Software Devs Targeted: DEV#POPPER Campaign in Disguise
Researchers have uncovered a hacking campaign known as DEV#POPPER, targeting software developers. The perpetrators disguise themselves as employers and distribute fictitious job offers to IT specialists. Their true intent is to implant a dangerous Python-based Remote Access Trojan (RAT) onto the victims’ computers. During the ostensible interview process, candidates are asked to complete a “test task” – to download and execute code from a repository on GitHub.
The attack unfolds in several stages, employing social engineering techniques to progressively compromise the system. Initially, candidates are prompted to download a ZIP archive containing an auxiliary NPM package with a README.md file and separate folders for client and server code.
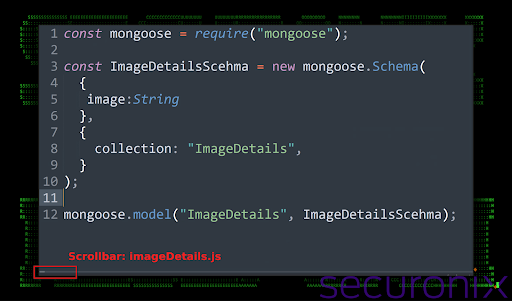
Subsequently, a disguised JavaScript file, imageDetails.js, in the backend directory is activated. Through Node.js, it executes curl commands to download an additional encrypted archive, p.zi, from an external server.
Inside the p.zi archive lies the main component of the attack – a convoluted Python script named npl, which is the RAT itself. Once the RAT is installed on the infected machine, it collects basic information: operating system type, host name, network data, which are then transmitted to the attackers’ server.
In addition to data collection, the trojan boasts a wide range of functionalities:
- Maintaining a stable communication channel for remote management of the compromised system
- Commands for detecting and extracting desired files from the file system
- Capability to remotely execute malicious code
- Direct transmission of data from critical folders such as “Documents” and “Downloads” via FTP from the victim
- Intercepting keystrokes and clipboard data to steal credentials
Analysts from Securonix assess that the tactics of the DEV#POPPER campaign are highly likely to be employed by hacking groups from North Korea, known for their use of social engineering techniques. However, there is insufficient evidence to directly accuse the North Korean authorities of these attacks.
Experts emphasize that the perpetrators skillfully exploit the trust IT specialists place in the employment process. The reluctance to miss out on a potential job opportunity due to non-compliance with the instructions of a fictitious employer makes the attack exceptionally effective.





