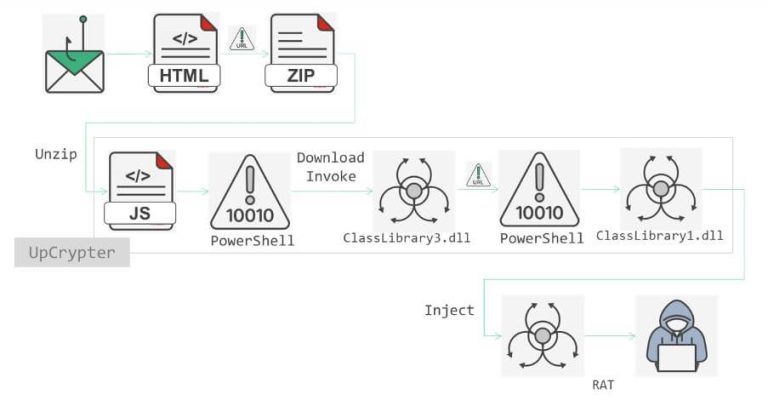
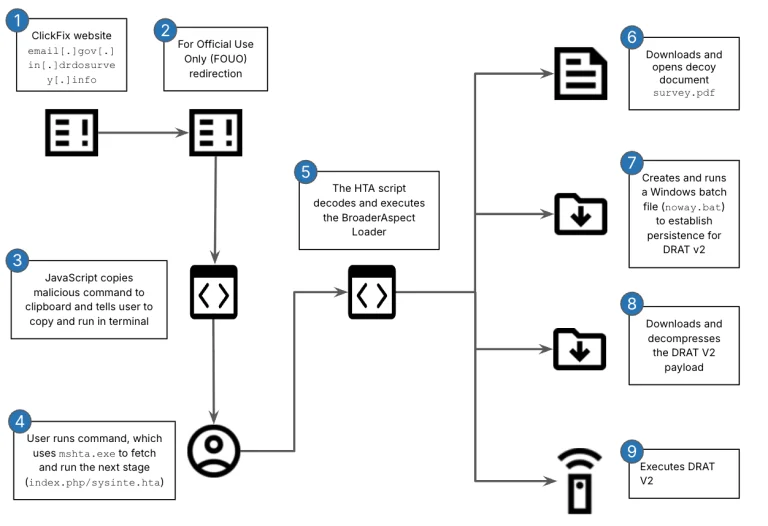
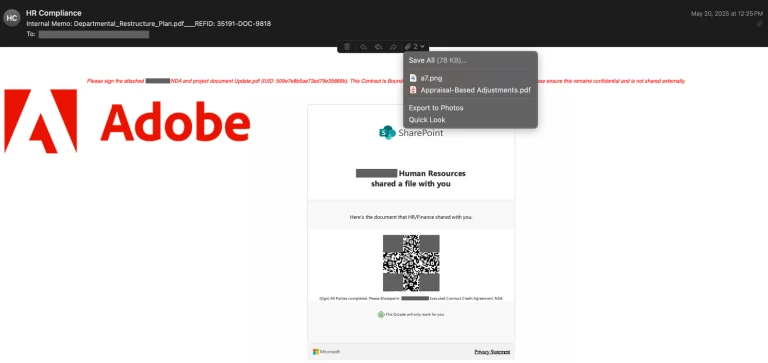
In early August 2025, specialists at Fortinet FortiGuard Labs detected a large-scale phishing campaign distributing the UpCrypter...
Remote Access Trojan
The hacking collective APT-C-08, also known as TA397 and Bitter, continues to expand its cyber arsenal. Chinese...
Experts at Kaspersky Lab have uncovered a new remote access trojan, GodRAT, which is being distributed through...
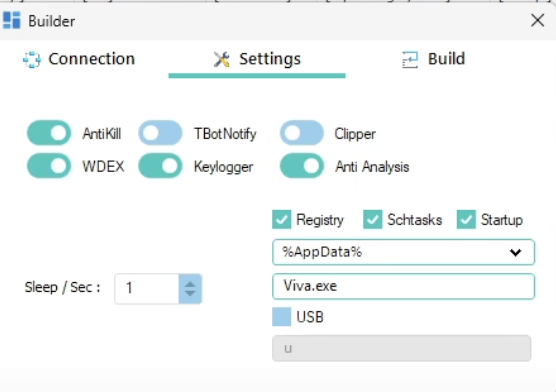
A new wave of attacks leveraging the XWorm malware vividly illustrates how far threat actors have advanced...
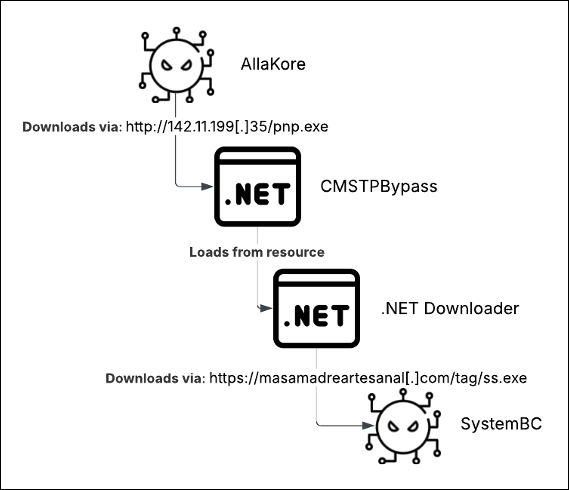
Mexican organizations remain the persistent targets of an enduring cybercriminal campaign involving modified versions of the AllaKore...
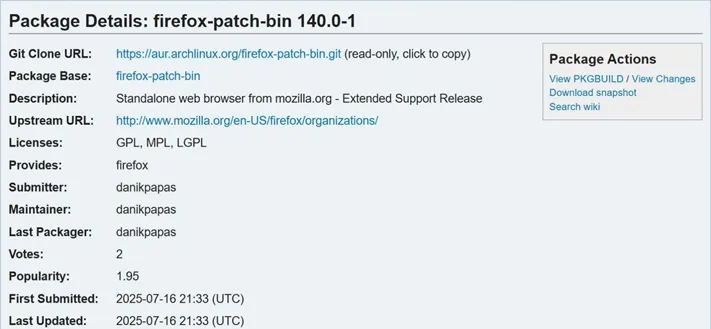
Three malicious scripts have been discovered in the Arch User Repository (AUR)—a community-driven repository for Arch Linux...
AsyncRAT, first introduced on GitHub in January 2019, has evolved into one of the most formidable tools...
A hacker group with affiliations beyond Pakistan has once again drawn attention following its attacks on Indian...
In recent months, cybersecurity experts have observed a dramatic surge in the malicious exploitation of domains within...
Telephone-based fraud schemes masquerading as customer support from well-known brands are rapidly gaining traction among cybercriminals. According...
Cybercriminals have launched a new wave of attacks targeting WordPress websites—so meticulously concealed that the campaign was...