Windows 10 Update can be used to load malicious files
Earlier Microsoft updated the Microsoft Defender anti-virus software. For some reason, Microsoft brought the command line download for this anti-virus software.
The automatic update of the anti-virus software itself does not use the command-line download file function at all. On the contrary, this function may be used by attackers to download malicious files.
The malicious files downloaded by the attacker with the help of this module may be able to bypass the detection of anti-virus software because this useless function carries potential risks.
Although Microsoft issued a statement at the time that the feature will not cause security problems, Microsoft subsequently released an update to quietly delete the command line download function to dispel users’ doubts.
When some researchers analyzed it, it seemed that when Microsoft released the update before, it seemed that it did not just bring the command-line download function to Microsoft Defender.
Even the system update service seems to have a similar function. It is said that the similarity is not a command-line download but the system update service even provides command-line operations.
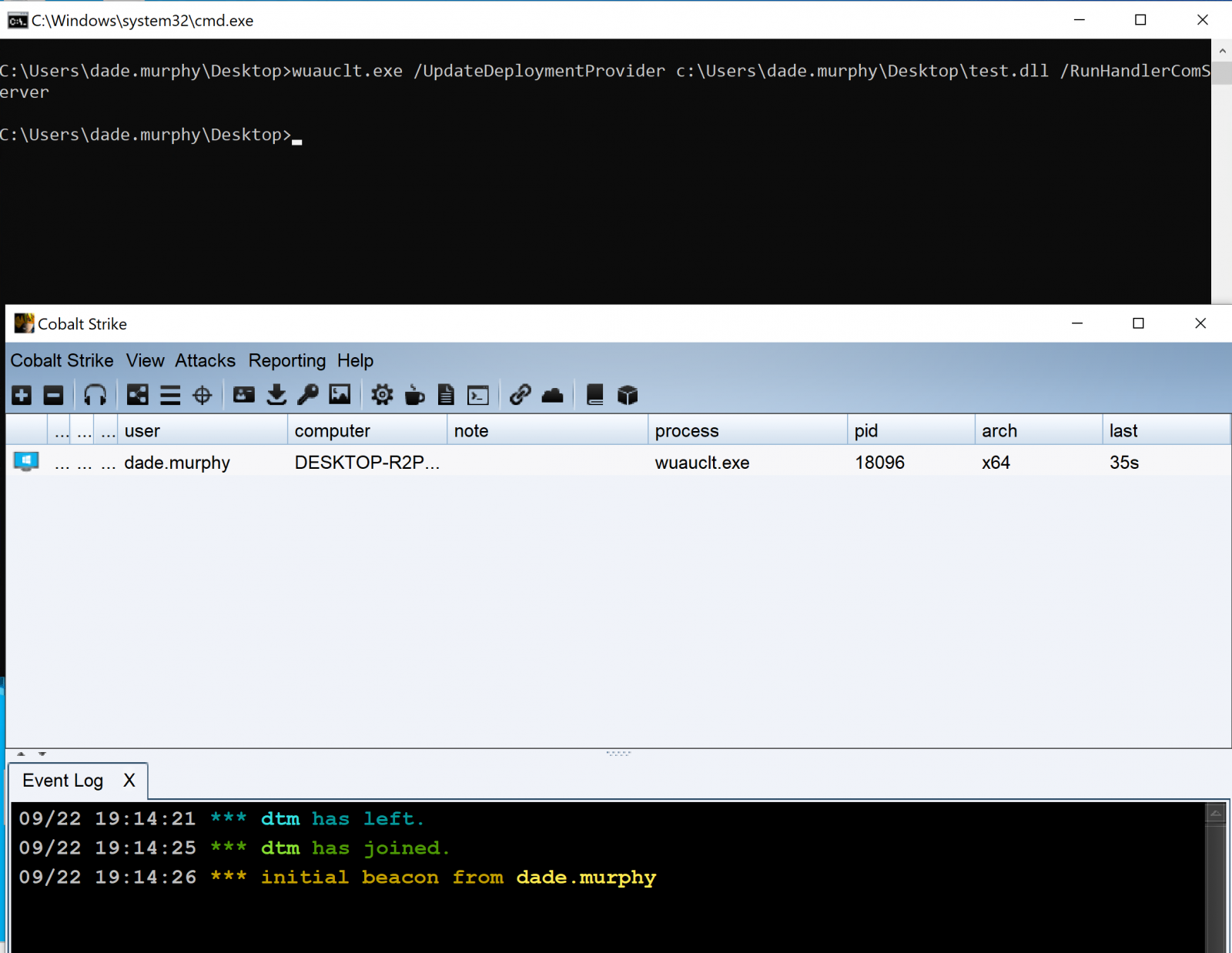
Researchers found that the system update service now brings a new command-line feature, which allows attackers to load wuauclt from any specially crafted DLL through the command line.
wuauclt is the automatic upgrade program pre-installed by Microsoft, and the attacker can directly bypass UAC account control and WDAC application control after calling this function.
Simply put, an attacker can use this function to achieve the persistence of malicious files. It stands to reason that the system update service does not need the function of loading arbitrary DLL library files.
wuauclt.exe /UpdateDeploymentProvider [path_to_dll] /RunHandlerComServer
Image: David Middlehurst
The system update service itself is controlled by Microsoft to perform automatic checks and upgrades. It has extremely high system permissions and can be used to deploy security and functional updates.
It stands to reason that it is safer for the system update service to be controlled by Microsoft, but now Microsoft has added the ability to call arbitrary DLL files.
The key is that under normal circumstances, users do not need to use this feature at all. On the contrary, attackers can use this feature to bypass the user account control mechanism.
Coupled with the previous Microsoft Defender command-line download function, even security researchers are now very confused about what Microsoft’s recent operations are.
It is worth noting that researchers have discovered virus samples that use the system update service to bypass the account control mechanism, indicating that this feature does have security risks.
At present, Microsoft has not responded to the questions raised by the researchers, and it is not clear whether Microsoft will remove this feature like the Microsoft Defender command line download.
Via: bleepingcomputer