ZANSIN: A comprehensive training environment for learning cybersecurity
ZANSIN
ZANSIN is envisioned as a GROUNDBREAKING cybersecurity training tool designed to equip users against the ever-escalating complexity of cyber threats. It achieves this by providing learners with a platform to engage in simulated cyberattack scenarios, supervised and designed by experienced pentesters. This comprehensive approach allows learners to actively apply security measures, perform system modifications, and handle incident responses to counteract the attacks. Engaging in this hands-on practice within realistic environments enhances their server security skills and provides practical experience in identifying and mitigating cybersecurity risks. ZANSIN’s flexible design accommodates diverse skill levels and learning styles, making it a comprehensive and evolving platform for cybersecurity education.
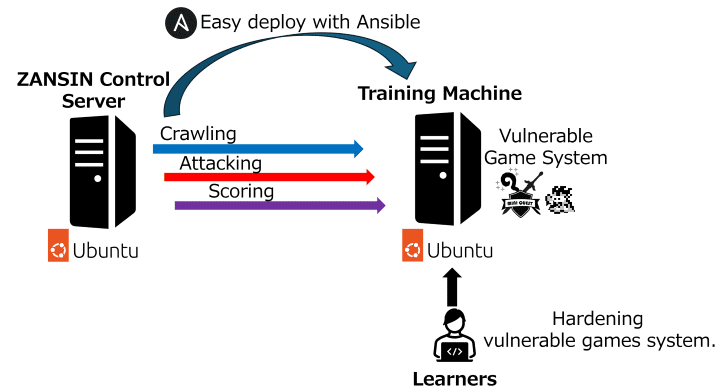
Components
Control Server:
Roles:
- Crawling: The crawler simulates access to the game system on the training machine by a legitimate game user. The crawler periodically accesses the game system during exercises to check if it’s functioning correctly, aggregating results to evaluate the duration the game system operated normally during the exercise.
- Attack: Executes cyber-attacks based on attack scenarios against vulnerabilities in the training machine.
- Scoring: Evaluate whether vulnerabilities on the training machine have been correctly fixed.
Training Machine:
Roles:
- Learners can access the game system, which contains vulnerabilities.
Workflow
- Initially, set up the environment. Prepare two virtual machines (Ubuntu) and download tools from the ZANSIN repository on GitHub. Execute the Ansible command to set up the control server and training machine.
- Learners access the training machine, where the vulnerable game system is operational.
- Once the exercise begins, the control server’s crawler simulates legitimate game users by periodically checking if the game system is functioning correctly. The control server then executes cyber attacks against vulnerabilities in the training machines based on attack scenarios.
- Learners must keep the system operational while responding to cyber-attacks. They also need to identify and fix vulnerabilities in the game system.
- At the end of the exercise, the control server evaluates the time the game system operated correctly and how much the vulnerabilities in the training machine were fixed, assessing the learners’ ability to respond to cyber-attacks.





