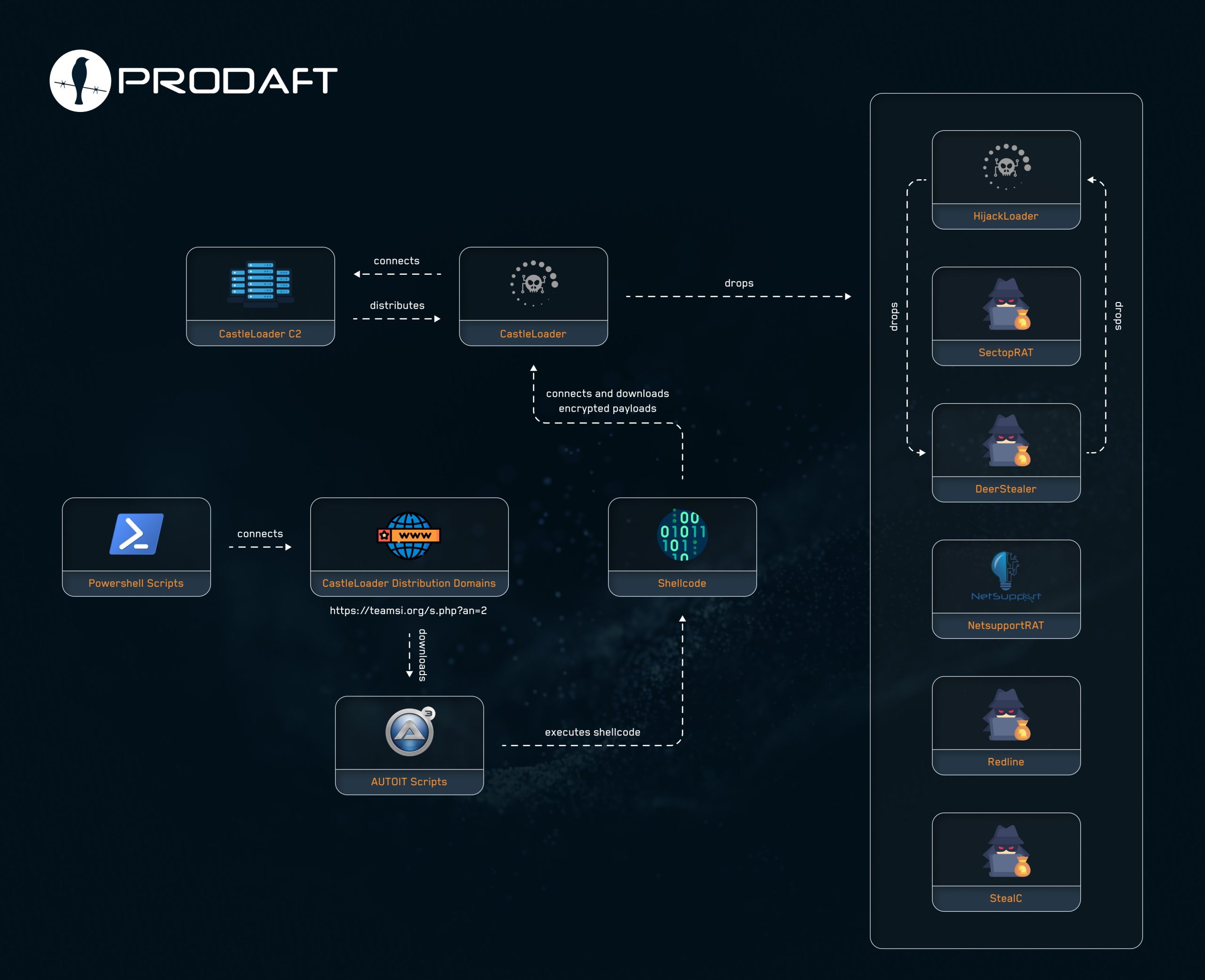
In the first half of 2025, researchers observed the active exploitation of a new malware loader known as CastleLoader. Since its emergence, this tool has become a central element in the distribution infrastructure for a wide range of malicious payloads—from traditional infostealers like RedLine and StealC to sophisticated remote access trojans (RATs) such as NetSupport and SectopRAT. CastleLoader is distinguished not only by its flexible delivery architecture but also by a meticulously designed command-and-control (C2) infrastructure, styled to resemble a full-fledged campaign management system with features akin to those of malware-as-a-service (MaaS) offerings.
