Dig ( Domain Information Groper) is a powerful command-line tool that can be used for DNS record queries. Using the dig command, you can query information about various DNS records, including hostname records (A, AAAA), mail exchange records (MX), and alias records (CNAME). Because of its flexibility and ease of use, it has become the most common tool used by
Linux system administrators to troubleshoot DNS issues.
To check if there is a dig command on a Linux system, you can do it in Terminal:
dig -v
If your system does not have its own dig tool, you may be prompted with dig: command not found, you can install it in the following way.
Ubuntu/Debian
sudo apt install dnsutils
CentOS/Fedora
sudo yum install bind-utils
Using dig command
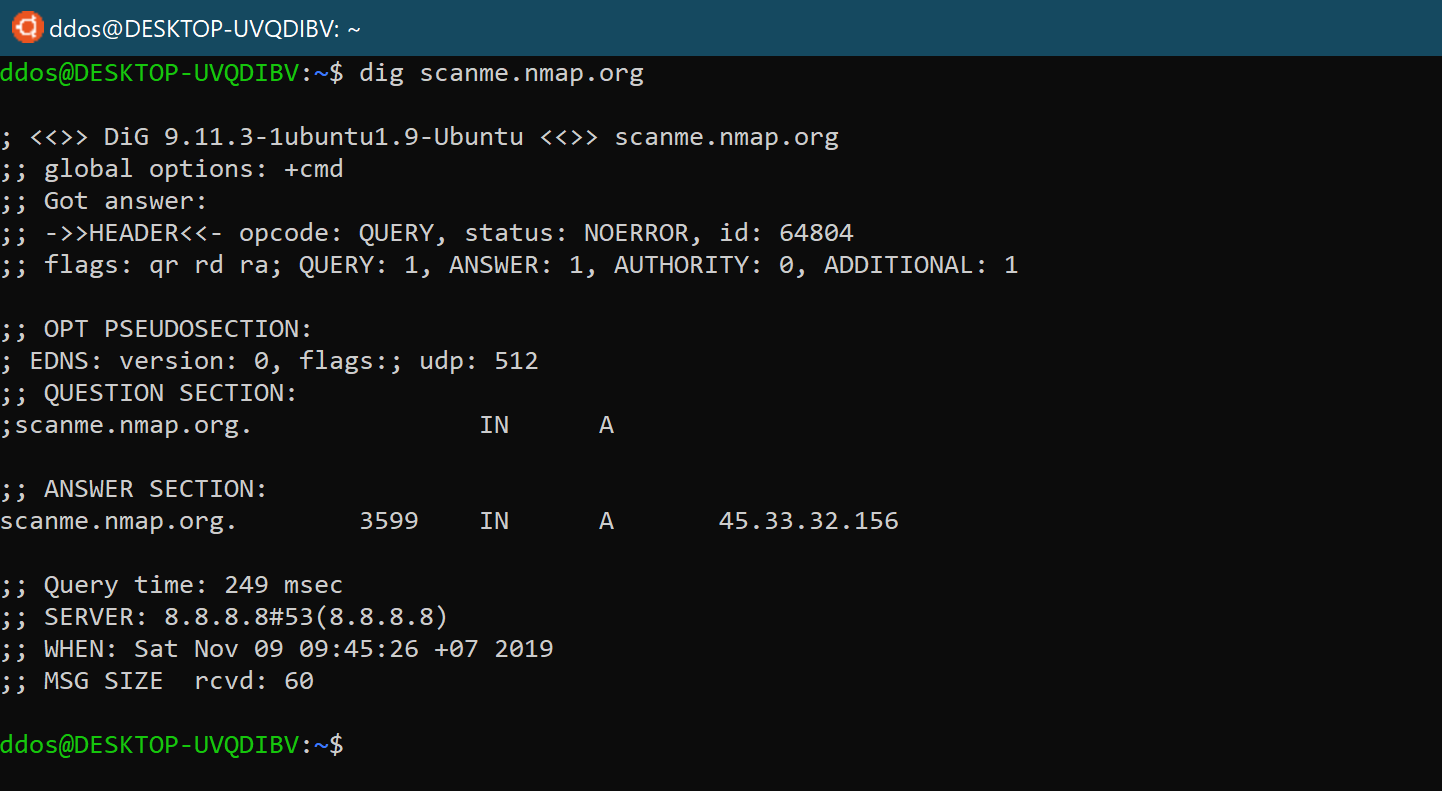
When using dig to query a single host (domain name) without parameters, its output is very detailed, such as query scanme.nmap.org domain name:
Let’s walk through and explain the output of the dig command:
The first part of the output prints out the installed version of dig and the query that was called and the second line shows the global option (by default only cmd).
If you don’t want these lines to be included in the output, you can use the +nocmd option. (This option must be the first argument after the dig command.)
dig +nocmd scanme.nmap.org
The section output includes detailed technical information about the response received from the relevant DNS server. The first line of this section is the “opcode” and “operation status” operated by dig. The “operation status” in the above example is NOERROR, which means that the requested DNS server can be serviced without problems for the query.

This section is displayed when using a newer version of the dig, and you can find more information about the DNS Extension Mechanism (EDNS) in this section of the output.

This part of the output shows what dig is about to query. By default, dig will request an A record.

By default, dig will request an A record. In this case, we can see that scanme.nmap.org points to the IP address 45.33.32.156.

