Bifrost Trojan Targets Linux with VMware Deception
A new Linux version of the Bifrost remote access trojan has emerged, employing a suite of novel camouflage techniques. Among its primary tools is a deceptive domain, mimicking the legitimate VMware.
First identified two decades ago, Bifrost stands as one of the oldest RAT-type threats in operation. It infects users through malicious email attachments or websites distributing malware, subsequently harvesting confidential information from the compromised computer.
Researchers at Palo Alto Networks have recently documented a significant surge in Bifrost activity. An investigation was launched, revealing that perpetrators are now deploying an enhanced version of the malware.
The latest analyses of Bifrost samples by Unit 42 analysts have unveiled several intriguing updates that enhance the trojan’s stealth and expand its capabilities.
Foremost, the command and control server, which the trojan communicates with, utilizes the domain “download.vmfare[.]com,” eerily reminiscent of VMware. This allows it to evade detection with ease. A public DNS resolver from Taiwan is employed to resolve the deceptive domain.
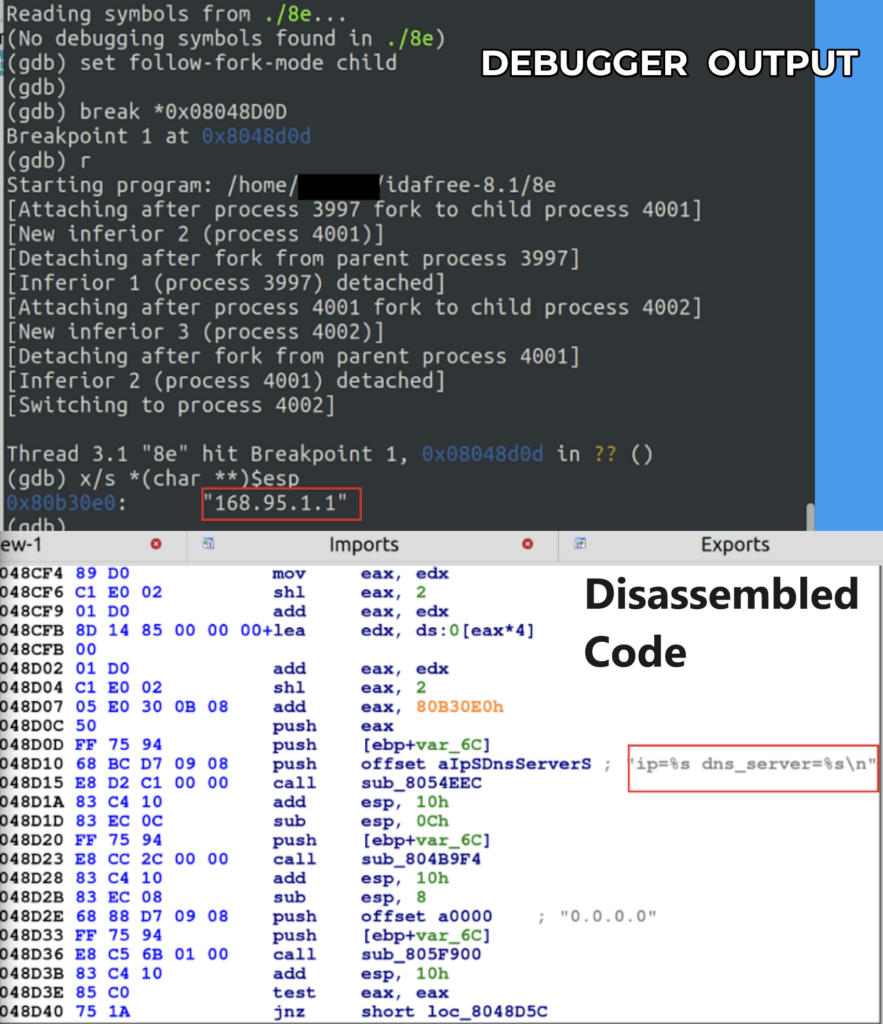
Debugger output and disassembled code revealing the malware contacting a public DNS resolver at 168.95.1[.]1.
Another innovation highlighted in the report is the ARM version of Bifrost, equipped with the same functionalities as the analyzed x86 samples.
The characteristics of these builds indicate the attackers’ intention to broaden their impact to ARM architectures, which are currently proliferating in various environments.
Although Bifrost may not rank among the most sophisticated threats or widely spread malware, the discoveries made by the Unit 42 team call for heightened vigilance.