CastleLoader’s primary infection vector continues to be phishing pages designed to mimic Cloudflare Verification screens, employing the so-called ClickFix technique. Victims are typically lured via malicious links—often embedded in Google search results—to landing pages masquerading as legitimate platforms: developer libraries, video conferencing tools like Google Meet, browser updates, or document verification portals. The page appears broken and prompts users with an error message and “recovery” instructions. Clicking on a fake “Verification Step” silently executes a script that copies a malicious PowerShell command to the clipboard via the unsecuredCopyToClipboard() function. Trusting the on-screen instructions, the user then pastes this command into the Run dialog and executes it manually.
This action triggers the CastleLoader payload. The PowerShell command provided to the user resembles the following:
This sequence downloads a ZIP archive containing the malicious payload from CastleLoader’s delivery domain (e.g., teamsapi.net), extracts it to a new directory, and executes an AutoIT script (launch_traffic3.au3) to initiate shellcode execution. The script is executed twice to ensure reliability. Within AutoIT resides a DLL-based shellcode loader that resolves necessary DLLs and APIs using an embedded hashing algorithm, subsequently connecting to the C2 server to retrieve additional payloads. Notably, AutoIT is employed not as a supporting tool but as the core mechanism for in-memory code injection and execution.
CastleLoader campaigns vary in the malware they deliver depending on the objectives. Analysts have identified campaigns involving infostealers such as StealC, RedLine, and DeerStealer, alongside RATs like NetSupport and SectopRAT. In some instances, CastleLoader has also been used to distribute other loaders, including HijackLoader—positioning it as a modular platform for cascading payload deployment.
In addition to ClickFix, threat actors employ a secondary distribution strategy involving fake GitHub repositories. These impersonate legitimate development tools and contain malicious builds disguised as popular software releases. A prominent example includes the SSMS-lib repository, which claimed to offer a version of SQL Server Management Studio but instead distributed CastleLoader via the Releases section—capitalizing on developers’ trust in GitHub and their tendency to execute installation commands without verifying source integrity.
Analysis indicates that the same malware samples are being propagated both via CastleLoader and other loader families. For example, a HijackLoader sample (Swi_Compiler.exe, hash: aafcf3fc0eb947759e1c97917a6533a4) was concurrently detected in a DeerStealer campaign (hash: 890eb981dbc0c4b11a386b3b668a7e17, domain: bytehub.asia) and via CastleLoader (hash: d195e39044641f3b1f74843318bca182, domain: teamsi.org). This overlap suggests shared infrastructure or collaboration between threat actor groups.
Between May and July 2025, researchers recorded 1,634 download attempts via CastleLoader, with 469 resulting in successful infections—yielding an infection rate of nearly 29%, underscoring the scheme’s efficiency despite modest click-through volume.
CastleLoader’s network traffic reveals connections to a broad array of distributed domains, including compromised websites and legitimate file-hosting services, enhancing its resilience against targeted takedowns and complicating attribution.
The loader employs a proprietary C2 management panel labeled version 1.1 Alpha, designed with a multipage interface comprising sections such as Installs, Delivery, Tasks, Campaigns, Visits, and Statistics.
- Installs logs all infected machines, detailing IP addresses, campaign names (“Traffics”), unique identifiers, user and computer names, domain affiliation, and Windows version. Operators can track payload installations and manually trigger client reinstalls or removals.
- Delivery functions as the malware repository, with each sample annotated by file name, campaign label, and distribution method. Three deployment modes are supported:
- Common deployment
- Register visit tracking
- Visit requirement enforcement
Operators can enable or disable samples, track download metrics, and manage file lifespans.
- Tasks allows operators to configure delivery parameters such as URL, installation path, and execution method—often embedding PowerShell code directly. Geographic targeting is also supported, with options to include or exclude specific regions. Tasks may be containerized using Docker to thwart analysis, with support for automatic ZIP extraction and elevated privilege execution.
- Campaigns defines malware behavior, including admin rights escalation, anti-analysis (e.g., VM detection), restart blocking, fake error display, and redirections—facilitating stealth and evasion.
- Visits tracks all download URL accesses, logging IP, geolocation, campaign name, and User-Agent—data used to refine targeting for future campaigns.
CastleLoader has not been observed for sale on darknet forums, suggesting its use is confined to a limited circle of operators or is privately distributed. Its robust control panel, diverse delivery channels, and resistance to mitigation point to a highly competent and organized threat actor group. With over 400 confirmed infections across critical targets, including U.S. government systems, CastleLoader rightfully ranks among the most formidable active malware loaders of 2025.





