Vultur Malware Returns: Beware Fake Bank Calls
Cybersecurity specialists have unearthed a new variant of the Android Trojan, code-named Vultur, endowed with sophisticated remote control capabilities and mechanisms for circumventing protection.
The company ThreatFabric reported the first version of this malicious software in March 2021, and by the end of 2022, the trojan began to spread through dropper applications in Google Play. By the end of 2023, the mobile security platform Zimperium listed Vultur among the top ten most active banking Trojans, noting that nine of its variants targeted 122 banking applications across 15 countries.
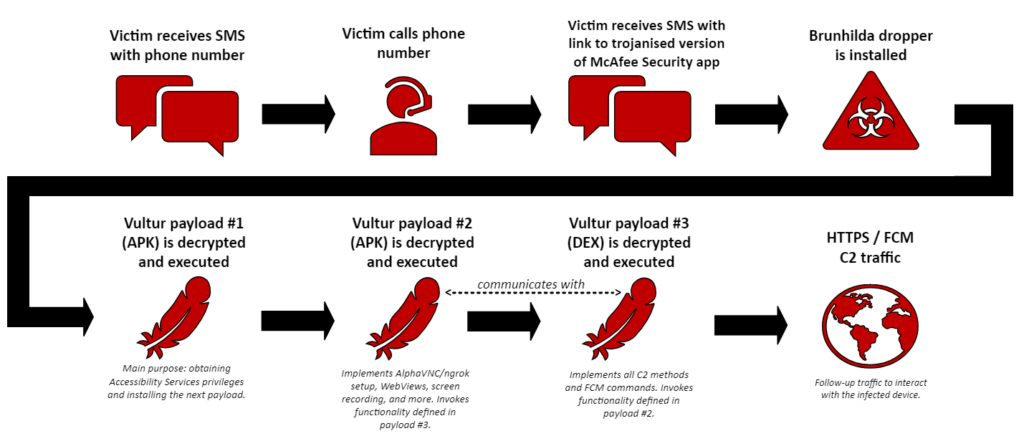
Fox-IT, a division of NCC Group, recently released a detailed report on the new version of Vultur, employing more cunning distribution methods via SMS phishing and calls.
The infection commences with an SMS about an unauthorized banking transaction, followed by an offer of a call for assistance. The fraudulent call culminates with the criminals’ proposition to install mobile antivirus software to safeguard funds. Subsequently, cybercriminals send the victim a link to install what is purportedly the legitimate McAfee Security application, which in reality is the disguised malicious Vultur.
The new Vultur version retains the functionalities of previous iterations, such as screen recording, keylogging, and remote access, but also introduces new features, including file management, the use of Android’s accessibility service to simulate taps and scrolling, the blocking of certain applications, and the display of false notifications.
The malware employs sophisticated mechanisms to circumvent the protection, including encrypted communication with the control server and the use of native code for decrypting the payload, complicating reverse analysis and helping to evade detection.
To minimize the risk of infection by malicious software on Android, it is recommended to download applications only from verified sources, such as the official Google Play app store, and to avoid clicking on links in messages.
It is also crucial to meticulously review the permissions requested by applications and grant access only to those functions essential for their proper operation.





