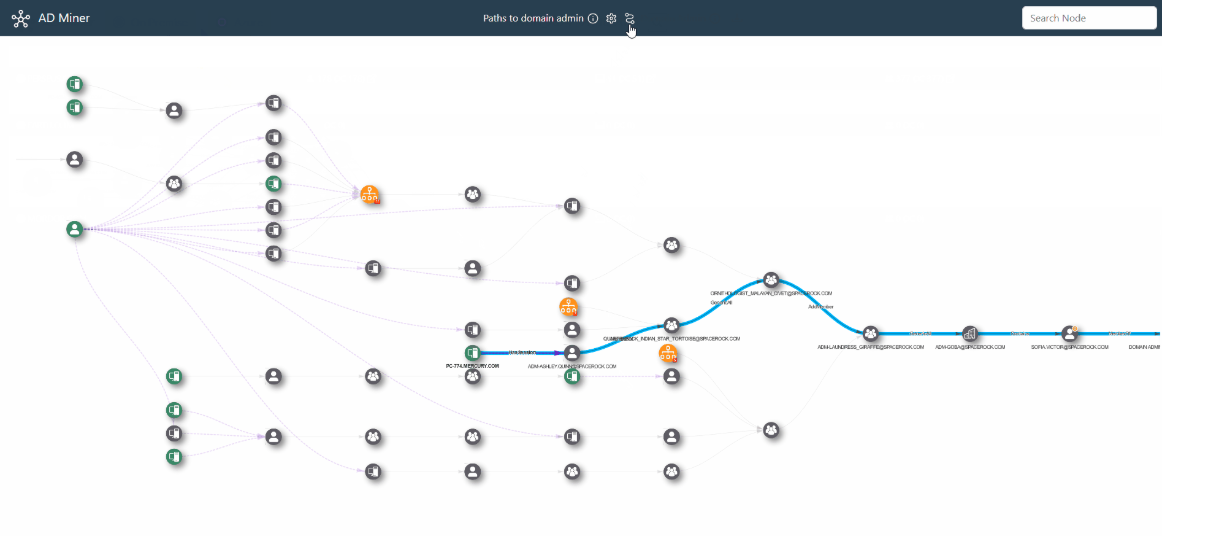
ADMiner
ADMiner is an Active Directory audit tool that leverages cypher queries to crunch data from the BloodHound graph database (neo4j) and gives you a global overview of existing weaknesses through a web-based static report, including detailed listing, dynamic graphs, key indicators history, along with risk ratings.

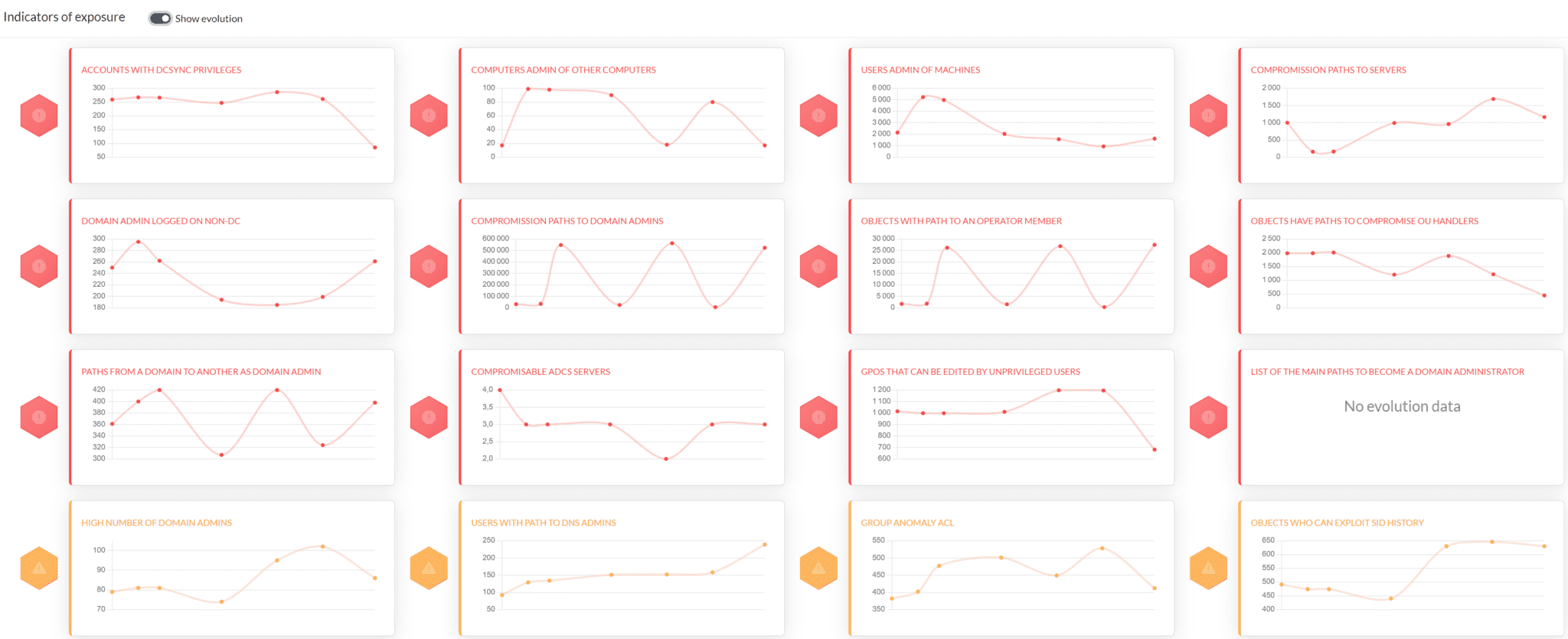
You can also observe indicators over time to help measure mitigation efficiency.
