ToddyCat APT: A Cyber Threat to Asia-Pacific
Specialists from Kaspersky Lab have discovered that the hacking group ToddyCat employs a diverse array of tools to maintain access to compromised systems and steal valuable data. Active since December 2020, the group primarily targets government and defense organizations in the Asia-Pacific region.
The primary hacking tool is a passive backdoor named Samurai, which allows remote control over infected hosts. According to researchers Andrey Gunykin, Alexander Fedotov, and Natalia Shornikova, the hackers have highly automated the data collection process from a large number of hosts, employing several alternative methods for continuous access and system monitoring.
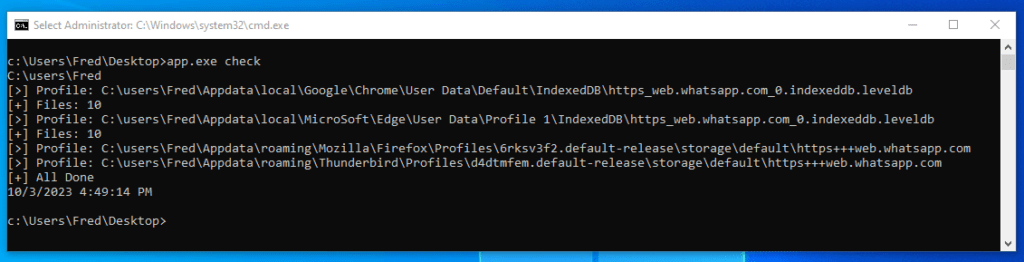
WAExp “check” output with results for Chrome, Edge, Firefox and Thunderbird
In addition to the Samurai malware, ToddyCat also deploys additional tools for data exfiltration, such as LoFiSe and Pcexter, for gathering data and uploading archived files to Microsoft OneDrive. Additional software includes data tunneling using various applications:
- A reverse SSH tunnel using OpenSSH;
- SoftEther VPN, disguised as innocuous files like “boot.exe,” “mstime.exe,” “netscan.exe,” and “kaspersky.exe”;
- Ngrok and Krong for encrypting and rerouting command and control traffic;
- FRP, a Golang-based fast reverse proxy client;
- Cuthead, a .NET executable for searching documents by extension, name, or modification date;
- WAExp, a .NET program for capturing data from the WhatsApp web application and storing it in an archive;
- TomBerBil for extracting cookies and credentials from web browsers, including Google Chrome and Microsoft Edge.
These tools allow for multiple simultaneous connections with infected endpoints and controlled infrastructure, serving as a fallback mechanism to preserve access in case one of the channels is detected.
Kaspersky Lab warns that to protect organizational infrastructures, it is necessary to add the resources and IP addresses of cloud services that provide traffic tunneling to the firewall’s blocklist. It is also recommended not to store passwords in browsers to prevent hackers from accessing sensitive information.





