Void Manticore: Iranian State-Sponsored Hackers Target Israel, Albania
The cybersecurity world is alarmed by new devastating attacks targeting Israel and Albania. These attacks are orchestrated by an Iranian group affiliated with the Ministry of Intelligence and Security (MOIS). Check Point Research specialists have shed light on the tactics of these Iranian hackers.
The group, named Void Manticore (Storm-0842), operates under various pseudonyms in different countries. The most notable aliases include Homeland Justice for attacks in Albania and Karma for operations against Israel.
A high-level timeline of the Void-Scarred Manticores Connection
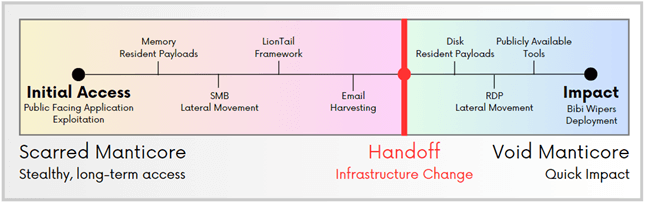
Void Manticore targets various regions, employing unique approaches for each objective. The group’s activities overlap with those of another Iranian group, Scarred Manticore, indicating coordinated and systematic victim selection as part of their work for the Ministry of Intelligence and Security of Iran (MOIS).
Check Point specialists warn that Void Manticore poses a significant threat to anyone opposing Iranian interests. The group utilizes a sophisticated network of pseudonyms, strategic collaboration, and complex attack methodologies.
The group is known for its dual approach to cyberattacks, combining physical data destruction with psychological pressure. Using five different methods, including custom wipers for Windows and Linux, Void Manticore disrupts systems by deleting files and manipulating shared disks.
Specialization in the Destructive Phase
Researchers analyzed the systematic transfer of targets between the two cyber groups. Scarred Manticore is responsible for initial access and data extraction from targeted networks, after which it hands over control to Void Manticore to execute the “destructive phase of the operation.” This collaboration significantly amplifies the scale and impact of the attacks.
Overlaps in actions were observed in attacks on Israel during 2023-2024 and on Albania in 2022.
Simple Yet Effective Tactics
Void Manticore’s attacks are characterized by their simplicity and straightforwardness. They typically use publicly available tools and protocols, such as Remote Desktop Protocol (RDP), Server Message Block (SMB), and File Transfer Protocol (FTP) for lateral movement within networks before deploying malware. In some cases, initial access is achieved by exploiting the CVE-2019-0604 vulnerability in Microsoft SharePoint.
Once inside, hackers deploy wipers Cl Wiper and No-Justice (LowEraser) for Windows and Linux systems. Some wipers target specific files, file types, or applications for selective deletion of critical information (Cl Wiper), while others corrupt the system’s partition table, rendering data inaccessible (No-Justice). The group manually deletes some data, further intensifying the impact of the attacks.
CI Wiper was first used in an attack on Albania in July 2022, alongside LowEraser, which was used in attacks on both Albania and Israel. Recent attacks also utilized BiBi Wiper, available in versions for Linux and Windows, employing sophisticated techniques to damage files and disrupt system operations.
Void Manticore’s attacks indicate a high level of threat to nations opposing Iranian interests. Researchers continue to monitor the activities of these groups to minimize the consequences of their destructive actions.