Implemented controls
The following provides a list controls that have already been implemented in AD Miner:
Controls for On-premise
| Category | Description | Category | Description | |
|---|---|---|---|---|
| Kerberos | AS-REP Roastable accounts | Misc | Computers with obsolete OS | |
| Kerberos | Kerberoastable accounts | Misc | Dormant accounts | |
| Kerberos | Kerberos constrained delegation | Misc | Functional level of the domain | |
| Kerberos | Kerberos RBCD against computers | Misc | Ghost computers | |
| Kerberos | Kerberos unconstrained delegations | Misc | Groups without any member | |
| Kerberos | Old KRBTGT password | Misc | OUs without any member | |
| Kerberos | Shadow Credentials on privileged accounts | Misc | Shadow credentials on domain controllers | |
| Kerberos | Shadow Credentials on regular accounts | Misc | Unexpected PrimaryGroupID | |
| Passwords | Access to LAPS passwords | Misc | Users FGPP | |
| Passwords | Computers without LAPS | Permissions | ACL anomalies | |
| Passwords | Objects can read GMSA passwords of administrators | Permissions | Attack paths choke points | |
| Passwords | Password requirement bypass | Permissions | Computers admin of other computers | |
| Passwords | Users with cleartext passwords | Permissions | Cross-domain paths to Domain Admin | |
| Passwords | Users with old passwords | Permissions | Guest accounts | |
| Passwords | Users without password expiration | Permissions | Inadequate access to DCSync privileges | |
| Permissions | Inadequate AdminCount settings | Permissions | Inadequate GPO modifications privileges | |
| Permissions | Inadequate number of domain admins | Permissions | Machine accounts with inadequate privileges | |
| Permissions | Machine accounts with inadequate privileges | Permissions | Non-tier 0 local admin privs on ADCS | |
| Permissions | Objects with SID history | Permissions | Paths to DNS Admins | |
| Permissions | Paths to Domain Admins | Permissions | Paths to Operators Groups | |
| Permissions | Paths to Organizational Units (OU) | Permissions | Paths to servers | |
| Permissions | Paths to the AdminSDHolder container | Permissions | “Pre-Windows 2000 Compatible Access” group | |
| Permissions | Privileged account outside the protected users group | Permissions | RDP access (computers) | |
| Permissions | RDP access (users) | Permissions | Tier-0 violation (sessions) | |
| Permissions | Users that have powerful cross-domain privileges | Permissions | Users with local admin privileges |
Controls for Entra ID
| Category | Description | Category | Description | |
|---|---|---|---|---|
| Entra ID Misc | Azure dormant accounts | Entra ID MS Graph | Direct Controllers of MS Graph | |
| Entra ID Passwords | Entra ID password reset privileges | Entra ID MS Graph | Entra ID accounts not synced on-prem | |
| Entra ID Passwords | Incoherent last password change | Entra ID MS Graph | Synced accounts with disabled twin account | |
| Entra ID Permissions | Access to privileged Entra ID roles | Entra ID Permissions | Privileged accounts on both on-prem and Azure | |
| Entra ID Permissions | Cross on-prem/Entra ID path to tier-0 | Entra ID Permissions | Users possibly related to AADConnect | |
| Entra ID Permissions | Entra ID users with path high value targets |
Install
git clone https://github.com/Mazars-Tech/AD_Miner.git
pip install -r requirements.txt
Use
Copyright (C) 2023 Mazars Cybersecurity Audit & Advisory team
Source: https://github.com/Mazars-Tech/





