Windows 11 now blocks RDP brute force attacks by default
In the underground black market, the sale of remote desktop passwords is also a big deal. There have been cases where the remote desktop passwords of multiple control systems of an airport have been sold. For this reason, Microsoft began to implement the RDP brute-force attack blocking strategy in Windows 11. If 10 failed sign-in attempts, it will be locked for 10 minutes.
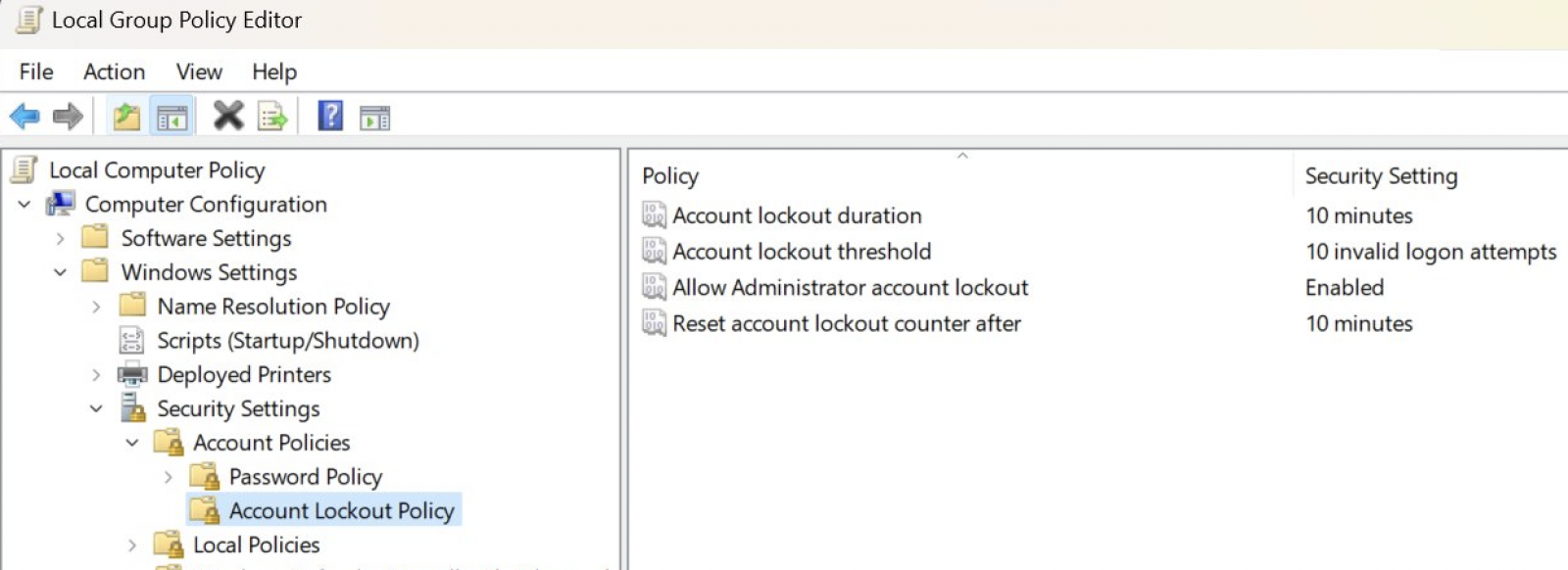
Windows 11 Account Lockout Policy (David Weston)
“Win11 builds now have a DEFAULT account lockout policy to mitigate RDP and other brute force password vectors,” David Weston, Microsoft’s VP for Enterprise and OS Security, tweeted Thursday.
“This technique is very commonly used in Human Operated Ransomware and other attacks – this control will make brute forcing much harder which is awesome!”
Via: bleepingcomputer





