Cyber espionage in Asia is intensifying: researchers at Seqrite Labs have unveiled new insights into the operations of the group UNG0002, also known as Unknown Group 0002. This obscure yet technically adept entity is conducting large-scale campaigns targeting strategically vital sectors across China, Hong Kong, and Pakistan. Its focus encompasses the defense industry, electrical engineering, energy infrastructure, civil aviation, healthcare institutions, universities, IT enterprises, and even the video game sector.
According to the latest report by Seqrite Labs, UNG0002 exhibits a marked preference for employing LNK shortcuts, VBScript files, and post-exploitation tools such as Cobalt Strike and Metasploit. To lure victims, the group distributes deceptive documents disguised as résumés, lending their attacks a convincing veneer of authenticity. The analysis, conducted by researcher Subhajit Singha, highlights the attackers’ methodical approach and remarkable adaptability.
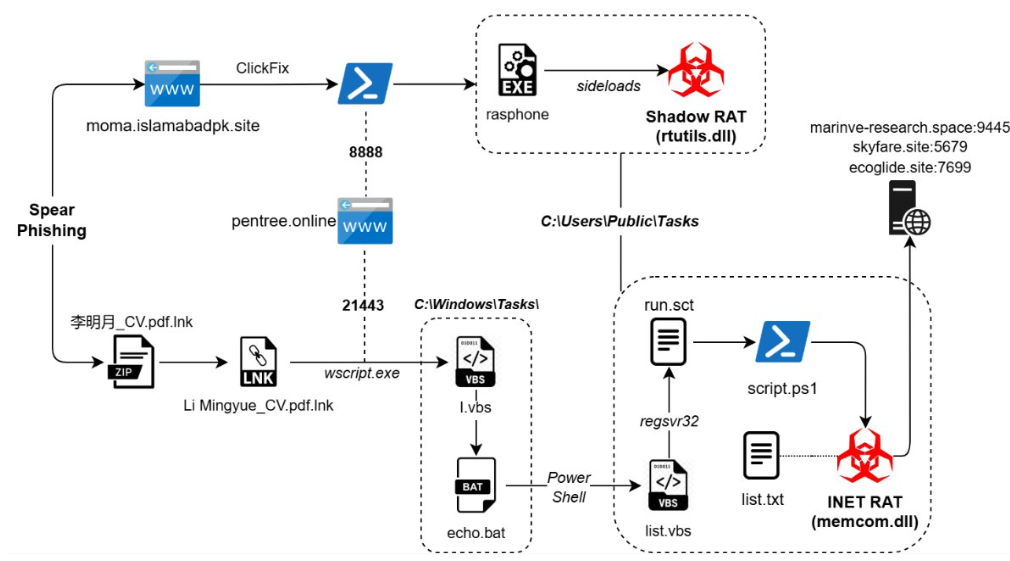
The group has orchestrated two major campaigns—Cobalt Whisper and AmberMist. The former was active from May to September 2024, and the latter spanned January to May 2025. Both operations relied heavily on phishing emails, where malicious ZIP archives and LNK files served as initial infection vectors for complex malware deployment chains.
The Cobalt Whisper operation was first identified in October 2024. At that time, researchers reported that ZIP attachments delivered via email concealed LNK and VBScript files, which, once executed, deployed modules of Cobalt Strike—a powerful post-exploitation framework used to maintain command and control within compromised systems.
In the more recent AmberMist campaign, attackers distributed faux résumés in the form of LNK files. These initiated a multi-stage infection process that culminated in the deployment of the INET RAT and Blister DLL trojans. The former is believed to be a customized variant of the previously documented Shadow RAT spyware, while the latter acts as a shellcode loader to establish remote access.
Of particular interest is an alternative attack scenario observed in January 2025. Victims were redirected to a spoofed website mimicking the Pakistan Ministry of Maritime Affairs. Under the guise of a CAPTCHA verification page, the attackers surreptitiously executed PowerShell commands using a technique known as ClickFix. These commands activated Shadow RAT, creating a covert communication channel with the attackers’ command-and-control infrastructure.
The capabilities of the malware employed in these campaigns are striking. Shadow RAT, for instance, leverages DLL Sideloading and supports remote command execution, rendering it stealthy and difficult to detect by traditional defenses. The attack techniques continue to evolve, and the group’s technical arsenal grows increasingly sophisticated. Yet the infection vectors—phishing emails, spoofed official sites, and contemporary lures—remain consistently effective.
While no direct attribution has been established, circumstantial evidence suggests that UNG0002 may originate from the South or Southeast Asian region. Analysts describe the group as resilient and highly inventive: despite the exposure of some of its tools, it continues to expand its infrastructure, refine its toolkit, and maintain operational momentum.
These developments underscore a growing trend: phishing and DLL Sideloading persist as formidable tools in cyber espionage, while targeted attacks on critical industries remain a strategic axis likely to intensify in the future.




