Plug & Play Peril: UNC4990 Spreads via USB across Italian Industries
In Italy, cybercriminal activity known as UNC4990, which employs infected USB devices to launch attacks across various sectors including healthcare, transportation, construction, and logistics, was reported by Mandiant on January 30.
Active since late 2020 and presumably based in Italy, UNC4990 leverages Italian infrastructure for command and control (C2) of their operations. Their primary mode of attack involves the dissemination of malicious software via USB, subsequently leading to the installation of the EMPTYSPACE loader.
The perpetrators utilize platforms such as GitHub, Vimeo, and Ars Technica to host additional payloads. Malicious files are downloaded and decrypted from these sites using PowerShell.
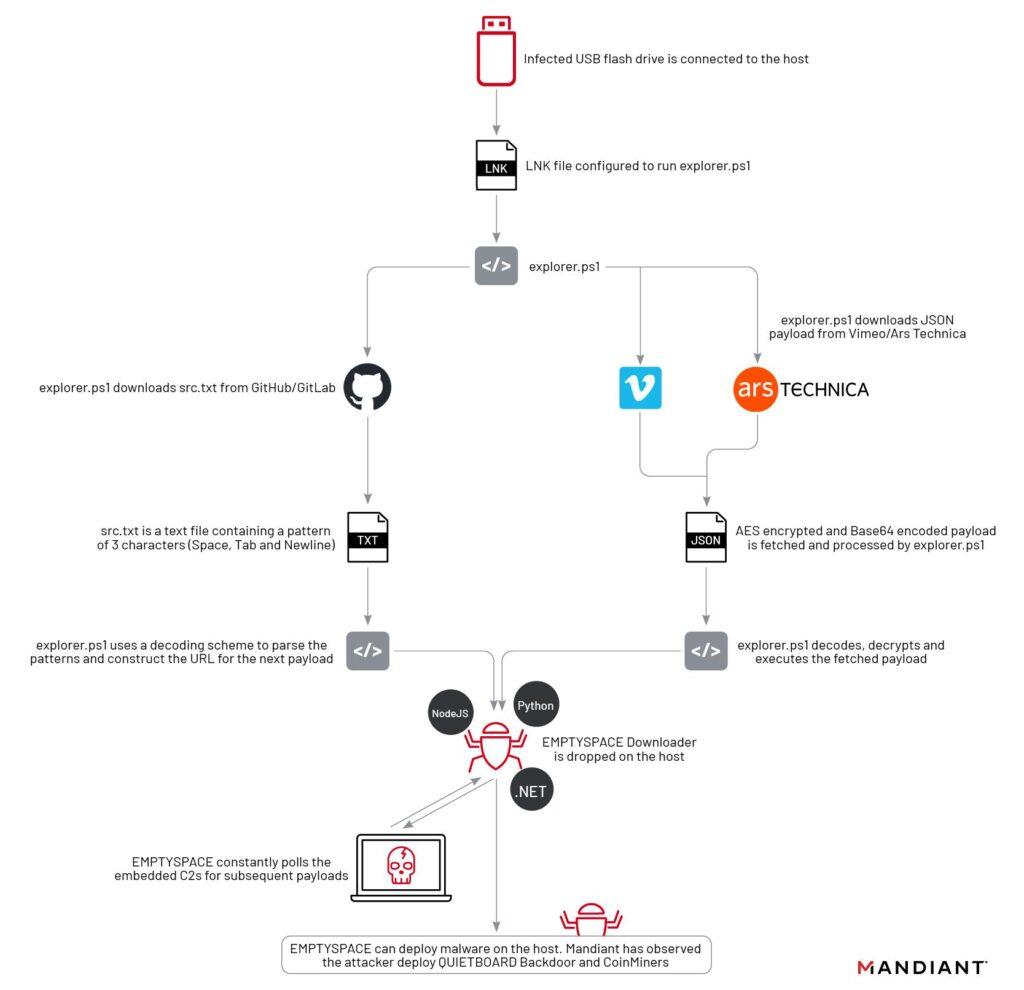
Infection chain
The ultimate objectives of UNC4990 remain ambiguous, though, in one instance, researchers discovered the use of a cryptocurrency miner, hinting at the group’s financial motivations.
This malicious campaign was also documented in early December by researchers from Fortgale and Yoroi. The infection process begins when a victim executes a malicious LNK file on a removable USB device, triggering a PowerShell script that downloads EMPTYSPACE from a remote server.
Yoroi identified four variants of EMPTYSPACE, developed in Golang, .NET, Node.js, and Python. These variants are used to download subsequent stages of malware from a C2 server, including QUIETBOARD.
QUIETBOARD, a Python backdoor, offers a broad range of capabilities, from executing arbitrary commands to altering cryptocurrency wallet addresses and gathering system information. The backdoor can also propagate to removable drives and capture screenshots.
While the attackers use popular websites to host their malware, Mandiant experts assure that the content of these sites does not pose a direct threat to regular users, as the programs are harmless in isolation.
The analysis of EMPTYSPACE and QUIETBOARD also reveals that the attackers employ a modular approach in developing their tools, showcasing an experimental mindset and adaptability.
The cyber incident under review proves that seemingly outdated methods of compromise, such as the distribution of infected USB drives, remain effective, and built-in protective systems often fail to recognize them.
Such attacks underscore the necessity for continuous enhancement of cybersecurity measures to stay ahead of hackers’ actions. Only a comprehensive approach, encompassing technology, processes, and human factors, can ensure an adequate level of security.





