Tsunami
Tsunami is a general-purpose network security scanner with an extensible plugin system for detecting high severity vulnerabilities with high confidence.
Why Tsunami?
When security vulnerabilities or misconfigurations are actively exploited by attackers, organizations need to react quickly in order to protect potentially vulnerable assets. As attackers increasingly invest in automation, the time window to react to a newly released, high-severity vulnerability is usually measured in hours. This poses a significant challenge for large organizations with thousands or even millions of internet-connected systems. In such hyperscale environments, security vulnerabilities must be detected and ideally remediated in a fully automated fashion. To do so, information security teams need to have the ability to implement and roll out detectors for novel security issues at scale in a very short amount of time. Furthermore, it is important that the detection quality is consistently very high. To solve these challenges, we created Tsunami – an extensible network scanning engine for detecting high severity vulnerabilities with high confidence in an unauthenticated manner.
Goals and Philosophy
- Tsunami supports a small manually curated set of vulnerabilities
- Tsunami detects high severity, RCE-like vulnerabilities, which often actively exploited in the wild
- Tsunami generates scan results with high confidence and minimal false-positive rate.
- Tsunami detectors are easy to implement.
- Tsunami is easy to scale, executes fast, and scans non-intrusively.
How Tsunami Scan Works
Overview
As of today, Tsunami follows a hardcoded 2-step process when scanning a publicly exposed network endpoint on the potential improvement on the workflow):
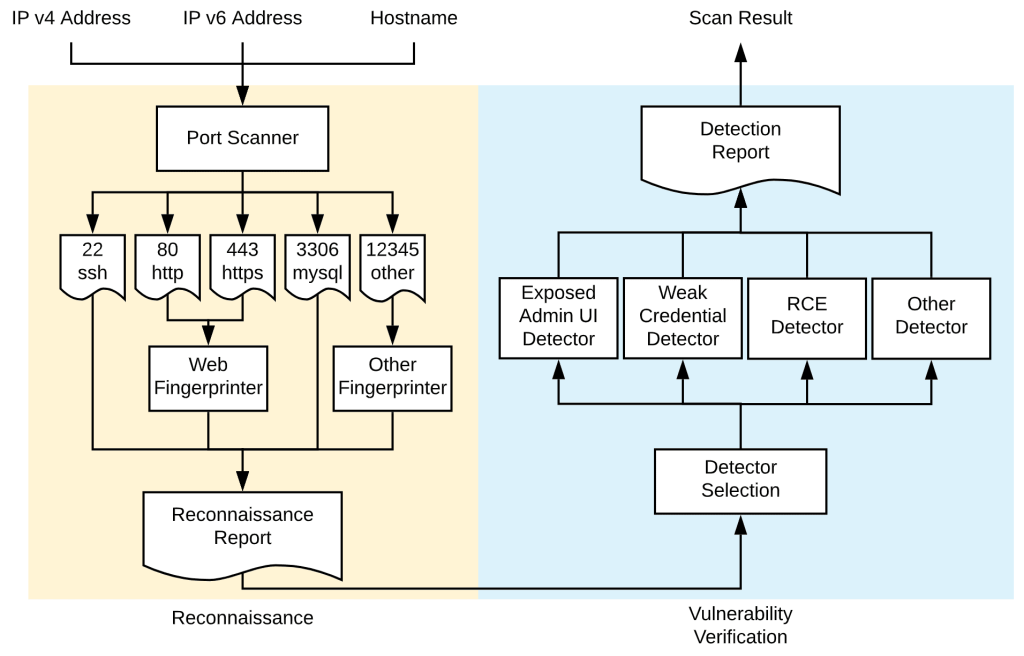
- Reconnaissance: In the first step, it identifies open ports and subsequently fingerprints protocols, services, and other software running on the target host via a set of fingerprinting plugins. To not reinvent the wheel, it leverages existing tools such as nmap for some of these tasks.
- Vulnerability Verification: Based on the information gathered in step 1, it selects all vulnerability verification plugins matching the identified services and executes them in order to verify vulnerabilities without false positives.
Overall Scanning Workflow
The following diagram shows the overall workflow for a Tsunami scan.
Reconnaissance
In the reconnaissance step, Tsunami probes the scan target and gathers as much information about the scan target as possible, including:
- open ports,
- protocols,
- network services & their banners,
- potential software & corresponding version.
Tsunami performs the Reconnaissance step in 2 separate phases.
Port Scanning Phase
In the port scanning phase, it performs port sweeping in order to identify open ports, protocols, and network services on the scan target. The output of Port Scanning is a PortScanReport protobuf that contains all the identified NetworkServices from the port scanner.
PortScanner is a special type of Tsunami plugins design for Port Scanning purpose. This allows users to swap the port scanning implementations. To not reinvent the wheel, users could choose a Tsunami plugin wrapper around existing tools like nmap or masscan. You may find useful PortScanner implementations can be found in the tsunami-security-scanner-plugins repo.
Fingerprinting Phase
Usually, port scanners only provide very basic service detection capability. When the scan target hosts complicated network services, like web servers, the scanner needs to perform further fingerprinting work to learn more about the exposed network services.
For example, the scan target might choose to serve multiple web applications on the same TCP port 443 using nginx for reverse proxy, /blog for WordPress, and /forum for phpBB, etc. Port scanner will only be able to tell port 443 is running nginx. A Web Application Fingerprinter with a comprehensive crawler is required to identify these applications.
ServiceFingerprinter is a special type of Tsunami plugin that allows users to define fingerprinters for a specific network service. By using filtering annotations (see how to apply my plugins to certain types of services / software?), it will be able to automatically invoke appropriate ServiceFingerprinter s when it identifies matching network services.
Reconnaissance Report
At the end of the reconnaissance step, Tsunami compiles both the port scanner outputs and service fingerprinter outputs into a single ReconnaissanceReport protobuf for Vulnerability Verification.
Vulnerability Verification
In the Vulnerability Verification step, Tsunami executes the VulnDetector plugins in parallel to verify certain vulnerabilities on the scan target based on the information gathered in the Reconnaissance step. VulnDetector‘s detection logic could either be implemented as plain Java code or as a separate binary/script using a different language like python or go. External binaries and scripts have to be executed as separate processes outside of Tsunami using Tsunami’s command execution util.
Detector Selection
Usually, one VulnDetector only verifies one vulnerability and the vulnerability often only affects one type of network service or software. In order to avoid doing wasteful work, Tsunami allows plugins to be annotated by some filtering annotations (see how-to guide for details) to limit the scope of the plugin.
Then before the Vulnerability Verification step starts, Tsunami will select matching VulnDetectors to run based on the exposed network services and running software on the scan target. Non-matching VulnDetectors will stay inactive throughout the entire scan.
Install & Use
Copyright (C) 2020 Google





