Attack Flow: Illuminating the Anatomy of Cyber Threats
Attack Flow
The Attack Flow project helps defenders move from tracking individual adversary behaviors to tracking the sequences of behaviors that adversaries employ to move towards their goals. By looking at combinations of behaviors, defenders learn the relationships between them: how some techniques set up other techniques, or how adversaries handle uncertainty and recover from failure. The project supports a wide variety of use cases: from the blue team to the red team, from manual analysis to autonomous response, and the front-line worker to the C-suite. Attack Flow provides a common language and toolset for describing complex, adversarial behavior.
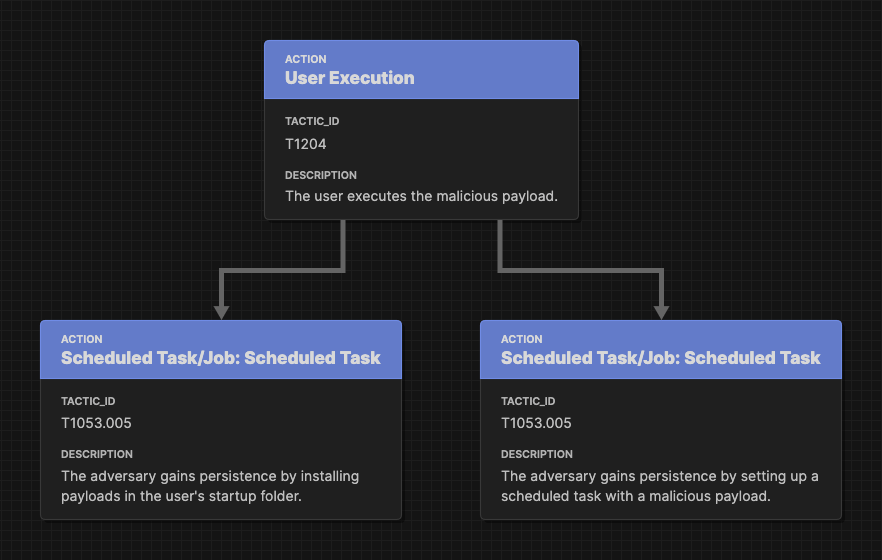
The attack branches out to show that the adversary has multiple persistence techniques
Who is Attack Flow For?
This project is targeted at any cyber security professional seeking to understand how adversaries operate, the impact on their organization, and how to most effectively improve their defensive posture to address those threats. Threat intelligence analysts, security operations, incident response teams, red team members, and risk assessors are some of the groups that can benefit from Attack Flow. This specification facilitates the sharing of threat intelligence, communicating about risks, modeling the efficacy of security controls, and more. The project includes tools to visualize attacks for the benefit of low-level analysis as well as communicating high-level principles to management.
Use Cases
Attack Flow is designed to support many different use cases.
Threat Intelligence
CTI analysts can use Attack Flow to create highly detailed, behavior-based threat intelligence products. The langauge is machine-readable to provide for interoperability across organizations and commercial tools. Users can track adversary behavior at the incident level, campaign level, or threat actor level. Instead of focusing on indicators of compromise (IOCs), which are notoriously inexpensive for the adversary to change, Attack Flow is centered on adversary behavior, which is much more costly to change.
Defensive Posture
The blue team can use Attack Flow to assess and improve their defensive posture, as well as provide leadership with a data-driven case for resource allocation. Attack Flow allows for a realistic risk assessment based on observed adversary sequences of attack, allowing defenders to play out hypothetical scenarios (e.g. table top exercises) with high fidelity. Defenders can reason about security controls over chains of TTPs to determine gaps in coverage, as well as choke points where defenses should be prioritized.
Executive Communications
Front-line cyber professionals can use Attack Flow to roll up highly complicated, technical details of an incident into a visual depiction that aids communication with non-technical stakeholders, management, and executives. This format Attack Flow allows defenders to present their analysis of an attack and their defensive posture strategically while de-emphasizing raw data, technical jargon, and other information that executives do not need to make a business decision. Defenders can use flows to communicate the impact of an attack in business terms (i.e. money) and make a convincing case for new tools, personnel, or security controls to prioritize.
Incident Response
Incident responders can use Attack Flow to improve their incident response (IR) planning and after-action review. After a security incident has occurred, responders can create flows to understand how their defenses failed and where they can apply controls to reduce future risk and enhance threat containment. Mapping a flow will also allow defenders to see where their defenses succeeded and what they should continue to do going forward. Creating attack flows is an easy way to ensure the incident is documented and organizational knowledge is retained for future use. Over time, this will improve defenders’ ability to mitigate and recover from incidents more efficiently.
Adversary Emulation
The red team can use Attack Flow to create adversary emulation plans that focus their security testing on realistic sequences of TTPs informed by the public as well as proprietary intelligence. The red team can leverage a corpus of attack flow to identify common attack paths and TTP sequences. In purple team scenarios, a flow is a very precise way to communicate between attackers and defenders.
Threat Hunting
Threat hunters can use Attack Flow to identify common sequences of TTPs observed in the wild, and then hunt for those same TTP chains in their environment. These flows can guide investigative searches, piecing together techniques and timestamps to construct detailed timelines. Attack Flow can showcase the adversary tools and TTPs that are being used, which can help aid in writing detections against common behaviors and/or adversary toolsets, as well as prioritizing those detections.