This is the last part of the dig output, which includes statistics about the query.
 In the vast majority of cases, we only use dig to query the corresponding DNS records without too many complicated and irrelevant responses and outputs. In this case, we can use the following two methods.
In the vast majority of cases, we only use dig to query the corresponding DNS records without too many complicated and irrelevant responses and outputs. In this case, we can use the following two methods.
If you only want a short response to a DNS query, you can use the +short parameter, for example:
dig scanme.nmap.org +short
The output will only include the CNAME record and the final A record that was responded to when querying the IP address of scanme.nmap.org.
To get a detailed response to a DNS query, you can first turn off all results with the +noall parameter and then open some results with the +answer parameter.
dig scanme.nmap.org +noall +answer
By default, if no name server is specified, dig will actively use the DNS server listed in the /etc/resolv.conf file for queries. If you want to use a specific DNS server for record queries, you can use @DNS with the DNS server IP address to force a DNS server.
dig scanme.nmap.org @1.1.1.1
Similar to the nslookup command line under Windows, the dig tool also allows users to query the specified DNS record type. The following system geeks will introduce you to the common DNS record types, such as A (IP address), CNAME (alias record), TXT (text record), MX (mail exchange record) and NS (name server).
To get a list of all IP addresses for a domain name, use the a parameter:
dig +nocmd microsoft.com a +noall +answer
To find the Alias Record, use the cname option:
dig +nocmd microsoft.com cname +noall +answer
You can use the txt parameter to retrieve all “TXT records” for a particular domain:
dig +nocmd microsoft.com txt +noall +answer

To get a list of all mail servers for a particular domain, use the mx parameter:
dig +nocmd microsoft.com mx +noall +answer
To find an authoritative name server for a specific domain, use the ns parameter:
dig +nocmd microsoft.com ns +noall +answer
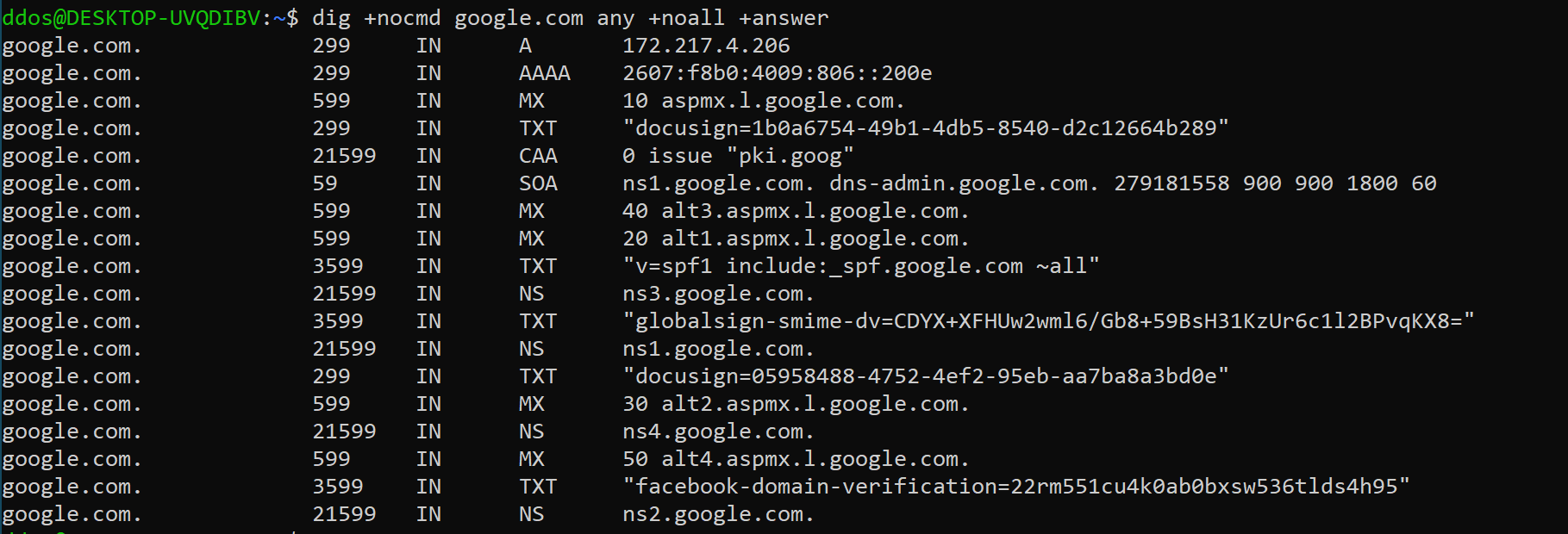
Use the any parameter to get a list of all DNS records for a particular domain:
dig +nocmd google.com any +noall +answer
To query the hostname associated with a specific IP address, use the -x parameter. For example, to perform a reverse lookup on 45.33.32.156, you would use:
dig -x 45.33.32.156 +noall +answer
As you can see from the output, the IP address 45.33.32.156 is associated with the hostname scanme.nmap.org.
If you want to perform a DNS query on a large number of domain names, you can write them all into a text file (one per line), then use the -f parameter, followed by the file name, for example:
dig -f domains.txt any +noall +answer





 In the vast majority of cases, we only use dig to query the corresponding DNS records without too many complicated and irrelevant responses and outputs. In this case, we can use the following two methods.
In the vast majority of cases, we only use dig to query the corresponding DNS records without too many complicated and irrelevant responses and outputs. In this case, we can use the following two methods.